
The South Korea-aligned cyberespionage group APT-C-60 has been leveraging a zero-day code execution vulnerability within the Home windows model of WPS Workplace to put in the SpyGlace backdoor on East Asian targets.
WPS Workplace is a productiveness suite developed by the Chinese language agency Kingsoft that’s well-liked in Asia. Reportedly, it has over 500 million energetic customers worldwide.
The zero-day flaw, tracked as CVE-2024-7262, has been leveraged in assaults within the wild since a minimum of late February 2024, however impacts variations from 12.2.0.13110 (August 2023) to 12.1.0.16412 (March 2024).
Kingsoft “silently” patched the issue in March this yr with out informing the purchasers that the flaw was actively exploited, prompting ESET, who found the marketing campaign and vulnerability, to publish an in depth report right now.
Along with CVE-2024-7262, ESET’s investigation unveiled a second extreme flaw, tracked as CVE-2024-7263, which Kingsoft patched in late Could 2024 with model 12.2.0.17119.
APT-C-60 exploitation
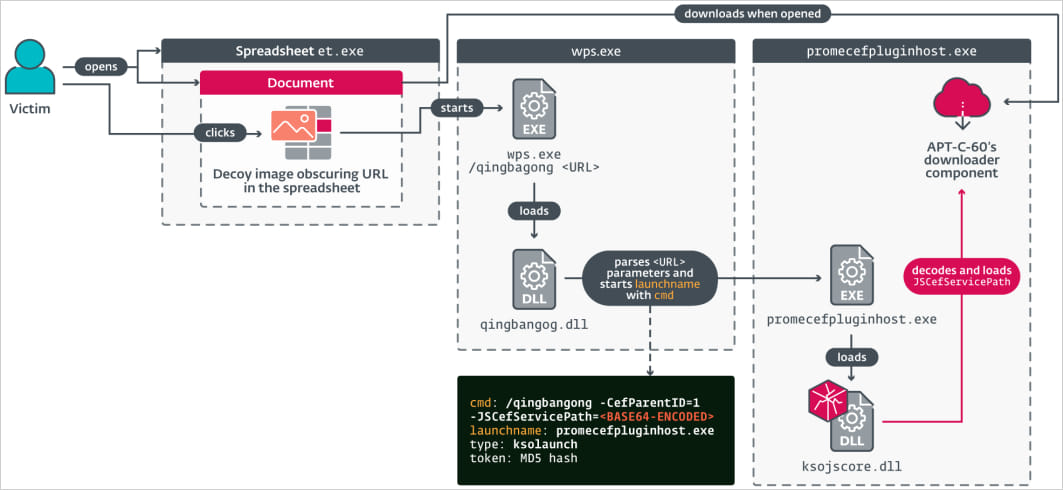
CVE-2024-7262 resides in how the software program handles customized protocol handlers, particularly ‘ksoqing://,’ which permits the execution of exterior purposes by means of specifically crafted URLs inside paperwork.
Resulting from improper validation and sanitization of those URLs, the flaw permits attackers to craft malicious hyperlinks that result in arbitrary code execution.
APT-C-60 created spreadsheet paperwork (MHTML information) the place they embedded malicious hyperlinks hidden underneath a decoy picture to trick the sufferer into clicking them, triggering the exploit.
The processed URL parameters embody a base64-encoded command to execute a selected plugin (promecefpluginhost.exe) that makes an attempt to load a malicious DLL (ksojscore.dll) containing the attacker’s code.
This DLL is APT-C-60’s downloader element, designed for fetching the ultimate payload (TaskControler.dll) from the attacker’s server, a customized backdoor named ‘SpyGlace.’
Supply: ESET
SpyGlace is a backdoor beforehand analyzed by Threatbook when APT-C-60 used it in assaults on human assets and trade-related organizations.
Dangerous patch leaves hole
Whereas investigating APT-C-60’s assaults, ESET’s researchers found CVE-2024-7263, a second arbitrary code execution flaw impacting WPS Workplace, which emerged as an incomplete patch of CVE-2024-7262.
Particularly, Kingsoft’s preliminary try to handle the issue added validation on particular parameters. Nevertheless, some, just like the ‘CefPluginPathU8,’ have been nonetheless not adequately secured, permitting attackers to level to paths of malicious DLLs by means of promecefpluginhost.exe once more.
ESET explains that this vulnerability might be exploited domestically or by means of a community share, the place the malicious DLL may very well be hosted.
Regardless of this chance, the researchers didn’t observe APT-C-60 or another actors leveraging the flaw within the wild. Nevertheless, given sufficient time, it isn’t unlikely they’d have found the safety hole left by Kingsoft’s dangerous patch.
Customers of WPS Workplace are advisable to maneuver to the newest launch as quickly as doable, or a minimum of 12.2.0.17119, to handle each code execution flaws.
“The exploit is crafty as it’s misleading sufficient to trick any consumer into clicking on a legitimate-looking spreadsheet whereas additionally being very efficient and dependable,” warns ESET within the report.
“The selection of the MHTML file format allowed the attackers to show a code execution vulnerability right into a distant one.”
Test this GitHub repository for a whole record of indicators of compromise (IoCs) related to the APT-C-60 exercise.