
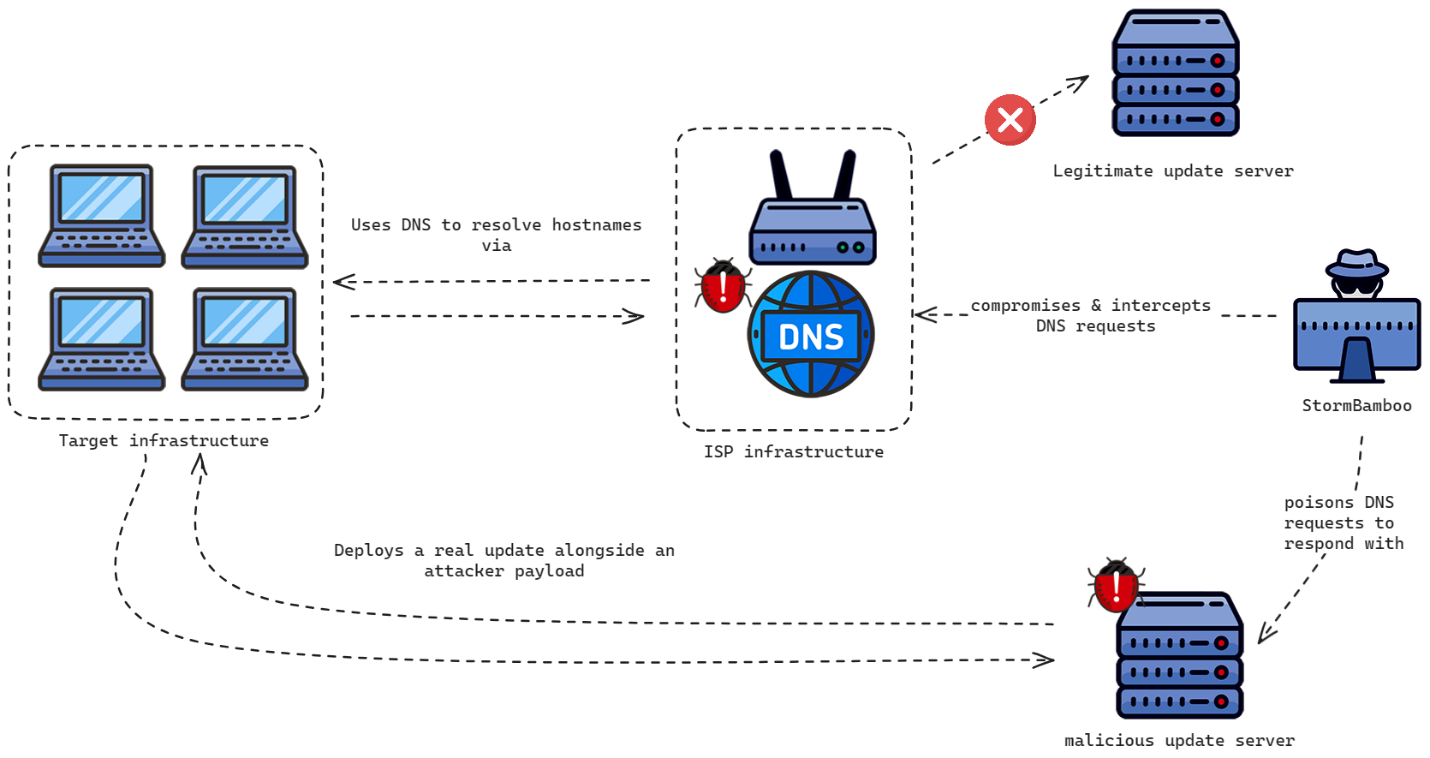
A Chinese language hacking group tracked as StormBamboo has compromised an undisclosed web service supplier (ISP) to poison automated software program updates with malware.
Additionally tracked as Evasive Panda, Daggerfly, and StormCloud, this cyber-espionage group has been energetic since a minimum of 2012, concentrating on organizations throughout mainland China, Hong Kong, Macao, Nigeria, and numerous Southeast and East Asian nations.
On Friday, Volexity risk researchers revealed that the Chinese language cyber-espionage gang had exploited insecure HTTP software program replace mechanisms that did not validate digital signatures to deploy malware payloads on victims’ Home windows and macOS units.
“When these functions went to retrieve their updates, as an alternative of putting in the meant replace, they might set up malware, together with however not restricted to MACMA and POCOSTICK (aka MGBot),” cybersecurity firm Volexity defined in a report printed on Friday.
To try this, the attackers intercepted and modified victims’ DNS requests and poisoned them with malicious IP addresses. This delivered the malware to the targets’ techniques from StormBamboo’s command-and-control servers with out requiring consumer interplay.
As an example, they took benefit of 5KPlayer requests to replace the youtube-dl dependency to push a backdoored installer hosted on their C2 servers.
After compromising the goal’s techniques, the risk actors put in a malicious Google Chrome extension (ReloadText), which allowed them to reap and steal browser cookies and mail knowledge.
“Volexity noticed StormBamboo concentrating on a number of software program distributors, who use insecure replace workflows, utilizing various ranges of complexity of their steps for pushing malware,” the researchers added.
“Volexity notified and labored with the ISP, who investigated numerous key units offering traffic-routing companies on their community. Because the ISP rebooted and took numerous elements of the community offline, the DNS poisoning instantly stopped.”
In April 2023, ESET risk researchers additionally noticed the hacking group deploying the Pocostick (MGBot) Home windows backdoor by abusing the automated replace mechanism for the Tencent QQ messaging utility in assaults concentrating on worldwide NGOs (non-governmental organizations).
Nearly a yr later, in July 2024, Symantec’s risk looking crew noticed the Chinese language hackers concentrating on an American NGO in China and a number of organizations in Taiwan with new Macma macOS backdoor and Nightdoor Home windows malware variations.
In each circumstances, though the attackers’ talent was evident, the researchers believed it was both a provide chain assault or an adversary-in-the-middle (AITM) assault however weren’t in a position to pin down the precise assault methodology.