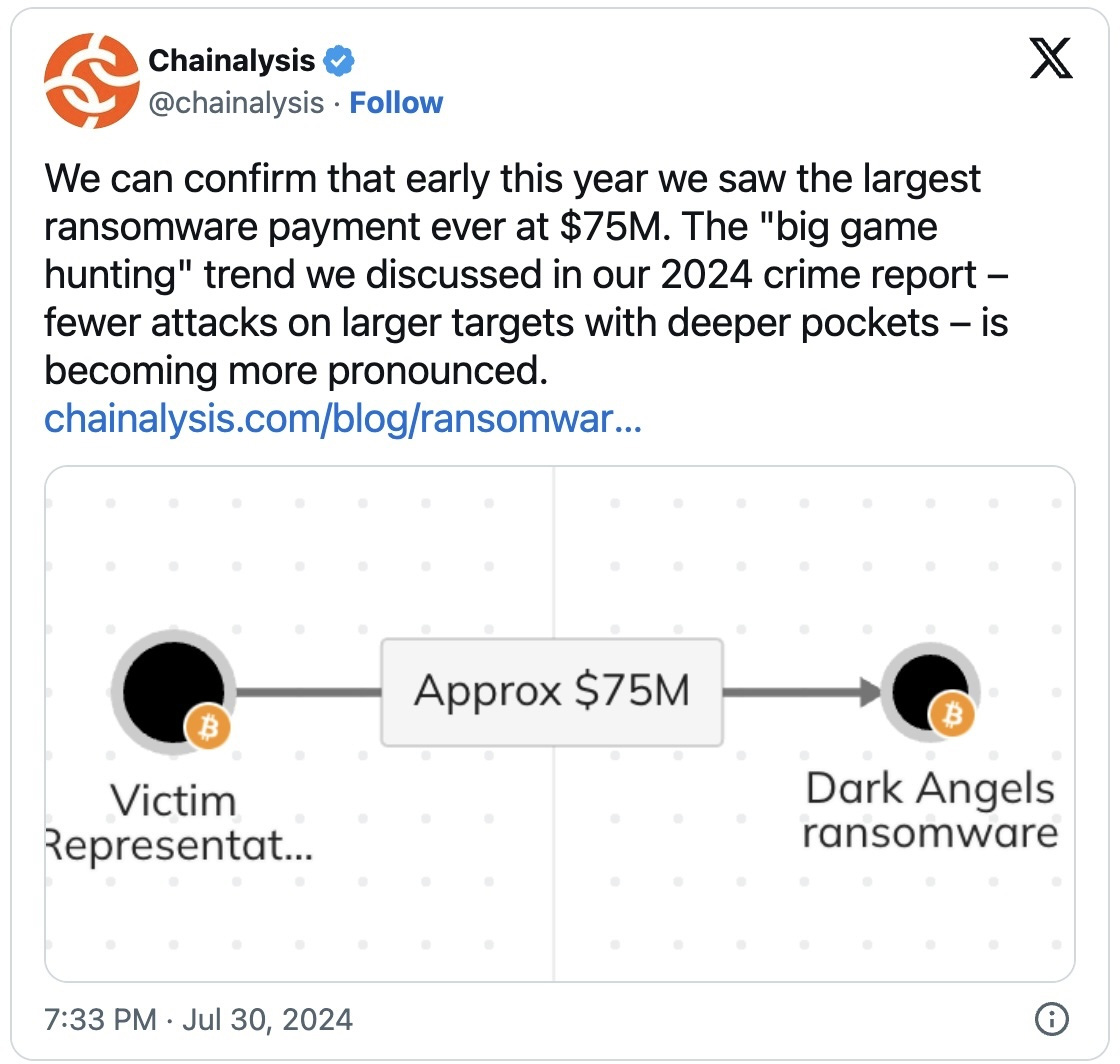
A Fortune 50 firm paid a record-breaking $75 million ransom cost to the Darkish Angels ransomware gang, in accordance with a report by Zscaler ThreatLabz.
“In early 2024, ThreatLabz uncovered a sufferer who paid Darkish Angels $75 million, larger than any publicly recognized quantity— an achievement that is certain to draw the curiosity of different attackers seeking to replicate such success by adopting their key techniques (which we describe beneath),” reads the 2024 Zscaler Ransomware Report.
This record-breaking cost was additional confirmed by crypto intelligence firm Chainalysis, who tweeted about it on X.
The most important recognized ransom cost was beforehand $40 million, which insurance coverage big CNA paid after struggling an Evil Corp ransomware assault.
Whereas Zscaler didn’t share what firm paid the $75 million ransom, they talked about the corporate was within the Fortune 50 and the assault occurred in early 2024.
One Fortune 50 firm that suffered a cyberattack in February 2024 is pharmaceutical big Cencora, ranked #10 on the record. No ransomware gang ever claimed accountability for the assault, doubtlessly indicating {that a} ransom was paid.
BleepingComputer contacted Cencora to ask in the event that they paid the ransom to Darkish Angels however has not heard again but.
Who’s Darkish Angels
Darkish Angels is a ransomware operation launched in Might 2022 when it started focusing on firms worldwide.
Like most human-operated ransomware gangs, Darkish Angels operators breach company networks and transfer laterally till they ultimately acquire administrative entry. Throughout this time, in addition they steal information from compromised servers, which is later used as extra leverage when making ransom calls for.
After they acquire entry to the Home windows area controller, the menace actors deploy the ransomware to encrypt all units on the community.
When the menace actors launched their operation, they used Home windows and VMware ESXi encryptors based mostly on the leaked supply code for the Babuk ransomware.
Nevertheless, over time, they switched to a Linux encryptor that was the identical one utilized by Ragnar Locker since 2021. Ragnar Locker was disrupted by legislation enforcement in 2023.
This Linux encryptor was utilized in a Darkish Angels assault on Johnson Controls to encrypt the corporate’s VMware ESXi servers.
On this assault, Darkish Angels claimed to have stolen 27 TB of company information and demanded a $51 million ransom cost.
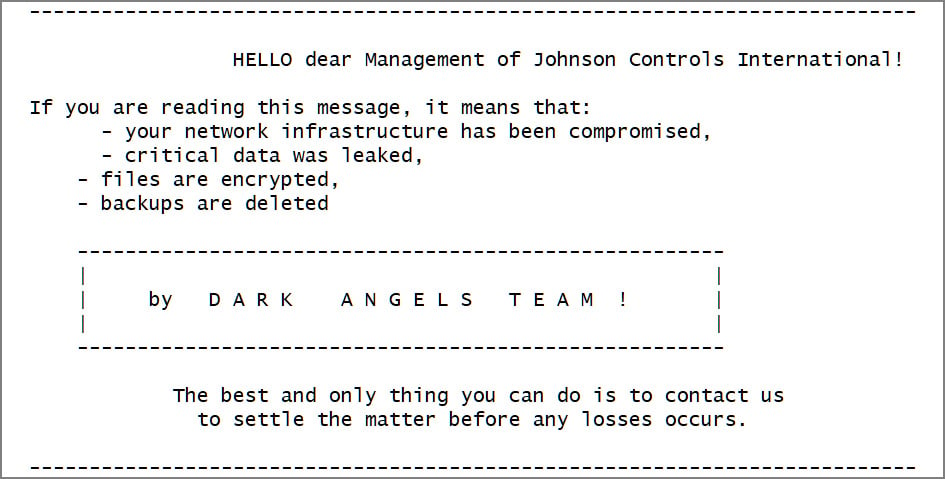
Supply: BleepingComputer
The menace actors additionally function a knowledge leak web site named ‘Dunghill Leaks’ that’s used to extort its victims, threatening to leak information if a ransom just isn’t paid.
Supply: BleepingComputer
Zscaler ThreatLabz says that Darkish Angels makes use of the “Large Sport Searching” technique, which is to focus on just a few high-value firms within the hopes of huge payouts relatively than many firms without delay for quite a few however smaller ransom funds.
“The Darkish Angels group employs a extremely focused method, sometimes attacking a single giant firm at a time,” explains the Zscaler ThreatLabz researchers.
“That is in stark distinction to most ransomware teams, which goal victims indiscriminately and outsource a lot of the assault to affiliate networks of preliminary entry brokers and penetration testing groups.”
In response to Chainalysis, the Large Sport Searching tactic has change into a dominant development utilized by quite a few ransomware gangs over the previous few years.