
An affiliate of the Mallox ransomware operation, often known as TargetCompany, was noticed utilizing a barely modified model of the Kryptina ransomware to assault Linux techniques.
This model, based on SentinelLabs, is separate from different Linux-targeting variants of Mallox, such because the one described final June by Development Micro researchers, highlighting the shifting techniques of the ransomware ecosystem.
Additionally, that is one other signal that Mallox, beforehand a Home windows-only malware, is placing Linux and VMWare ESXi techniques into its crosshairs, marking a major evolution for the operation.
From Kryptina to Mallox
Kryptina was launched as a low-cost ($500-$800) ransomware-as-a-service (RaaS) platform for focusing on Linux techniques in late 2023 however failed to realize traction within the cybercrime group.
In February 2024, its purported administrator, utilizing the alias “Corlys,” leaked Kryptina’s supply code free of charge on hacking boards, which was presumably acquired by random ransomware actors thinking about getting their fingers on a working Linux variant.
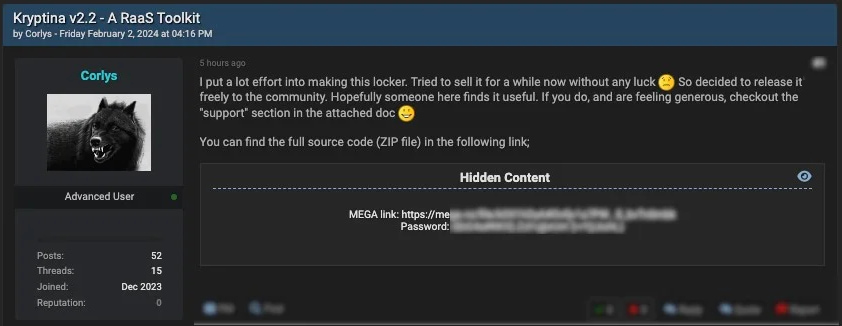
Supply: SentinelLabs
After a Mallox affiliate suffered an operational error and uncovered their instruments, SentinelLabs found that Kryptina had been adopted by the challenge and its supply code was used for constructing rebranded Mallox payloads.
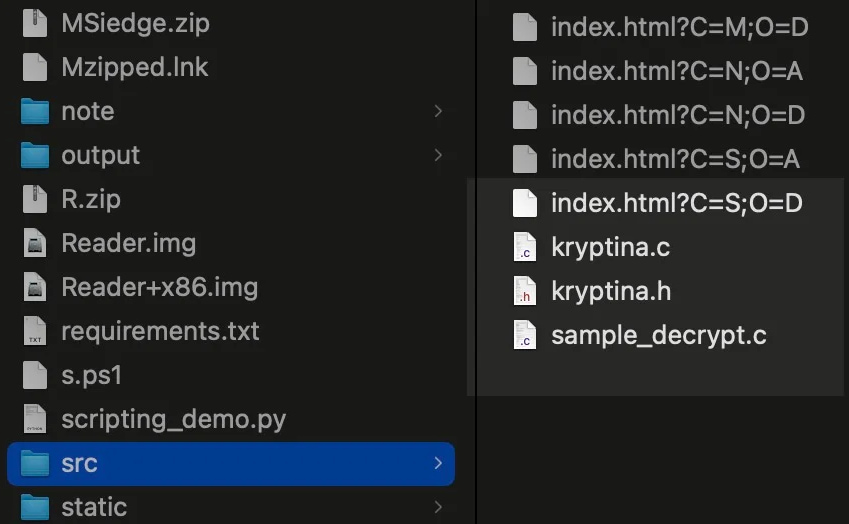
Supply: SentinelLabs
The rebranded encryptor, named “Mallox Linux 1.0,” makes use of Kryptina’s core supply code, the identical AES-256-CBC encryption mechanism and decryption routines, and in addition the identical command-line builder and configuration parameters.
This means that the Mallox affiliate solely modified the looks and title, eliminated references to Kryptina on ransom notes, scripts, and information, and transposed the present documentation right into a “lite” type, leaving all the remaining unchanged.
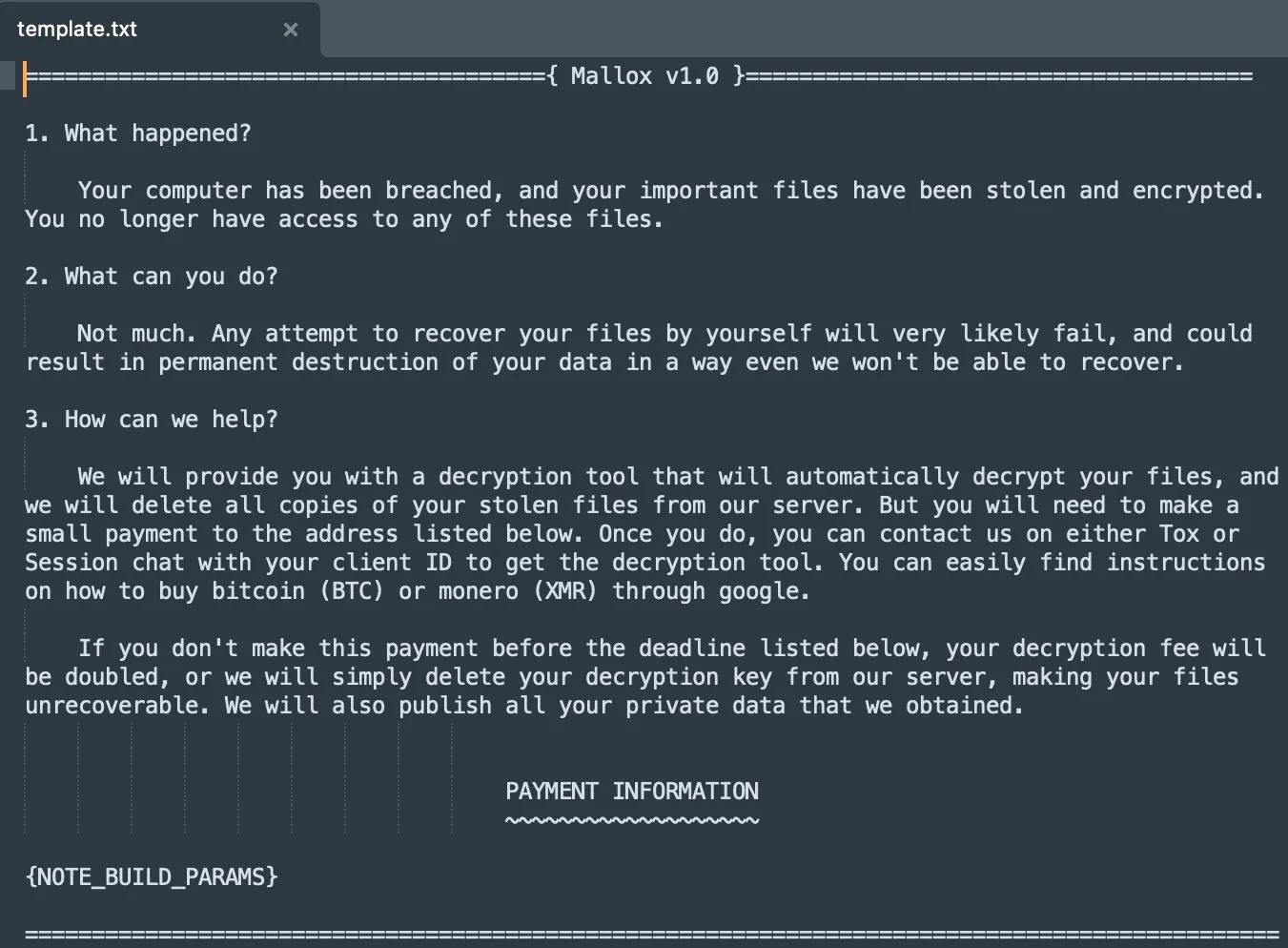
Supply: SentinelLabs
Aside from Mallox Linux 1.0, SentinelLabs discovered varied different instruments on the risk actor’s server, together with:
- A respectable Kaspersky password reset instrument (KLAPR.BAT)
- An exploit for CVE-2024-21338, a privilege escalation flaw on Home windows 10 and 11
- Privilege escalation PowerShell scripts
- Java-based Mallox payload droppers
- Disk picture information containing Mallox payloads
- Information folders for 14 potential victims
At the moment, it stays unsure whether or not the Mallox Linux 1.0 variant is being utilized by a single affiliate, a number of associates, or all Mallox ransomware operators alongside the Linux variant mentioned in our earlier report.