.jpg)
A brand new model of the Android spy ware ‘Mandrake’ has been present in 5 purposes downloaded 32,000 occasions from Google Play, the platform’s official app retailer.
Bitdefender first documented Mandrake in 2020, with the researchers highlighting the malware’s refined spying capabilities and noting that it has operated within the wild since a minimum of 2016.
Kaspersky now reviews {that a} new variant of Mandrake that options higher obfuscation and evasion sneaked into Google Play by way of 5 apps submitted to the shop in 2022.
These apps remained out there for a minimum of a yr, whereas the final one, AirFS, which was probably the most profitable by way of reputation and infections, was eliminated on the finish of March 2024.
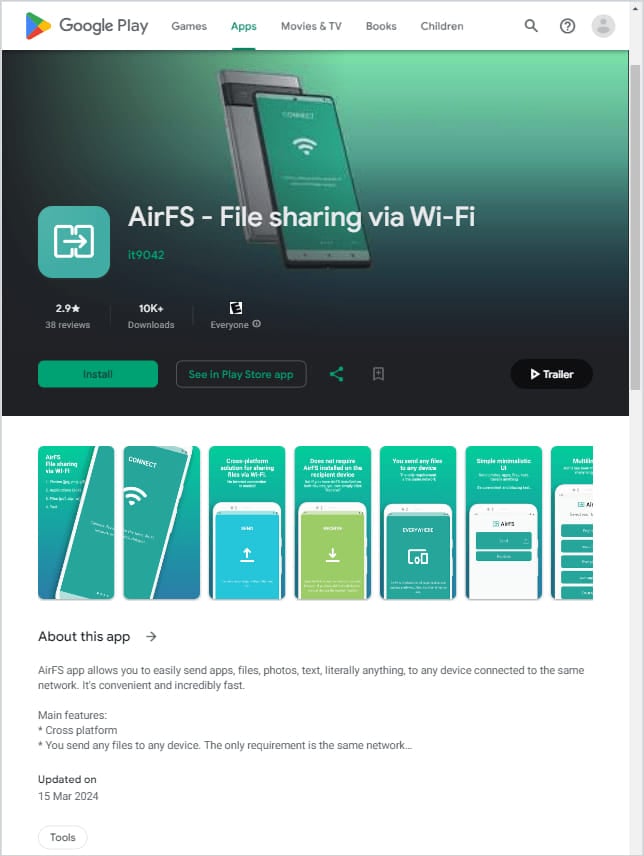
Supply: Kaspersky
Kaspersky recognized the 5 Mandrake-carrying apps as follows:
- AirFS – File sharing by way of Wi-Fi by it9042 (30,305 downloads between April 28, 2022, and March 15, 2024)
- Astro Explorer by shevabad (718 downloads from Could 30, 2022 to to June 6, 2023)
- Amber by kodaslda (19 downloads between February 27, 2022, and August 19, 2023)
- CryptoPulsing by shevabad (790 downloads from November 2, 2022, to June 6, 2023)
- Mind Matrix by kodaslda (259 downloads between April 27, 2022 and June 6, 2023)
The cybersecurity agency says most downloads come from Canada, Germany, Italy, Mexico, Spain, Peru, and the UK.
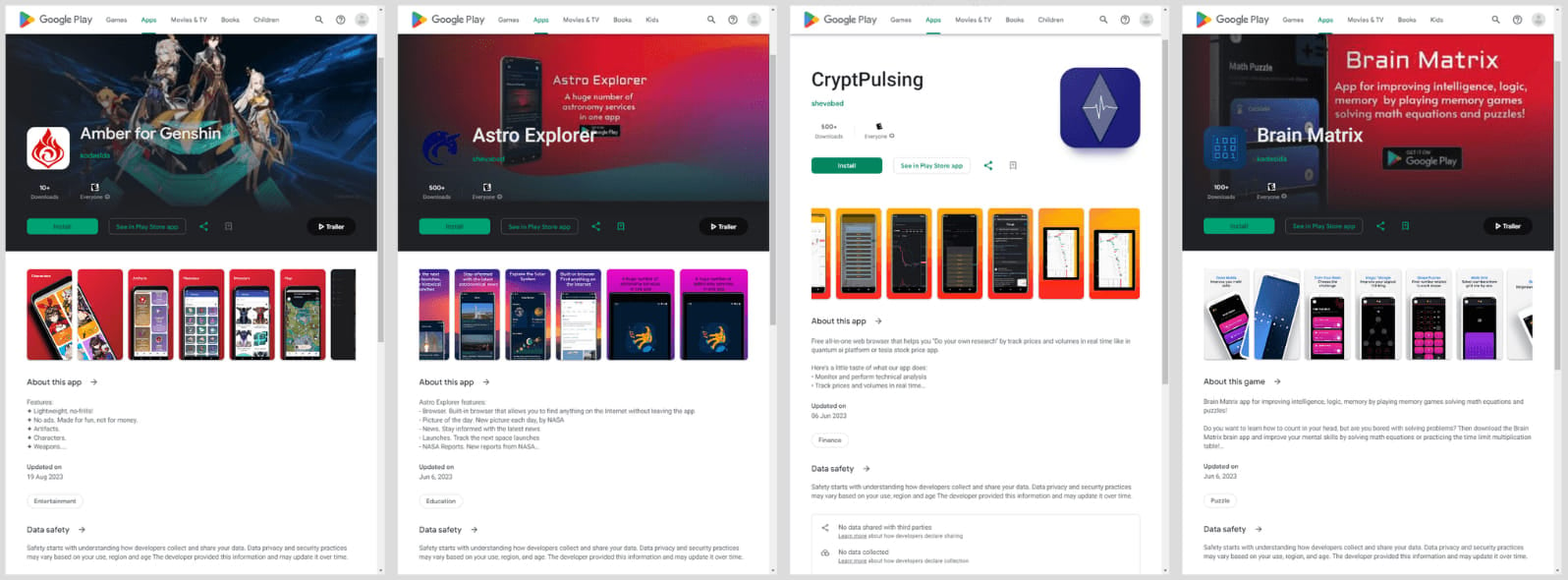
Supply: Kaspersky
Evading detection
Not like typical Android malware, which locations malicious logic within the app’s DEX file, Mandrake hides its preliminary stage in a local library, ‘libopencv_dnn.so,’ which is closely obfuscating utilizing OLLVM.
Upon the malicious app’s set up, the library exports features to decrypt the second-stage loader DEX from its property folder and cargo it into reminiscence.
The second stage requests permissions to attract overlays and masses a second native library, ‘libopencv_java3.so,’ which decrypts a certificates for safe communications with the command and management (C2) server.
Having established communication with the C2, the app sends a tool profile and receives the core Mandrake element (third stage) if deemed appropriate.
As soon as the core element is activated, Mandrake spy ware can carry out a variety of malicious actions, together with information assortment, display recording and monitoring, command execution, simulation of consumer swipes and faucets, file administration, and app set up.
Notably, the risk actors can immediate customers to put in additional malicious APKs by displaying notifications that mimic Google Play, hoping to trick customers into putting in unsafe recordsdata by way of a seemingly trusty course of.
Kaspersky says the malware additionally makes use of the session-based set up technique to bypass Android 13’s (and later) restrictions on the set up of APKs from unofficial sources.
Like different Android malware, Mandrake can ask the consumer to grant permission to run within the background and conceal the dropper app’s icon on the sufferer’s system, working stealthily.
The malware’s newest model additionally options batter evasion, now particularly checking for the presence of Frida, a dynamic instrumentation toolkit in style amongst safety analysts.
It additionally checks the system root standing, searches for particular binaries related to it, verifies if the system partition is mounted as read-only, and checks if growth settings and ADB are enabled on the system.
The Mandrake risk stays alive, and whereas the 5 apps recognized as droppers by Kaspersky are now not out there on Google Play, the malware may return by way of new, harder-to-detect apps.
Android customers are really helpful solely to put in apps from respected publishers, examine consumer feedback earlier than putting in, keep away from granting requests for dangerous permissions that appear unrelated to an app’s operate, and be sure that Play Defend is at all times lively.
