March 11, 2024
Introduction
The objective of this assault was to gather delicate details about the workers in addition to to collect knowledge in regards to the firm’s infrastructure and its inside community. As well as, we detected that knowledge had been uploaded from the contaminated pc; this included recordsdata saved on the pc and screenshots taken whereas the malware was in operation.
Common details about the assault and the instruments concerned
In early October 2023, malicious actors despatched a number of phishing emails to the e-mail tackle of the affected firm. The topic of the messages was associated to an “investigation” of sure felony instances of tax evasion. These emails had been supposedly despatched on behalf of an investigator with the Investigative Committee of the Russian Federation and contained two attachments. The primary one was a password-protected ZIP archive. It hid a computer virus which, when executed, initiated the system an infection course of. The second attachment, a PDF doc, was not malicious. It contained a phishing textual content stating that every one the details about the “felony case” was within the archive and inspired the person to open the computer virus from it.
The very first such phishing message contained the ZIP archive Трeбoвaниe 19098 Cлед ком РФ от 02.10.23 ПАРОЛЬ – 123123123.zip. For its half, the trojan app in it was hid within the file Перечень юридических лиц и предприятий, уклонение от уплаты налогов, требования и дополнительные.exe.
One of many final messages despatched is the one proven under:
The phishing PDF doc Требование следователя, уклонение от уплаты налогов (запрос в рамках УД).pdf and the ZIP archive Трeбoвaниe 19221 СК РФ от 11.10.2023 ПАРОЛЬ – 123123123.zip had been hooked up to it. The archive contained the next objects:
Just like of their earlier messages, the attackers indicated the password for extracting recordsdata from the archive, each in its title and within the title of the doc Пароль для открытия 123123123.odt. This doc itself, in addition to the recordsdata Права и обязанности и процедура ст. 164, 170, 183 УПК РФ.pdf and the СК РФ.png, weren’t malicious.
This archive contained two copies of the trojan software: Перечень предприятий, уклонение от уплаты налогов, а также дополнительные материалы.exe and Дополнительные материалы, перечень вопросов, накладные и первичные документы.exe.
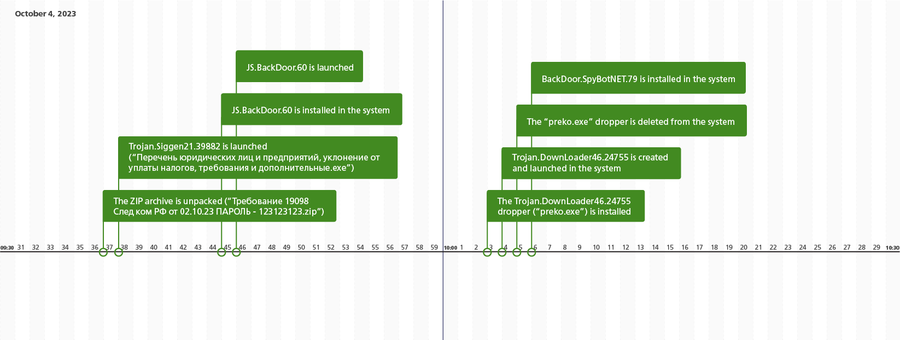
In all instances, Trojan.Siggen21.39882 was the computer virus distributed by attackers. This malware, also called WhiteSnake Stealer, is offered on the DarkNet and is used to steal account knowledge from quite a lot of software program and to hijack different knowledge. Furthermore, it will probably obtain and set up different malicious apps on attacked computer systems. Within the focused assault in query, it was assigned the position of initiating the primary an infection stage. After receiving the corresponding instructions, this trojan collected and transmitted to the attackers details about configuring Wi-Fi community profiles within the contaminated system in addition to the passwords for accessing them. It then launched an SSH proxy server and put in the second stage within the system.
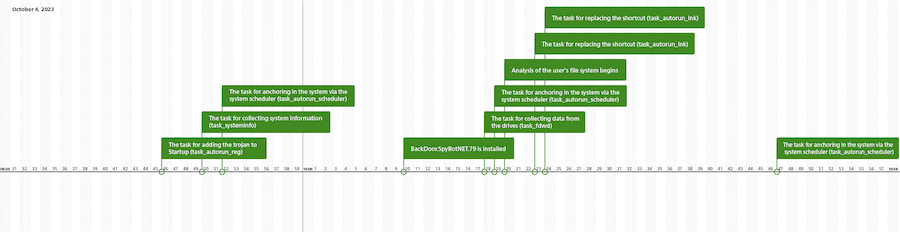
The second stage, and concurrently the menace actors’ important instrument, was the JS.BackDoor.60 malicious backdoor program. It was the device by means of which the primary interplay between the attackers and the contaminated system happened. One of many backdoor’s options is that it makes use of its personal JavaScript framework. The trojan consists of the first obfuscated physique and extra modules that, owing to the specifics of the malware’s structure, are concurrently a trojan part and the duties that it executes by way of the JavaScript capabilities they share. The trojan receives new duties from its C&C server, and de facto they flip it right into a multi-component menace with expandable performance, which permits it for use as a robust cyberespionage instrument.
The mechanism that JS.BackDoor.60 used to supply itself with the autorun potential can also be of curiosity. Together with using a standard methodology—including crucial adjustments to the Home windows registry—the trojan modified the shortcut recordsdata (.lnk) in a selected means. For this, it verified the contents of a variety of system directories, together with the Desktop and taskbar directories. For all of the shortcut recordsdata it present in them (excluding Explorer.lnk or Проводник.lnk), it assigned this system wscript.exe as a goal app for launching. On the identical time, it added particular arguments for its execution, considered one of which was the Alternate Knowledge Stream (or ADS), wherein the backdoor physique was written. Because of the adjustments, the modified shortcuts launched the JS.BackDoor.60 first, and solely after that―the preliminary packages.
All through the entire assault, malicious actors had been actively sending numerous instructions to the backdoor. With its assist, they stole the contents of dozens of directories from the contaminated pc, which contained each private and company knowledge. Furthermore, we discovered proof that the trojan had created screenshots.
The extra spying instrument on this assault was the BackDoor.SpyBotNET.79 computer virus, which was used for audio surveillance and for recording conversations by means of the microphone hooked up to the contaminated pc. This trojan recorded audio solely when it detected a sure sound depth―specifically, one attribute of a voice.
On the identical time, the attackers additionally tried to contaminate the system with the Trojan.DownLoader46.24755 downloader trojan, however failed as a result of an error that occurred.
The chronology of the assault is proven within the subsequent illustration:
The chronology of the duties obtained by JS.BackDoor.60:
The evaluation carried out by our specialists didn’t clearly point out the involvement of any of the beforehand recognized APT teams on this assault.
For detailed technical descriptions of the malicious packages detected, please discuss with the PDF model of the examine or go to the Physician Net virus library.
Extra particulars on Trojan.Siggen21.39882
Extra particulars on JS.BackDoor.60
Extra particulars on BackDoor.SpyBotNET.79
Extra particulars on Trojan.DownLoader46.24755
Conclusion
The usage of malicious devices, which can be found as a industrial service (MaaS ― Malware as a Service), reminiscent of Trojan.Siggen21.39882, permits even comparatively inexperienced malicious actors to hold out fairly delicate assaults towards each companies and authorities businesses. For its half, social engineering nonetheless poses a critical menace. This can be a comparatively easy however efficient method to bypass a built-in safety layer, and it may be utilized by each skilled and novice cybercriminals. On this regard, it’s particularly vital to make sure that the whole infrastructure of an enterprise is protected, together with its workstations and e-mail gateways. Furthermore, it is strongly recommended to conduct periodic coaching periods for workers on the subject of data safety and to familiarize them with present digital threats. All these measures will assist scale back the probability of cyber incidents and decrease the injury from assaults.