A ransomware group referred to as Darkish Angels made headlines this previous week when it was revealed the crime group lately obtained a report $75 million knowledge ransom cost from a Fortune 50 firm. Safety specialists say the Darkish Angels have been round since 2021, however the group doesn’t get a lot press as a result of they work alone and keep a low profile, selecting one goal at a time and favoring mass knowledge theft over disrupting the sufferer’s operations.

Picture: Shutterstock.
Safety agency Zscaler ThreatLabz this month ranked Darkish Angels as the highest ransomware menace for 2024, noting that in early 2024 a sufferer paid the ransomware group $75 million — increased than any beforehand recorded ransom cost. ThreatLabz discovered Darkish Angels has carried out a few of the largest ransomware assaults up to now, and but little is understood concerning the group.
Brett Stone-Gross, senior director of menace intelligence at ThreatLabz, stated Darkish Angels function utilizing a wholly completely different playbook than most different ransomware teams. For starters, he stated, Darkish Angels doesn’t make use of the everyday ransomware affiliate mannequin, which depends on hackers-for-hire to put in malicious software program that locks up contaminated programs.
“They actually don’t wish to be within the headlines or trigger enterprise disruptions,” Stone-Gross stated. “They’re about making a living and attracting as little consideration as potential.”
Most ransomware teams keep flashy sufferer leak websites which threaten to publish the goal’s stolen knowledge except a ransom demand is paid. However the Darkish Angels didn’t also have a sufferer shaming website till April 2023. And the leak website isn’t significantly properly branded; it’s referred to as Dunghill Leak.
The Darkish Angels sufferer shaming website, Dunghill Leak.
“Nothing about them is flashy,” Stone-Gross stated. “For the longest time, they didn’t even wish to trigger a giant headline, however they most likely felt compelled to create that leaks website as a result of they wished to point out they had been critical and that they had been going to put up sufferer knowledge and make it accessible.”
Darkish Angels is regarded as a Russia-based cybercrime syndicate whose distinguishing attribute is stealing really staggering quantities of knowledge from main firms throughout a number of sectors, together with healthcare, finance, authorities and schooling. For giant companies, the group has exfiltrated between 10-100 terabytes of knowledge, which might take days or even weeks to switch, ThreatLabz discovered.
Like most ransom gangs, Darkish Angels will publish knowledge stolen from victims who don’t pay. Among the extra notable victims listed on Dunghill Leak embody the worldwide meals distribution agency Sysco, which disclosed a ransomware assault in Might 2023; and the journey reserving large Sabre, which was hit by the Darkish Angels in September 2023.
Stone-Gross stated Darkish Angels is usually reluctant to deploy ransomware malware as a result of such assaults work by locking up the goal’s IT infrastructure, which usually causes the sufferer’s enterprise to grind to a halt for days, weeks and even months on finish. And people forms of breaches are likely to make headlines rapidly.
“They selectively select whether or not they wish to deploy ransomware or not,” he stated. “In the event that they deem they’ll encrypt some recordsdata that gained’t trigger main disruptions — however will give them a ton of knowledge — that’s what they’ll do. However actually, what separates them from the remaining is the amount of knowledge they’re stealing. It’s a complete order of magnitude better with Darkish Angels. Corporations dropping huge quantities of knowledge pays these excessive ransoms.”
So who paid the report $75 million ransom? Bleeping Laptop posited on July 30 that the sufferer was the pharmaceutical large Cencora (previously AmeriSourceBergen Company), which reported an information safety incident to the U.S. Securities and Change Fee (SEC) on February 21, 2024.
The SEC requires publicly-traded firms to reveal a probably materials cybersecurity occasion inside 4 days of the incident. Cencora is presently #10 on the Fortune 500 record, producing greater than $262 billion in income final yr.
Cencora didn’t reply to questions on whether or not it had made a ransom cost in reference to the February cybersecurity incident, and referred KrebsOnSecurity to bills listed beneath “Different” within the restructuring part of their newest quarterly monetary report (PDF). That report states that almost all of the $30 million price in “Different” was related to the breach.
Cencora’s quarterly assertion stated the incident affected a standalone legacy info know-how platform in a single nation and the international enterprise unit’s capability to function in that nation for roughly two weeks.
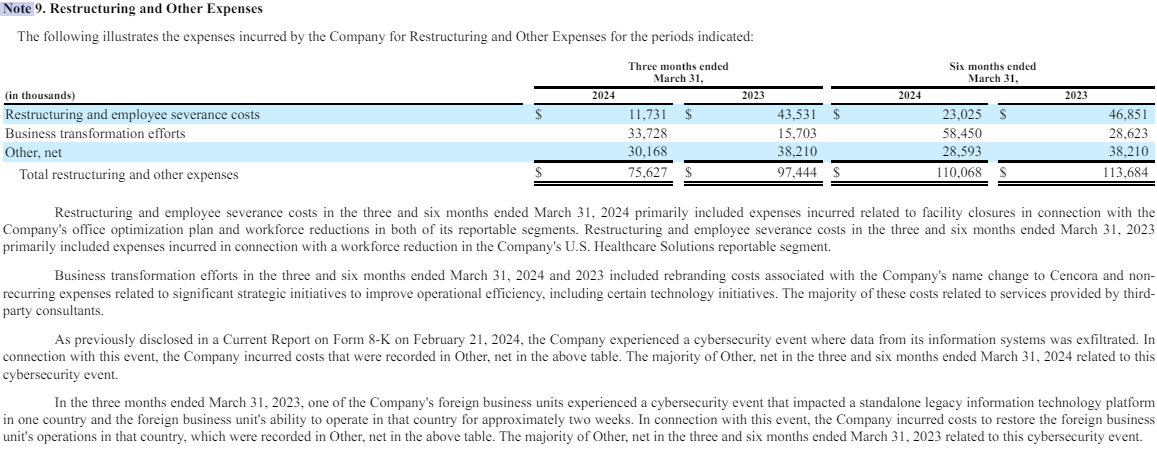
Cencora’s 2024 1st quarter report paperwork a $30 million price related to an information exfiltration occasion in mid-February 2024.
In its most up-to-date State of Ransomware report (PDF), safety agency Sophos discovered the common ransomware cost had elevated fivefold prior to now yr, from $400,000 in 2023 to $2 million. Sophos says that in additional than four-fifths (82%) of circumstances funding for the ransom got here from a number of sources. Total, 40% of complete ransom funding got here from the organizations themselves and 23% from insurance coverage suppliers.
Additional studying: ThreatLabz ransomware report (PDF).