.jpg)
A brand new model of the Necro Trojan malware for Android was put in on 11 million units by means of Google Play in malicious SDK provide chain assaults.
This new model of the Necro Trojan was put in by means of malicious promoting software program growth kits (SDK) utilized by official apps, Android sport mods, and modified variations of standard software program, corresponding to Spotify, WhatsApp, and Minecraft.
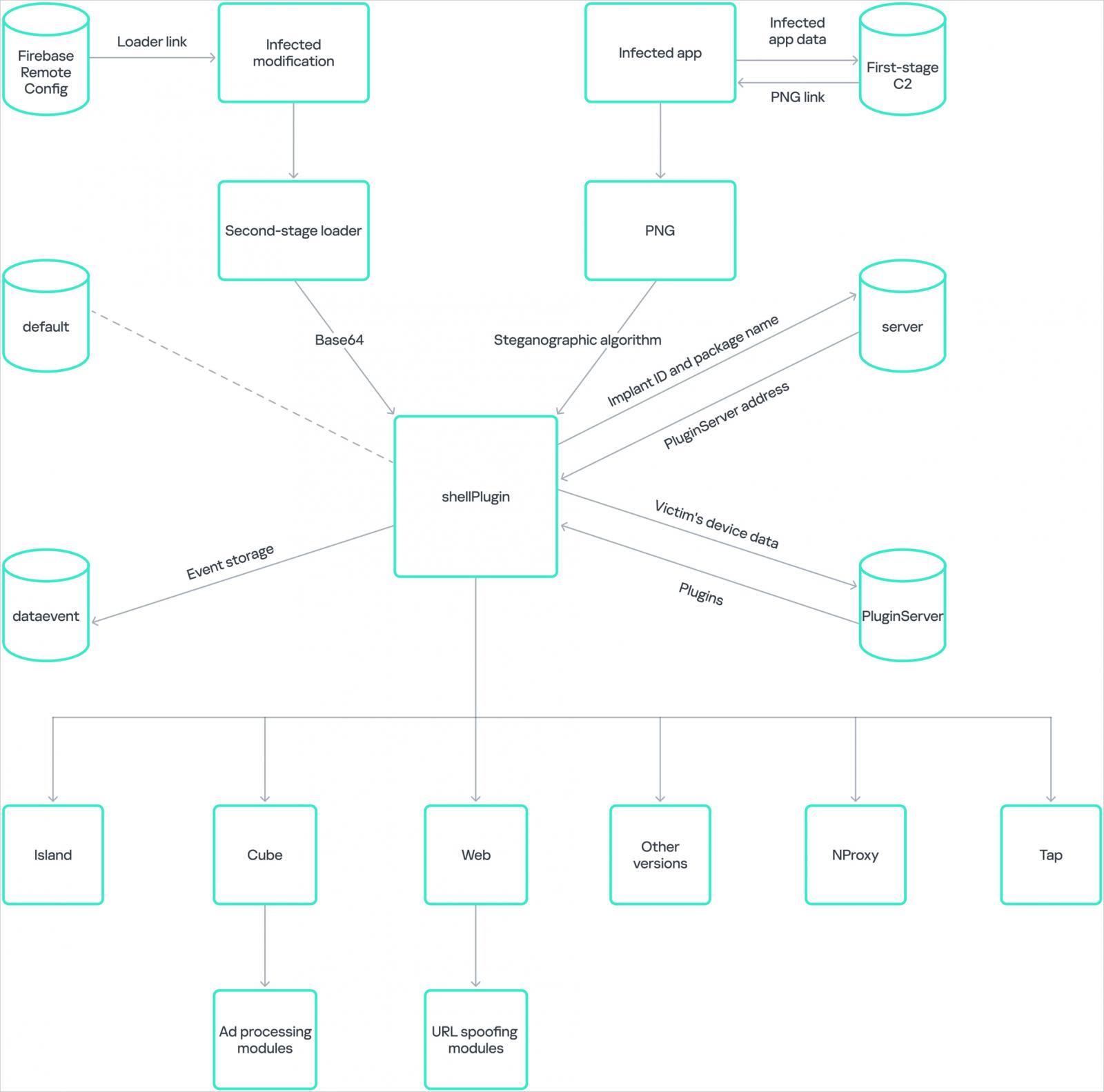
Necro installs a number of payloads to contaminated units and prompts numerous malicious plugins, together with:
- Adware that hundreds hyperlinks by means of invisible WebView home windows (Island plugin, Dice SDK)
- Modules that obtain and execute arbitrary JavaScript and DEX information (Blissful SDK, Jar SDK)
- Instruments particularly designed to facilitate subscription fraud (Net plugin, Blissful SDK, Faucet plugin)
- Mechanisms that use contaminated units as proxies to route malicious visitors (NProxy plugin)
Necro Trojan on Google Play
Kaspersky found the presence of Necro loader on two apps on Google Play, each of which have a considerable userbase.
The primary one is Wuta Digicam by ‘Benqu,’ a photograph enhancing and beautification instrument with over 10,000,000 downloads on Google Play.
Supply: BleepingComputer
The risk analysts report that Necro appeared on the app with the discharge of model 6.3.2.148, and it remained embedded till model 6.3.6.148, which is when Kaspersky notified Google.
Whereas the trojan was eliminated in model 6.3.7.138, any payloads which may have been put in through the older variations may nonetheless lurk on Android units.
The second official app that carried Necro is Max Browser by ‘WA message recover-wamr,’ which had 1 million downloads on Google Play till it was eliminated, following Kaspersky’s report.
Kaspersky claims that Max Browser’s newest model, 1.2.0, nonetheless carries Necro, so there isn’t any clear model out there to improve to, and customers of the net browser are really helpful to uninstall it instantly and change to a special browser.
Kaspersky says the 2 apps had been contaminated by an promoting SDK named ‘Coral SDK,’ which employed obfuscation to cover its malicious actions and likewise picture steganography to obtain the second-stage payload, shellPlugin, disguised as innocent PNG photographs.
Supply: Kaspersky
Google informed BleepingComputer they had been conscious of the reported apps and had been investigating them.
Outdoors official sources
Outdoors the Play Retailer, the Necro Trojan is unfold primarily by means of modified variations of standard apps (mods) that had been distributed through unofficial web sites.
Notable examples noticed by Kaspersky embrace WhatsApp mods ‘GBWhatsApp’ and ‘FMWhatsApp,’ which promise higher privateness controls and prolonged file-sharing limits. One other is the Spotify mod, ‘Spotify Plus,’ which guarantees free entry to ad-free premium providers.
Supply: Kaspersky
The report additionally mentions Minecraft mods and mods for different standard video games like Stumble Guys, Automobile Parking Multiplayer, and Melon Sandbox, which had been contaminated with the Necro loader.
In all instances, the malicious habits was the identical—displaying adverts within the background to generate fraudulent income for the attackers, putting in apps and APKs with out the consumer’s consent, and utilizing invisible WebViews to work together with paid providers.
As unofficial Android software program web sites don’t report obtain numbers reliably, the entire variety of infections by this newest Necro Trojan wave is unknown, however it’s a minimum of 11 million from Google Play.