
Microsoft Outlook might be was a C2 beacon to remotely execute code, as demonstrated by a brand new purple workforce post-exploitation framework named “Specula,” launched at the moment by cybersecurity agency TrustedSec.
This C2 framework works by making a customized Outlook Residence Web page utilizing WebView by exploiting CVE-2017-11774, an Outlook safety characteristic bypass vulnerability patched in October 2017.
“In a file-sharing assault state of affairs, an attacker might present a specifically crafted doc file designed to take advantage of the vulnerability, after which persuade customers to open the doc file and work together with the doc,” Microsoft says.
Nevertheless, regardless that Microsoft patched the flaw and eliminated the person interface to point out Outlook house pages, attackers can nonetheless create malicious house pages utilizing Home windows Registry values, even on techniques the place the newest Workplace 365 builds are put in.
As Trusted explains, Specula runs purely in Outlook’s context, and it works by setting a customized Outlook house web page through registry keys that decision out to an interactive Python net server.
To do this, non-privileged risk actors can set a URL goal in Outlook’s WebView registry entries beneath HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0OutlookWebView to an exterior web site beneath their management.
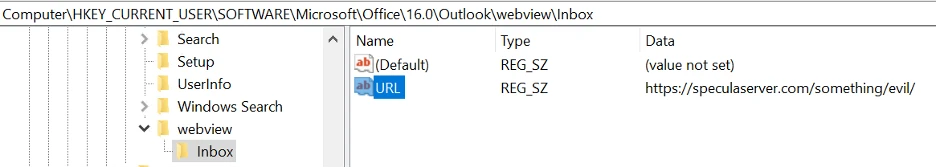
The attacker-controlled Outlook house web page is designed to serve customized VBscript recordsdata that an attacker can use to execute arbitrary instructions on compromised Home windows techniques.
“TrustedSec has been in a position to leverage this particular channel for preliminary entry in tons of of shoppers regardless of the present information and preventions accessible for this method,” TrustedSec stated.
“When a customized house web page is ready by any of the Registry keys outlined by Microsoft of their workaround, Outlook will obtain and show that HTML web page as an alternative of the traditional mailbox aspect (inbox, calendar, despatched, and many others.) when the related tab is chosen.
“From the downloaded HTML web page we’re in a position to run vbscript or jscript inside a privileged context with roughly full entry to the native system as if we have been operating cscript / wscript.exe.”
Whereas a tool first must be compromised to configure the Outlook Registry entry, as soon as configured, attackers can use this method for persistence and to unfold laterally to different techniques.
Since outlook.exe is a trusted course of, it makes it simpler for attackers to evade current software program as instructions are executed.
As U.S. Cyber Command (US CyberCom) warned 5 years in the past, the CVE-2017-11774 Outlook vulnerability was additionally used to focus on U.S. authorities companies.
Safety researchers from Chronicle, FireEye, and Palo Alto Networks later linked these assaults to the Iranian-sponsored APT33 cyber espionage group.
“FireEye first noticed APT34 use CVE-2017-11774 in June 2018, adopted by adoption by APT33 for a considerably broader marketing campaign starting in July 2018 and persevering with for a minimum of a 12 months,” FireEye cybersecurity researchers stated on the time.
