Up to now 12 months alone, now we have reported nearly 5 hundred distinctive malvertising incidents associated to Google search adverts. Whereas it may be troublesome to attribute every incident to a selected menace actor, we often discover similarities between campaigns.
Some malvertisers go to nice lengths to bypass safety controls, whereas others know they may get caught and are keen to burn their accounts and infrastructure. Having mentioned that, now we have typically noticed stealthier assaults and the one we’re protecting on this weblog is one among them.
Focusing on the favored communication device Slack, a menace actor is counting on a number of on-line instruments to slender down their victims’ listing and most significantly evade detection.
Context is every part
For a number of days we seen a suspicious advert for Slack that appeared while you googled the search time period for it. The advert really seems to be fairly reliable and is listed above the natural search end result for the official website. Regardless of its look, we knew it was doubtless malicious, though clicking on it on the time would solely lead to being redirected to slack.com.

Virtually each Google advert accommodates further details about its advertiser and why it was exhibited to you. That is accessible by clicking on the three dots beside the advert URL and it brings you to the Google Adverts Transparency Middle.
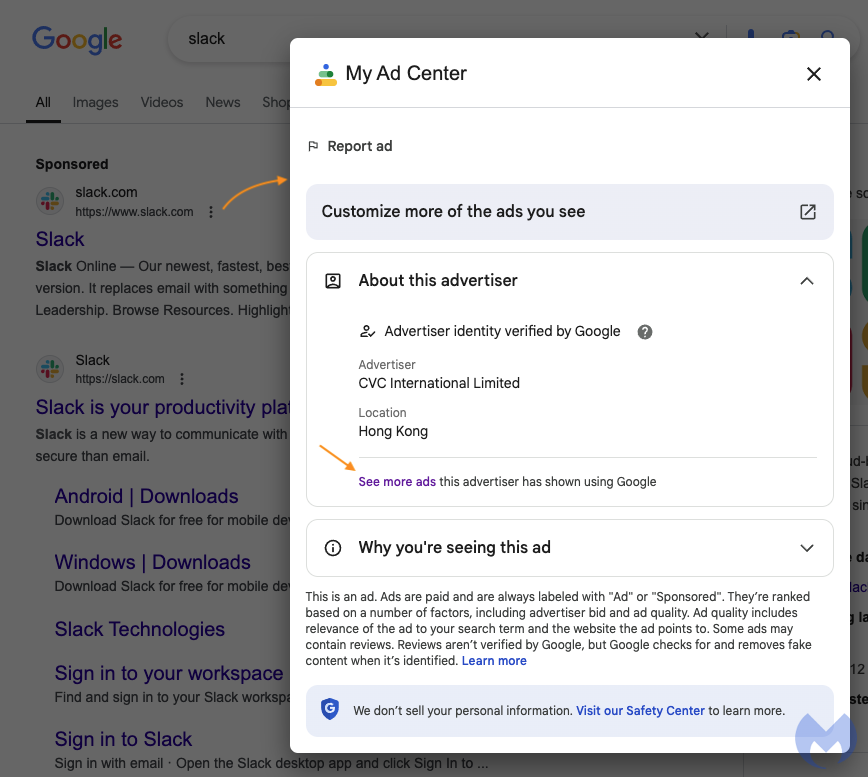
What we discover is that this advertiser is selling merchandise that look focused on the Asian market, after which there’s this Slack advert that seems in the midst of nowhere.

We’ve talked about earlier than how contextualized detection could possibly be a great way to determine an advertiser account that has been compromised. We don’t know whether or not Google’s algorithms are skilled on this or not, but it surely has definitely helped us many instances up to now to search out new malicious advert campaigns.
Gradual cooking
For days, clicking on this Slack advert would solely redirect to a value web page on Slack’s official web site. Adverts aren’t at all times weaponized immediately; in truth it’s a frequent follow for menace actors to let their advert ‘prepare dinner’ such that it doesn’t instantly turn out to be detected.

Ultimately, we noticed a change in habits. Moderately than redirecting to slack.com, now the advert first began redirecting to a click on tracker. This is likely one of the weaknesses within the Google advert ecosystem as such companies will be abused to filter clicks and basically ship site visitors to a site of anybody’s selecting. Monitoring templates as they’re identified, are a built-in function that has turn out to be synonym with fraud for us.
Taking part in video games of conceal and search
Now the advert’s remaining URL had turn out to be slack-windows-download[.]com an fascinating selection for a site title created lower than per week in the past. Whereas it’s apparent that this web page was mechanically generated, maybe utilizing AI, there may be nothing malicious on it. For no matter motive, the server aspect checks decided that we should always solely be seeing this decoy web page on the time:
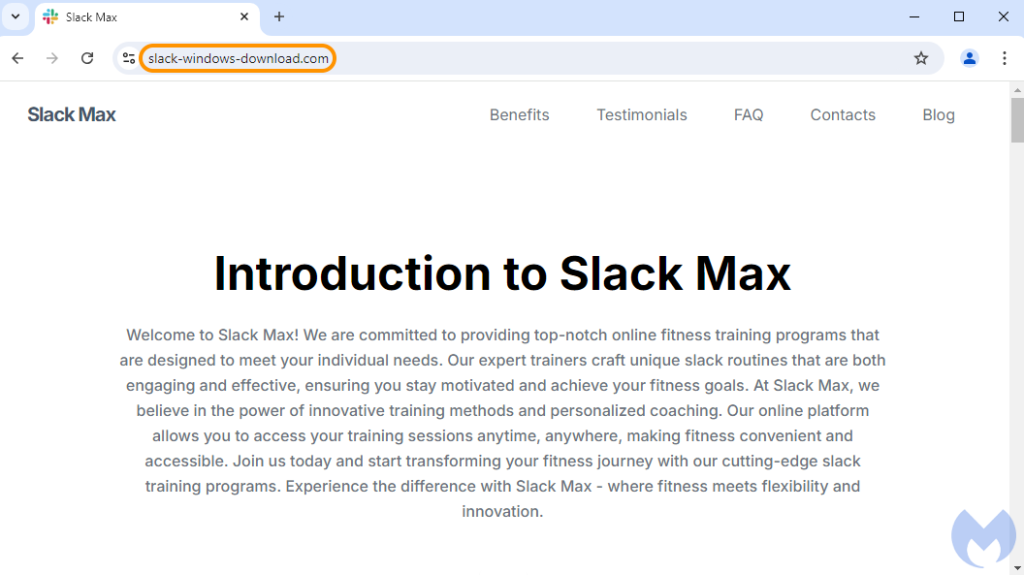
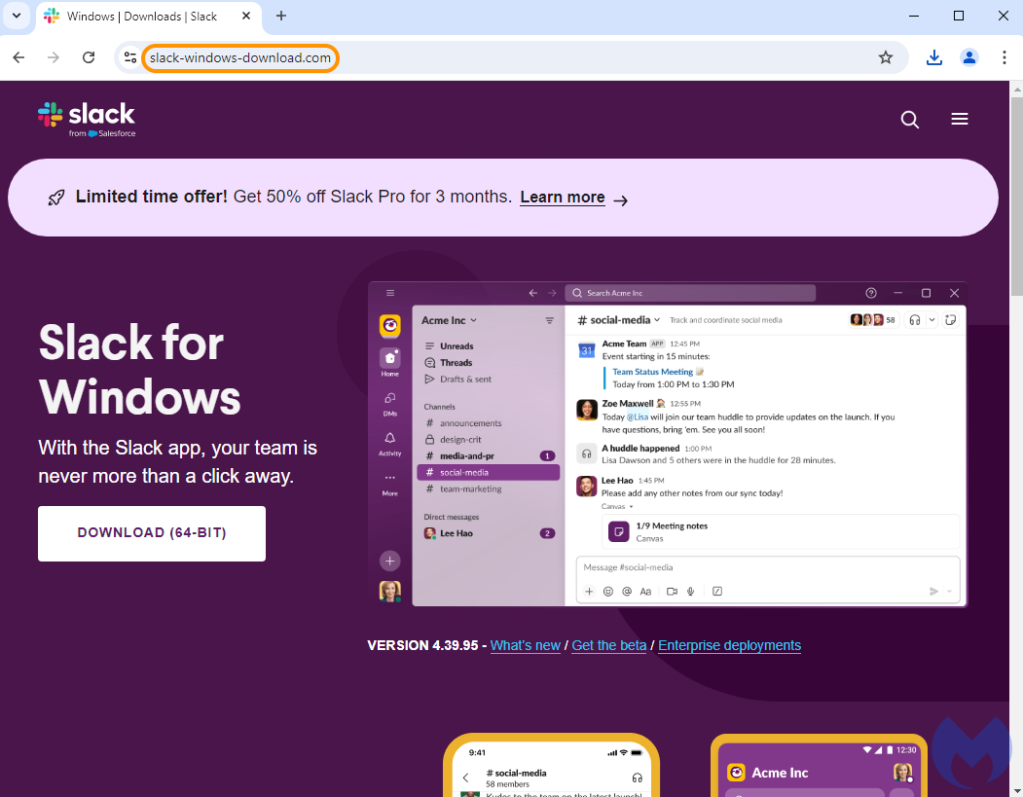
After tweaking numerous settings, we lastly noticed the malicious web page, meant to impersonate Slack and provide a obtain hyperlink to unsuspecting victims. It’s the similar area because the one above, however the content material is totally totally different. That sort of habits is called cloaking, the place totally different customers are proven totally different content material:
Beneath is a community site visitors seize exhibiting what was required to get to this web page. There are some things price noting:
- The Google advert URL redirects to a click on fraud detection device, adopted by a click on tracker. There isn’t a means for Google to know the place customers are going at this level.
- The press trackers themselves are blinded on what occurs subsequent, due to a singular hyperlink/monitoring hyperlink adopted by another cloaking area.

This deep layering makes it extremely troublesome to guage an advert with out resorting to particular tooling and data of the menace actors’ TTPs.
Malware payload
The obtain button triggers a file obtain from one other area which will trace at a parallel marketing campaign concentrating on Zoom. A secret’s handed to the server to request the malware binary to customers who went by the supply chain.
Dynamic evaluation in a sandbox reveals a distant connection to 45.141.87[.]218, a server beforehand utilized by SecTopRAT, a distant entry Trojan with stealer capabilities. This payload was beforehand dropped in different malvertising chains, one among them impersonating NordVPN.
Conclusion
Malwarebytes was already blocking that command and management server and we’ve improved our detection protection by including the supporting and supply infrastructure used on this marketing campaign. As well as, we’ve reported the malicious advert to Google and Cloudflare has now flagged the decoy domains that have been abusing its companies, as phishing.
We anticipate malvertisers to proceed to use free and paid platforms to assist them keep away from detection, however we additionally must be conscious that they could be extra affected person and await the fitting second to unleash a brand new marketing campaign.
Indicators of Compromise
Hyperlink redirect
slacklink[.]sng[.]hyperlink
Cloaking
haiersi[.]com
Decoy websites
slack-windows-download[.]com
slack-download-for-windows[.]com
Payload obtain
zoom2024[.]on-line
Payload SHA256
59e5e07ffa53ad721bc6b4c2ef435e08ae5b1286cda51415303978da474032d2