Scams
Your cellphone quantity is greater than only a technique to contact you – scammers can use it to focus on you with malicious messages and even exploit it to realize entry to your checking account or steal company information
13 Aug 2024
•
,
5 min. learn

Final month, we checked out how scammers can acquire entry to your cellphone quantity and the way information breaches and phishing campaigns might make acquiring it simple. On this blogpost, we’ll focus extra on why cellphone numbers are precious targets and focus on the dangers related to their compromise.
The $cam business
On-line scammers proceed to rake in staggering earnings from all kinds of fraudulent schemes. Lately, many such schemes have been orchestrated by legal syndicates that run rip-off compounds in Southeast Asia, the place trafficked people are coerced into executing elaborate ploys, corresponding to pig butchering.
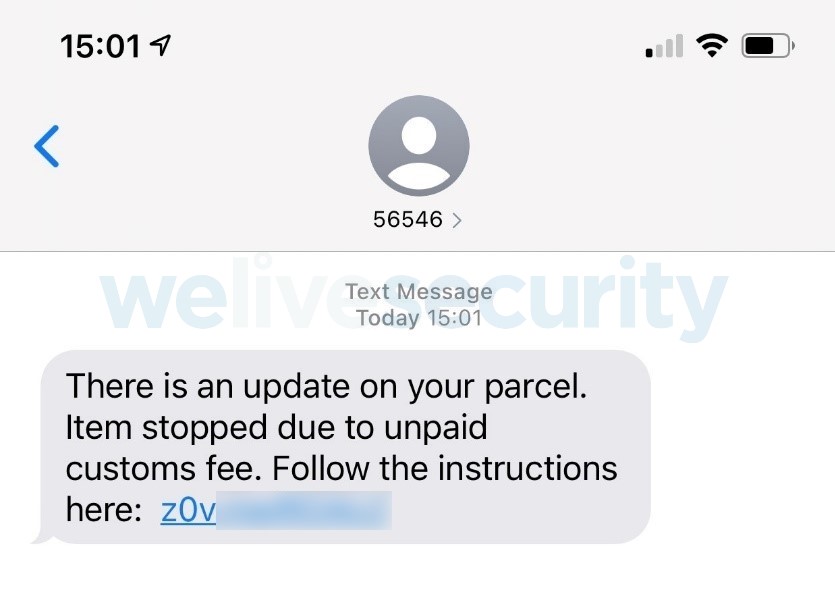
Aside from constructing pretend on-line relationships, the ways of many on-line fraudsters typically contain creating situations that demand pressing motion or depend on different ruses, together with purported financial institution or PayPal account takeovers, gadgets compromised with malware, failed package deal deliveries, and even kidnapped kinfolk and different schemes leveraging synthetic intelligence (AI).
On the coronary heart of many on-line fraud schemes is phishing and different social engineering assaults. Their success lies largely of their low-cost/high-reward nature, scalability, skill to exploit human weaknesses, in addition to the challenges of cross-border regulation enforcement. To high it off, it might take one profitable “phish” to repay the whole operation.
Throw me some numbers
Let’s now take a look at how cellphone numbers match into this, why they’re, along with account login credentials, so precious to scammers, and the way they are often leveraged for malicious ends.
Smishing and hacking
For starters, risk actors might goal you with malware disguised as benign hyperlinks or attachments that may, nonetheless, set up spy ware or different malware in your machine or exfiltrate your private information from it. Alternatively, they’ll ship you messages that goal to trick you into surrendering your login credentials or different private data on phishing web sites.
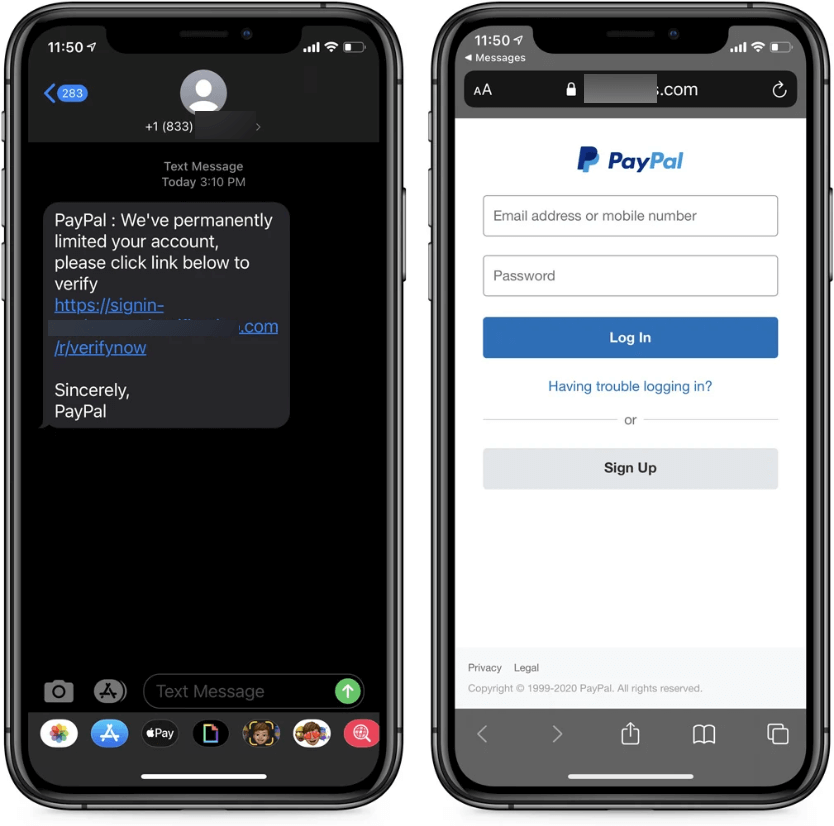
For instance, ESET Menace Report H1 2024 highlighted the proliferation of GoldPickaxe malware that in its iOS iteration employs a multistage social engineering scheme that persuades victims to put in a Cell Machine Administration profile, giving risk actors full management over the sufferer’s cellphone.
Name forwarding, SIM swaps and Caller ID spoofing
Regardless of the rise of digital communication, cellphone calls and messages stay a trusted technique for exchanging confidential data.
- In name forwarding schemes, scammers contact you or your service supplier and finally have cellphone calls forwarded out of your cellphone quantity to a quantity underneath their management. Whereas the supplier may ask for verification, the scammer might have already got entry to extra of your private particulars (from information leaks or public sources), making this rip-off simple to carry out.
- Equally, SIM swapping fraudsters can trick your cell provider into activating their SIM card underneath your identify/outdated quantity, successfully porting your quantity to their SIM card. This rip-off is “louder” than name forwarding mainly since you lose entry to your cellphone community because of this. Whereas additionally requiring some analysis into the sufferer’s life for the verification course of, SIM swapping has been a severe risk for years.
- Scammers can spoof their Caller ID by impersonating your quantity, utilizing Voice over Web Protocol (VoIP) or spoofing providers, and different strategies. Because of this, attackers might masks their id whereas committing monetary scams and different crimes and pretending to be you or your trusted contact.
Why are all these scams such a risk? Nowadays, many on-line providers depend on cellphone numbers for authentication and account restoration. Compromising a cellphone quantity can, due to this fact, be tantamount to bypassing your safety safeguards, together with two-factor authentication (2FA). Moreover, scammers might impersonate you to defraud your contacts – or your employer.
Phishing for company information
Nowadays, many staff use private or firm telephones to examine their company emails or messages. This creates a notable vector for assaults, as computer systems are not the only real entry factors for tried compromise. Scammers might impersonate enterprise executives or accounting departments to request cash transfers for “enterprise” functions.
Certainly, the final word objective for a lot of scammers is to realize entry to company techniques and funds. The human ingredient performs a vital position in these schemes, too. We frequently don’t confirm the legitimacy of requests earlier than complying with them, making it simple for phishing assaults to succeed and finally leading to substantial monetary injury to companies.
CEO fraud
For example, think about being an accountant at a big monetary firm. You’re enjoying round with Excel while you obtain a cellphone name, seemingly out of your boss, asking you to wire over cash for a enterprise deal whose success hinges in your immediate motion. Such scams are fairly actual. Because the name seems to come back out of your boss’s quantity, you might not query its legitimacy – and also you wouldn’t be alone.
The information runs crimson with mentions of this “CEO fraud”, a subset of enterprise e-mail compromise (BEC) fraud. At this time, such scams are supercharged by AI, with risk actors utilizing voice cloning to raised impersonate somebody (in case caller ID spoofing wasn’t sufficient).
So, what to do in such harmful occasions?
Elevating the protection internet
Fortunately, there are a number of methods folks and companies can keep freed from cellphone scams:
- Validate: By no means reply or work together with unknown callers/senders, and everytime you obtain a request for private information from a “trusted” entity, name them first and ask whether or not the request you obtained was real.
- Attain out to your service supplier: To stop forwarding or SIM swaps, ask your service supplier to safe your account towards undesirable adjustments with extra safety components like SIM locks to forestall swapping or extra complete verification checks.
- Thoughts what you share: To stop scams from gathering extra information on you, thoughts what you share about your self on-line. Impersonation depends on presenting oneself as somebody , so attempt to restrict your public publicity.
- Overlook SMS: To stop fraud, defend your accounts with app-based two-factor authentication as an alternative of SMS-based one. The latter will be simply intercepted and let crooks to compromise your accounts with ease.
- Use cell safety: Phishing, both by messages or calls, will be detected by robust cell safety software program. For companies, cell risk protection and safe authentication might help overcome such threats.
To conclude, since a cellphone quantity could be a doorway for risk actors and result in large-scale enterprise compromise and thousands and thousands in injury. It must be saved as non-public as doable – identical to some other distinctive identifier, in any case.
As phishing stays a serious risk, keep vigilant and keep in mind: validation and authentication are your keys to staying safe!
Within the meantime, why not check your phish-spotting prowess in our fast quiz?
