Scams
Your humble telephone quantity is extra useful than you might suppose. Right here’s the way it might fall into the incorrect arms – and how one can assist maintain it out of the attain of fraudsters.
15 Jul 2024
•
,
7 min. learn

What could be one of many best methods to rip-off somebody out of their cash – anonymously, in fact?
Wouldn’t it contain stealing their bank card knowledge, maybe utilizing digital skimming or after hacking right into a database of delicate private data? Whereas efficient, these strategies could also be resource-intensive and require some technical prowess.
What about stealing cost information by way of pretend web sites? This may occasionally certainly match the invoice, however spoofing legit web sites (and e-mail addresses to “unfold the phrase”) might not be for everyone, both. The chances are additionally excessive that such ploys shall be noticed in time by the security-savvy amongst us or thwarted by safety controls.
As a substitute, dangerous actors are turning to extremely scalable operations that depend on refined social engineering techniques and prices little to function. Utilizing voice phishing (additionally referred to as vishing) and message scams (smishing), these operations have been developed right into a rip-off call-center business price billions of {dollars}.
For starters, these ploys might not require a lot in the way in which of specialised or technical expertise. Additionally, a single particular person (usually a sufferer of human trafficking) can, at a time, ensnare a number of unwitting victims in varied flavors of fraud. These usually contain pig butchering, cryptocurrency schemes, romance scams, and tech assist fraud, every of which spins a compelling yarn and preys on a few of what really makes us human.
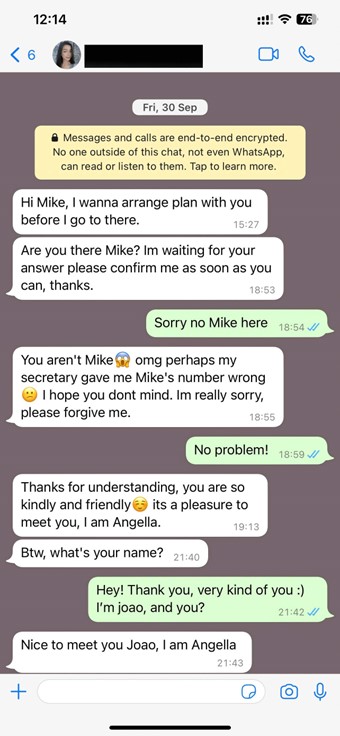
Hi there? Is that this factor on?
Think about receiving a name out of your financial institution to tell you that your account has been breached and in an effort to maintain your cash secure, you should share your delicate particulars with them. The urgency within the voice of the financial institution’s “worker” might certainly be sufficient to immediate you to share your delicate data. The issue is, this particular person may not be out of your financial institution – or they could not even exist in any respect. It could possibly be only a fabricated voice, however nonetheless sound utterly pure.
This isn’t in any respect unusual and cautionary tales from latest years abound. Again in 2019, a CEO was scammed out of virtually US$250,000 by a convincing voice deepfake of their father or mother firm’s chief. Equally, a finance employee was tricked by way of a deepfake video name in 2024, costing their agency US$25 million.
AI, the enabler
With trendy AI voice cloning and translation capabilities, vishing and smishing have turn out to be simpler than ever. Certainly, ESET World Cybersecurity Advisor Jake Moore demonstrated the benefit with which anyone can create a convincing deepfake model of another person – together with somebody you recognize effectively. Seeing and listening to are now not believing.
AI is decreasing the barrier of entry for brand new adversaries, serving as a multipronged device to collect knowledge, automate tedious duties, and globalize their attain. Consequently, phishing utilizing AI-generated voices and textual content will most likely turn out to be extra commonplace.
On this word, a latest report by Enea famous a 1,265% rise in phishing scams because the launch of ChatGPT in November 2022 and spotlighted the potential of huge language fashions to assist gas such malicious operations.
What’s your identify, what’s your quantity?
As evidenced by Client Experiences analysis from 2022, persons are changing into extra privacy-conscious than earlier than. Some 75% of the survey’s respondents had been not less than considerably involved in regards to the privateness of their knowledge collected on-line, which can embody telephone numbers, as they’re a useful useful resource for each identification and promoting.
However now that we’re effectively previous the age of the Yellow Pages, how does this connection between telephone numbers and promoting work?
Think about this illustrative instance: a baseball fan positioned tickets in a devoted app’s checkout however did not full the acquisition. And but, shortly after closing the app, he obtained a telephone name providing a reduction on the tickets. Naturally, he was baffled since he didn’t keep in mind offering his telephone quantity to the app. How did it get his quantity, then?
The reply is – by way of monitoring. Some trackers can accumulate particular data from a webpage, so after you’ve stuffed of their telephone quantity in a kind, a tracker might detect and retailer it to create what is usually referred to as personalised content material and expertise. There’s a whole enterprise mannequin often called “knowledge brokering”, and the dangerous information is that it doesn’t take a breach for the information to turn out to be public.
Monitoring, knowledge brokers, and leaks
Knowledge brokers vacuum up your private data from publicly obtainable sources (authorities licenses/registrations), industrial sources (enterprise companions like bank card suppliers or shops) in addition to by monitoring your on-line actions (actions on social media, advert clicks, and so forth.), earlier than promoting your data to others.
Nonetheless, the query in your lips could also be: how can scammers acquire different folks’s telephone numbers?
Naturally, the extra corporations, websites, and apps you share your private data with, the extra detailed your private “advertising and marketing profile” is. This additionally will increase your publicity to knowledge leaks, since knowledge brokers themselves can expertise safety incidents. A knowledge dealer might additionally promote your data to others, probably together with dangerous actors.
However knowledge brokers, or breaches affecting them, aren’t the one supply of telephone numbers for scammers. Listed below are another methods wherein criminals can get ahold of your telephone quantity:
- Public sources: Social media websites or on-line job markets may present your telephone quantity as a method to make a connection. In case your privateness settings usually are not dialed in accurately or you aren’t conscious of the results of revealing your telephone quantity in your social media profile, your quantity could be obtainable to anybody, even an AI net scraper.
- Stolen accounts: Numerous on-line companies require your telephone quantity, be it to verify your id, to put an order, or to function an authentication issue. When your accounts get brute-forced as a consequence of weak passwords or certainly one of your on-line suppliers suffers an information breach your quantity might simply leak as effectively.
- Autodialers: Autodialers name random numbers, and as quickly as you reply the decision, you might be focused by a rip-off. Typically these autodialers name simply to verify that the quantity is in use in order that it may be added to an inventory of targets.
- Mail: Test any of your latest deliveries – these often have your tackle seen on the letter/field, however in some circumstances, they will even have your e-mail or telephone quantity printed on them. What if somebody stole certainly one of your deliveries or rummaged via your recycling pile? Contemplating that knowledge leaks often comprise the identical data, this may be very harmful and grounds for additional exploitation.
For example of a wide-scale breach affecting telephone numbers, AT&T lately revealed that tens of millions of shoppers’ name and textual content message data from mid-to-late 2022 had been uncovered in an enormous knowledge leak. Almost the entire firm’s clients and folks utilizing the cell community have had their numbers, name durations, and variety of name interactions uncovered. Whereas name and textual content contents are allegedly not among the many breached knowledge, buyer names and numbers can nonetheless be simply linked, as reported by CNN.
Reportedly, the blame may be placed on a third-party cloud platform, which a malicious actor had accessed. Coincidentally, the identical platform has had a number of circumstances of large leaks linked to it in recent times.
Find out how to defend your telephone quantity
So, how will you defend your self and your quantity? Listed below are a couple of ideas:
- Concentrate on phishing. By no means reply unsolicited messages/calls from overseas numbers, don’t click on on random hyperlinks in your emails/messages, and keep in mind to maintain cool and suppose earlier than you react to a seemingly pressing state of affairs, as a result of that’s how they get you.
- Ask your service supplier about their SIM safety measures. They may have an possibility for card locks to guard in opposition to SIM swapping, for instance, or extra account safety layers to stop scams like name forwarding.
- Shield your accounts with two-factor authentication, ideally utilizing devoted safety keys, apps, or biometrics as a substitute of SMS-based verification. The latter may be intercepted by dangerous actors with relative ease. Do the identical for service supplier accounts as effectively.
- Suppose twice earlier than offering your telephone quantity to an internet site. Whereas having it as an extra restoration possibility in your varied apps could be helpful, different strategies like secondary emails/authenticators might provide a safer various.
- For on-line purchases, think about using a pre-paid SIM card or a VoIP service as a substitute of your common telephone quantity.
- Use a cell safety answer with name filtering, in addition to ensure that third-party cookies in your net browser are blocked, and discover different privacy-enhancing instruments and applied sciences.
In a world that more and more depends on on-line report holding, there’s a low likelihood that your quantity gained’t be preserved by a 3rd social gathering someplace. And because the AT&T incident suggests, relying by yourself service’s safety can be slightly problematic. This doesn’t imply that it’s best to stay in a state of fixed paranoia, although.
Alternatively, it highlights the significance of committing to correct cyber hygiene and being conscious of your knowledge on-line. Vigilance can be nonetheless key, particularly when contemplating the implications of this new, AI-powered (beneath)world.
