Working in ‘kernel-space’ – probably the most privileged layer of an working system, with direct entry to reminiscence, {hardware}, useful resource administration, and storage – is vitally essential for safety merchandise. It permits them to observe ‘user-space’ – the non-privileged surroundings the place purposes run – and shield in opposition to malware that executes in that surroundings, even when it tries to evade detection. However kernel entry additionally permits safety merchandise to counter extra insidious threats throughout the kernel itself. As we’ve reported beforehand, for instance, some menace actors use BYOVD (Deliver Your Personal Weak Driver) assaults, or try and get their very own malicious drivers cryptographically signed, to be able to entry kernel-space and reap the benefits of that elevated stage of entry.
Nonetheless, from a safety standpoint, working in kernel-space comes with its personal dangers. A incorrect step on this surroundings – similar to a foul replace to a kernel driver – could cause outages. If the motive force in query begins at boot time, when the working system first hundreds, that may result in extended impacts, doubtlessly requiring affected hosts to be began in a restoration mode to mitigate the issue and permit the machines besides usually.
Sophos’ Intercept X Superior product makes use of 5 kernel drivers as of launch 2024.2. All drivers are extensively examined* with relevant flags enabled and disabled, and shipped with new flags disabled. (Sophos Intercept X and Sophos Central use function flags to progressively allow new options. Function flags are deployed by way of Sophos Central. New options are sometimes ‘guarded’ by function flags – turned off until the flag is enabled – in order that the function will be rolled out progressively and doubtlessly revised earlier than wider enablement.)
On this article, within the pursuits of transparency, we’ll discover what these drivers are, what they do, after they begin, how they’re signed, and what their inputs are. We’ll additionally discover a few of the safeguards we put in place round these drivers to reduce the danger of disruption (similar to staged rollouts, as talked about above; we offer an instance of this later within the article), and the choices accessible to clients with regards to configuring them. It’s additionally value noting that Intercept X Superior and all its elements, together with the kernel drivers, has been a part of an exterior bug bounty program since December 14, 2017; we welcome scrutiny by way of exterior bug bounty submissions, and we foster a tradition of collaboration with the analysis neighborhood.
* ‘Testing’ refers to a spread of inner testing, together with Microsoft-provided instruments and verifiers
The next desk gives an at-a-glance overview of the 5 kernel drivers that are a part of Intercept X Superior launch 2024.2.
| Driver | Model | Kind | Begin Kind | Signed By Microsoft? | Signature | Description |
| SophosEL.sys | 3.2.0.1150
|
Kernel Driver | Early-Launch Boot Begin | Sure | ELAMP* | Sophos ELAM driver: can stop execution of malicious boot begin drivers |
| SophosED.sys | 3.3.0.1727
|
File System Driver | Boot Begin | Sure | WHCP+ | The principle Sophos anti-malware driver |
| Sntp.sys | 1.15.1121
|
Community Filter Driver | System Begin | Sure | WHCP+ | Sophos Community Menace Safety driver |
| Hmpalert.sys | 3.9.4.990
|
File System Driver | System Begin
|
Sure | WHCP+ | Sophos HitmanPro.Alert driver |
| SophosZtnaTap.sys | 9.24.6.3
|
Community Filter Driver | On Demand | Sure | WHCP+ | Sophos Zero Belief Community Entry (ZTNA) Faucet driver |
Desk 1: An summary of the kernel drivers in Intercept X Advanced2024.2
* Microsoft Home windows Early Launch Anti-malware Writer
+ Microsoft Home windows {Hardware} Compatibility Writer
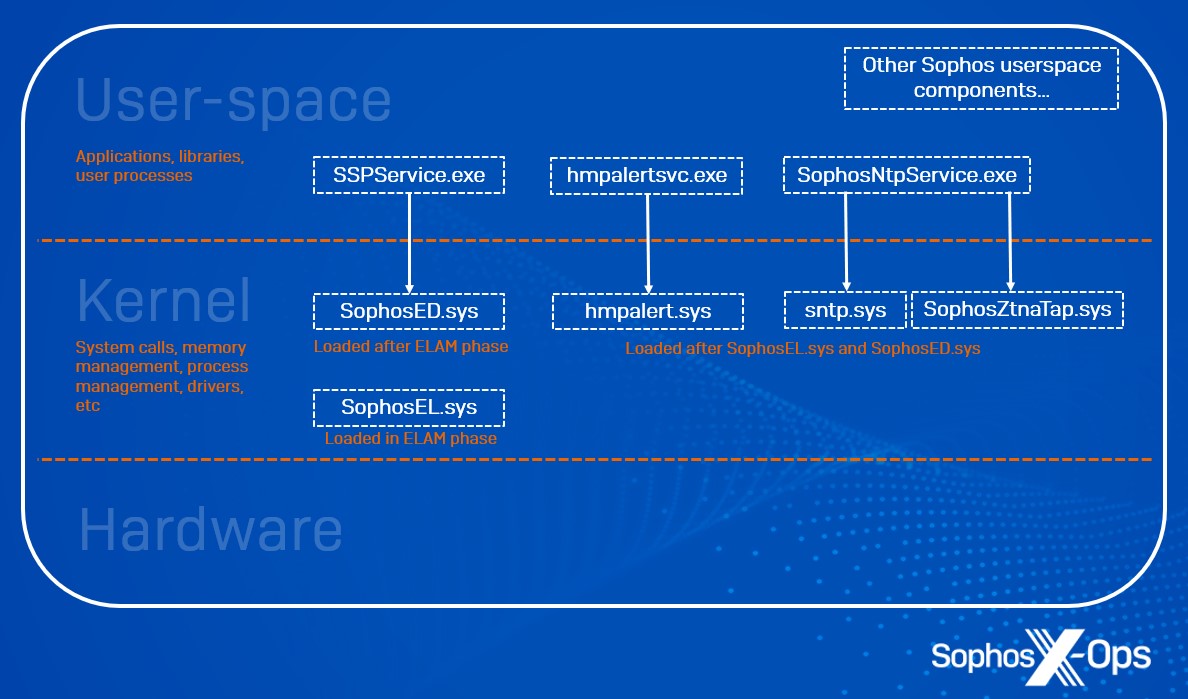
Determine 1: A conceptual depiction of user-space/kernel boundaries and the place Intercept X Superior elements function
What it does: SophosEL.sys is the Sophos Early Launch Anti-Malware (ELAM) driver.
Inputs: This driver has one enter – a blocklist of known-bad drivers which should be prevented from executing as boot begin drivers at machine startup. This blocklist, situated on the registry key beneath, is about by Sophos user-space menace detection logic when it detects a malicious driver. On the subsequent boot cycle, SophosEL.sys ensures that this driver shouldn’t be loaded.
| Enter | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos ELAMConfig | Blocklist of known-bad drivers | DACLs; Sophos Tamper Protected |
Buyer choices: Clients can configure remediation and allowed gadgets within the Menace Safety coverage from Sophos Central.
Extra measures: Any Microsoft or Sophos-signed driver is exempt from cleanup/blocking.
What it does: SophosED.sys (Endpoint Protection) is a boot begin driver, began throughout ELAM processing and earlier than many different kernel drivers are loaded, Home windows user-space is initialized, and the system drive is mounted. It has three broad duties:
- Offering tamper safety for the Sophos set up and configuration
- Exposing system exercise occasions to Sophos user-space elements for cover and detection
- Recording low-level system exercise occasions to the Sophos Occasion Journals for after-the-fact forensics and evaluation
Inputs: Since SophosED.sys begins earlier than the filesystem is accessible, its whole configuration is offered by way of its service key. Observe that every one the beneath inputs are below HKLMSYSTEMCurrentControlSetServicesSophos Endpoint Protection.
Filter driver altitudes inputs
SophosED.sys registers with Home windows as a Mini-Filter driver at a number of altitudes (a singular identifier that defines a driver’s place on the ‘stack’ of drivers, with ‘decrease’ drivers being nearer to reveal metallic) allotted and accepted by Microsoft.
| Enter | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseInstances | A number of altitudes allotted by Microsoft | DACLs; Sophos Tamper Protected |
Tamper Safety inputs
Sophos Tamper Safety is configured by a mix of buyer insurance policies, Sophos function flags, and signed manifests constructed into the agent.
| Enter | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionConfig | Buyer coverage (On/Off, configuration password*) | DACLs; Sophos Tamper Protected |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionComponents
HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionServices |
Manifest of protected keys, folders, companies and so forth | Signed; verified by driver earlier than loading |
* The configuration password is hashed with PBKDF2-SHA512 and a salt
System Exercise Occasions inputs
The Sophos Central Menace Safety coverage helps a number of configuration choices, which Sophos user-space processes write to the SophosED.sys registry key, in order that they’re accessible when the motive force is loaded.
| Enter | Description | Safety |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseScanningConfig | Buyer coverage (On/Off, exclusions, and plenty extra) | DACLs; Sophos Tamper Protected |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Sophos function flags (varied) | DACLs; Sophos Tamper Protected |
Occasion Journal inputs
| Enter | Description | Safety |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalConfig | Buyer coverage (exclusions, disk limits) | DACLs; Sophos Tamper Protected |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalFeatures | If a subkey exists with a DWORD worth Enabled =1, occasion journals are enabled | DACLs; Sophos Tamper Protected |
Buyer choices: Clients can configure disk limits and handle exclusions in Sophos Central Menace Safety coverage.
Extra measures: If a driver facility is accessible (based mostly on a mix of Buyer Coverage plus Sophos flag), then Sophos user-space processes can configure varied parameters at runtime:
- A bitmask of mitigations to use per-process
- What occasions to allow or disable for every course of
- The period of time the motive force ought to anticipate a response from user-space (or whether or not it must be an asynchronous notification).
What it does: Sntp.sys (Sophos Community Menace Safety) is a kernel driver that registers for varied Home windows Filtering Platform occasions to intercept and doubtlessly modify community movement knowledge. Relying on options enabled by Sophos Central Menace Safety and Net Management insurance policies, completely different filters and callouts are registered.
Inputs: Function configuration is communicated to the motive force from a number of of the next consumer mode processes:
- SophosNtpService.exe
- SophosNetFilter.exe
- SophosIPS.exe
- SSPService.exe
Person-space processes talk with the motive force by way of the Home windows Driver Framework, utilizing IOCTLs, Learn, and Write. Communications to and from the motive force are protected, solely accepting connections from approved and genuine Sophos processes.
Buyer choices: The filter driver intercepts community site visitors by browser and non-browser processes based mostly on the insurance policies outlined in Sophos Central. Processing of the intercepted site visitors is carried out in user-space by SophosNetFilter.exe and SophosIPS.exe, which can ship modified content material again to the motive force (for instance, to show a block web page for malicious content material).
Extra measures: Clients can add particular person websites to their enable or block listing in Sophos Central.
What it does: Hmpalert.sys enforces Sophos CryptoGuard, which detects and prevents bulk encryption of information by ransomware. It additionally configures what exploit mitigations are enforced as processes are executed.
Inputs: Hmpalert.sys has quite a lot of inputs, together with a number of registry subkeys and IOCTLS.
| Enter | Description | Safety |
| HKLMSYSTEMCurrentControlSetServiceshmpalert | Software program configuration | DACLs; Sophos Tamper Protected |
| HKLM SYSTEMCurrentControlSetServiceshmpalertConfig | Buyer coverage | DACLs; Sophos Tamper Protected |
| HKLM SYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Sophos function flags (varied) | DACLs; Sophos Tamper Protected |
Buyer choices: Clients can allow/disable exploit mitigations and handle exclusions in Sophos Central Menace Safety coverage.
Extra measures: N/A
What it does: SophosZtnaTap.sys is a Sophos-built OpenVPN TAP driver. If the client deploys the Sophos Zero Belief Community Entry (ZTNA) agent, the motive force intercepts DNS lookups for managed purposes, and redirects site visitors for these purposes to the relevant Sophos ZTNA gateways. ZTNA purposes and gateways are configured by way of Sophos Central insurance policies and saved within the registry.
Inputs: Inputs into SophosZtnaTap.sys are by way of a registry subkey.
| Enter | Description | Safety |
| HKLMSOFTWARESophosManagementPolicyNetworkPerimeter | Buyer coverage (ZTNA Purposes, Gateways, and certificates) | DACLs; Sophos Tamper Protected |
Buyer choices: Clients can handle their ZTNA-protected purposes and gateways from Sophos Central.
Extra measures: N/A
Sophos CryptoGuard has protected in opposition to bulk encryption on everlasting disks for over a decade. Intercept X model 2024.1.1 launched a brand new function, CryptoGuard ExFAT, which extends this safety to ExFAT partitions (sometimes discovered on detachable USB drives).
CryptoGuard ExFAT growth and testing came about in September 2023 by way of March 2024. This function was guarded by the flag ‘hmpa.cryptoguard-exfat.accessible.’
Sophos Engineering ran the software program internally with the flag enabled (our ‘Dogfood launch’) beginning March 22, 2024.
Intercept X model 2024.1.1 was launched to Sophos, then to clients utilizing our gradual software program deployment course of, between Could 21, 2024 by way of June 6, 2024. At this stage the function was nonetheless dormant for everybody aside from Sophos engineers.
The ’hmpa.cryptoguard-exfat.accessible’ flag was enabled utilizing our gradual flag enablement course of, between June 10, 2024 by way of June 26, 2024.
Clients can choose a hard and fast software program model (Endpoint Software program Administration: Fastened-term help, Lengthy-term help). This locks the software program and flags till the client selects a special software program bundle. Clients who use the ‘Sophos really helpful’ possibility obtain new software program periodically. Apart from software program rollouts, in addition they obtain gradual feature-flag enablements for brand spanking new options within the software program, as with a standard software program launch. Sophos has advanced this course of to enhance stability and keep away from enabling new occasions globally for all clients.
Kernel drivers are elementary to the Intercept X Superior product – and to strong Home windows endpoint safety, usually – however we additionally acknowledge that working in kernel-space shouldn’t be with out its dangers.
On this article, we’ve walked by way of the kernel drivers in Intercept X Superior (as of launch 2024.02), what they do, how they’re signed, what their inputs are, the management clients have over their administration, and extra safeguards we’ve put in place – together with gradual, phased rollouts of recent options, and exemptions to reduce the danger of disruption.
Whereas no safeguard can ever eradicate threat altogether, we needed to share the main points of our drivers within the pursuits of transparency, and to elucidate in depth how we strategy the advanced downside of making an attempt to guard our clients from threats, in as protected a fashion as doable.