
A sequence of focused cyberattacks that began on the finish of July 2024, focusing on dozens of methods utilized in Russian authorities organizations and IT corporations, are linked to Chinese language hackers of the APT31 and APT 27 teams.
Kaspersky, who found the exercise, dubbed the marketing campaign “EastWind,” reporting that it employs an up to date model of the CloudSorcerer backdoor noticed in an identical cyberespionage marketing campaign from Could 2024, additionally focusing on Russian authorities entities.
It must be famous that the CloudSorcerer exercise is not sure to Russia, as Proofpoint recorded an assault focusing on a U.S.-based assume tank in Could 2024.
EastWind toolkit
The preliminary an infection depends on phishing emails carrying RAR archive attachments named after the goal, which make use of DLL facet loading to drop a backdoor on the system from Dropbox whereas opening a doc for deception.
The backdoor can navigate the filesystem, execute instructions, exfiltrate information, or introduce further payloads on the compromised machine.
Kaspersky’s observations reveal that the attackers used the backdoor to introduce a trojan named ‘GrewApacha,’ which has been related to APT31.
The newest variant of GrewApacha options some enhancements in comparison with the final analyzed model from 2023, together with utilizing two command servers as an alternative of 1, storing their deal with in a base64-encoded string on GitHub profiles from the place the malware reads it.
Supply: Kaspersky
One other malware loaded by the backdoor is a refreshed model of CloudSorcerer filled with VMProtect for evasion.
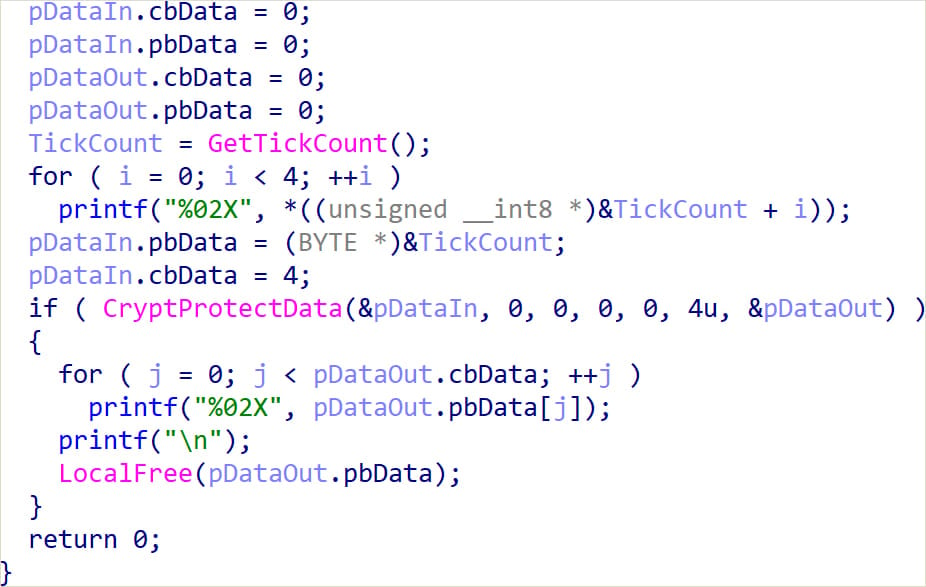
CloudSorcerer makes use of an encryption safety mechanism designed to stop its execution on non-targeted methods by using a singular key technology course of tied to the sufferer’s machine.
Upon execution, a utility (GetKey.exe) generates a singular four-byte quantity from the system’s present state and encrypts it utilizing the Home windows CryptProtectData operate to derive a singular, system-bound ciphertext.
If execution of the malware is tried on every other machine, the generated key will differ, so the CloudSorcerer payload decryption will fail.
Supply: Kaspersky
The brand new model of CloudSorcerer additionally makes use of public profile pages to get its preliminary C2 deal with however has now switched from GitHub to utilizing Quora and the Russian social media community LiveJournal for this objective.
The third implant seen within the EastWind assaults, launched by CloudSorcered, is PlugY, a beforehand unknown backdoor.
PlugY options excessive versatility in its C2 communications and the flexibility to execute instructions for file operations, shell command execution, display screen capturing, key-logging, and clipboard monitoring.
Kaspersky’s evaluation signifies that the code utilized in PlugY has been beforehand seen in assaults by the APT27 risk group.
Additionally, a library used for C2 communications by the UDP protocol is discovered solely in DRBControl and PlugX, that are malware instruments extensively utilized by Chinese language risk actors.
Supply: Kaspersky
Kaspersky feedback that, because the backdoors used within the EastWind assaults are notably completely different, detecting all of them on a compromised machine is difficult. Some issues to look out for are:
- DLL information bigger than 5MB in measurement within the ‘C:UsersPublic’ listing
- Unsigned ‘msedgeupdate.dll’ information within the file system
- A working course of named ‘msiexec.exe’ for every logged-in consumer
The Russian cybersecurity agency concludes that APT27 and APT31 are probably working collectively in EastWind.
This case highlights the complicated interaction between allied international locations with sturdy diplomatic ties and customary strategic objectives but lively cyberespionage operations towards one another.
Collaboration in financial, safety, and army fields doesn’t exclude intelligence businesses working within the shadows from launching refined and narrow-targeted espionage operations to gather beneficial intelligence.