
A Fb malvertising marketing campaign targets customers trying to find AI picture modifying instruments and steals their credentials by tricking them into putting in pretend apps that mimic official software program.
The attackers exploit the recognition of AI-driven image-generation instruments by creating malicious web sites that intently resemble official providers and trick potential victims into infecting themselves with data stealer malware, as Development Micro researchers who analyzed the marketing campaign discovered.
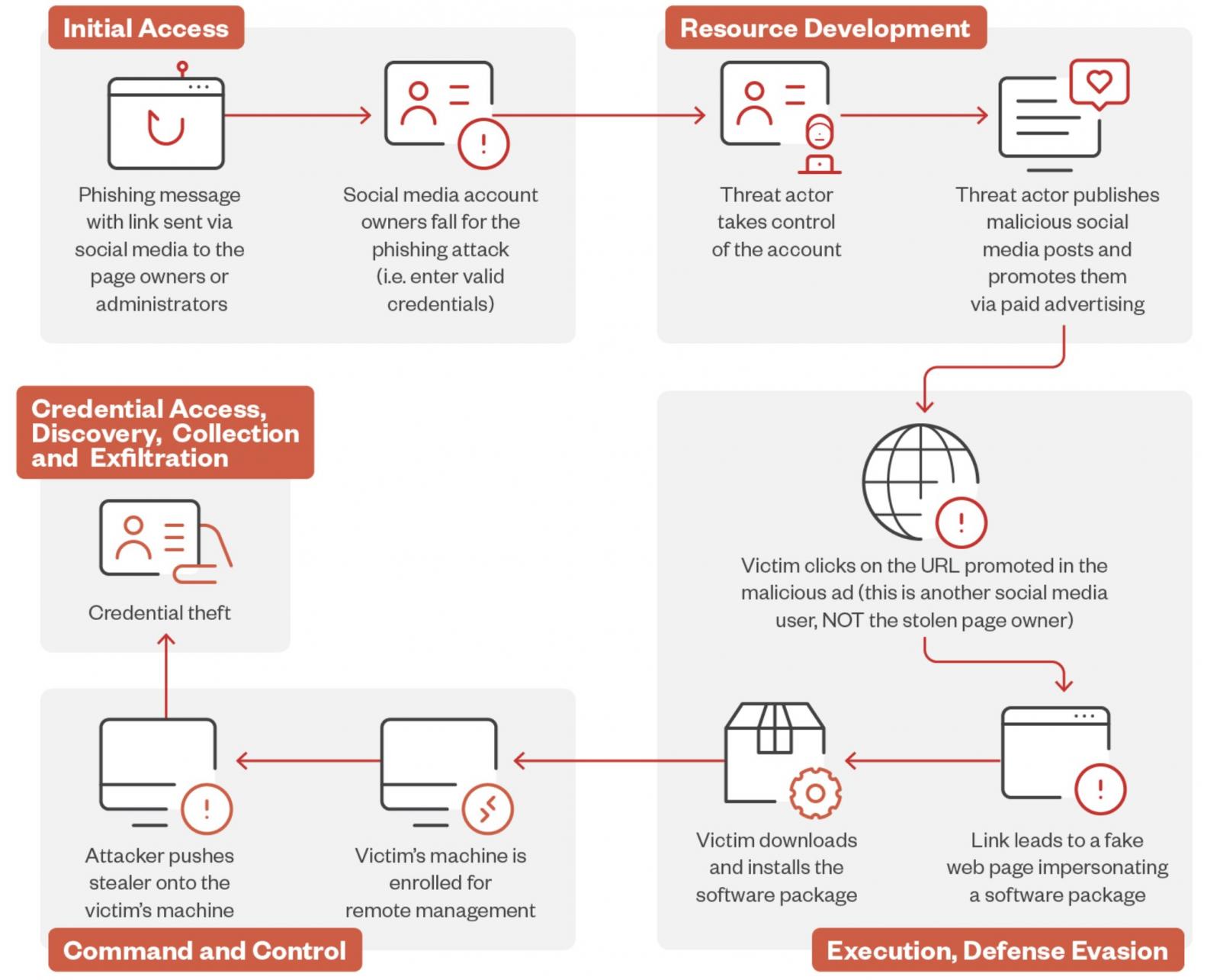
The assaults begin with phishing messages despatched to Fb web page house owners or directors, which can ship them to pretend account safety pages designed to trick them into offering their login data.
After stealing their credentials, the menace actors hijack their accounts, take management of their pages, publish malicious social media posts, and promote them through paid promoting.
“We found a malvertising marketing campaign involving a menace actor that steals social media pages (sometimes associated to pictures), altering their names to make them appear related to fashionable AI picture editors,” stated Development Micro menace researcher Jaromir Horejsi.
“The menace actor then creates malicious posts with hyperlinks to pretend web sites made to resemble the precise web site of the official picture editor. To extend visitors, the perpetrator then boosts the malicious posts through paid advertisements.”
Fb customers who click on the URL promoted within the malicious advert are despatched to a pretend net web page impersonating official AI picture modifying and producing software program, the place they’re prompted to obtain and set up a software program package deal.
Nevertheless, as a substitute of AI picture modifying software program, the victims set up the official ITarian distant desktop software configured to launch a downloader that robotically deploys the Lumma Stealer malware.
The malware then quietly infiltrates their system, permitting the attackers to gather and exfiltrate delicate data like credentials, cryptocurrency pockets recordsdata, browser knowledge, and password supervisor databases.
This knowledge is later bought to different cybercriminals or utilized by the attackers to compromise the victims’ on-line accounts, steal their cash, and promote additional scams.
“Customers ought to allow multi-factor authentication (MFA) on all social media accounts so as to add an additional layer of safety towards unauthorized entry,” Horejsi suggested.
“Organizations ought to educate their staff on the hazards of phishing assaults and easy methods to acknowledge suspicious messages and hyperlinks. Customers ought to at all times confirm the legitimacy of hyperlinks, particularly these asking for private data or login credentials.”
In April, an identical Fb malvertising marketing campaign promoted a malicious web page impersonating Midjourney to focus on virtually 1.2 million customers with the Rilide Stealer Chrome browser extension.