
The RansomHub ransomware gang is behind the latest cyberattack on oil and fuel companies large Halliburton, which disrupted the corporate’s IT programs and enterprise operations.
The assault brought about widespread disruption, and BleepingComputer was instructed that clients could not generate invoices or buy orders as a result of the required programs had been down.
Halliburton disclosed the assault final Friday in an SEC submitting, stating they suffered a cyberattack on August 21, 2024, by an unauthorized occasion.
“On August 21, 2024, Halliburton Firm (the “Firm”) turned conscious that an unauthorized third occasion gained entry to sure of its programs,” learn Halliburton’s SEC submitting.
“When the Firm realized of the difficulty, the Firm activated its cybersecurity response plan and launched an investigation internally with the help of exterior advisors to evaluate and remediate the unauthorized exercise.”
The corporate supplies a quite a few companies to grease and fuel corporations, together with nicely development, drilling, hydraulic fracturing (fracking), and IT software program and companies. Because of the firm’s big selection of companies, there’s quite a lot of connectivity between them and their clients.
Nonetheless, the corporate has not shared many particulars in regards to the assault, with a buyer within the oil and fuel trade telling BleepingComputer that they’ve been left at midnight about figuring out if the assault impacted them and the way to defend themselves.
This has brought about different clients to disconnect from Halliburton as a result of lack of understanding being shared.
BleepingComputer has additionally been instructed that some corporations are working with ONG-ISAC—an company that acts as a central level of coordination and communication for bodily and cybersecurity threats towards the oil and fuel trade—to obtain technical details about the assault to find out in the event that they had been breached as nicely.
RansomHub ransomware behind the assault
For days, there have been rumors that Halliburton suffered a RansomHub ransomware assault, with customers claiming this on Reddit and on the job layoff dialogue web site, TheLayoff, the place a partial RansomHub ransom notice was printed.
When BleepingComputer contacted Halliburton about these claims, Halliburton mentioned they weren’t making any additional feedback.
“We aren’t commenting past what was included in our submitting. Any subsequent communications will probably be within the type of an 8-Ok,” Halliburton instructed BleepingComputer.
Nonetheless, in an August 26 electronic mail despatched to suppliers and shared with BleepingComputer, Halliburton supplied extra data stating that the corporate took programs offline to guard them and is working with Mandiant to analyze the incident.
“We’re reaching out to replace you a few cybersecurity subject affecting Halliburton,” reads the letter seen by BleepingComputer.
“As quickly as we realized of the difficulty, we activated our cybersecurity response plan and took steps to deal with it, together with (1) proactively taking sure programs offline to assist defend them, (2) participating the help of main exterior advisors, together with Mandiant, and (3) notifying legislation enforcement.”
Additionally they acknowledged that their electronic mail programs proceed to function as they’re hosted on Microsoft Azure infrastructure. A workaround can be accessible for transacting and issuing buy orders.
This electronic mail features a record of IOCs containing file names and IP addresses related to the assault that clients can use to detect comparable exercise on their community.
One in every of these IOCs is for a Home windows executable named upkeep.exe, which BleepingComputer has confirmed to be a RansomHub ransomware encryptor.
After analyzing the pattern, it seems to be a more moderen model than beforehand analyzed, because it comprises a brand new “-cmd string” command-line argument, which is able to execute a command on the machine earlier than encrypting information.
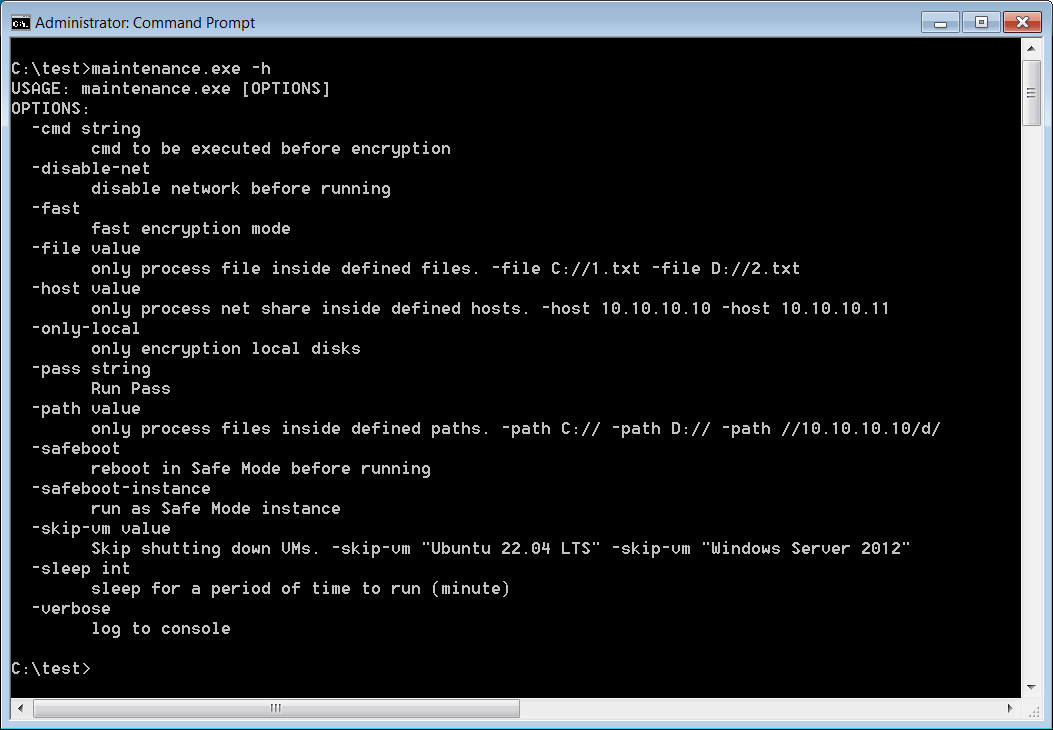
Supply: BleepingComputer
RansomHub
The RansomHub ransomware operation launched in February 2024, claiming it was an information theft extortion and extortion group that offered stolen information to the best bidder.
Nonetheless, quickly after, it was found that the operation additionally utilized ransomware encryptors in its double-extortion assaults, the place the menace actors breached networks, stole information, after which encrypted information.
The encrypted information and the menace to leak stolen information had been then used as leverage to scare corporations into paying a ransom.
Symantec analyzed the ransomware encryptors and reported that they had been based mostly on the Knight ransomware encryptors, previously referred to as Cyclops.
The Knight operation claimed they offered their supply code in February 2024 and shut down simply as RansomHub launched. This has made many researchers imagine that RansomHub is a rebrand of the Knight ransomware operation.
Right now, the FBI launched an advisory about RansomHub, sharing the menace actor’s ways and warning that they breached no less than 210 victims since February.
It’s common for the FBI and CISA to publish coordinated advisories on menace actors quickly after they conduct a extremely impactful assault on important infrastructure, comparable to Halliburton. Nonetheless, it’s not recognized if the advisory and the assault are linked.
For the reason that begin of the yr, RansomHub has been liable for quite a few high-profile assaults, together with these on American not-for-profit credit score union Patelco, the Ceremony Support drugstore chain, the Christie’s public sale home, and U.S. telecom supplier Frontier Communications.
The ransomware operation’s information leak web site was additionally utilized to leak stolen information belonging to Change Healthcare following the shutdown of the BlackCat and ALPHV ransomware operation.
It’s believed that after BlackCat shut down, a few of its associates moved to RansomHub, permitting them to rapidly escalate their assaults with skilled ransomware menace actors.