
A safety problem within the newest model of WhatsApp for Home windows permits sending Python and PHP attachments which are executed with none warning when the recipient opens them.
For the assault to achieve success, Python must be put in, a prerequisite which will restrict the targets to software program builders, researchers, and energy customers.
The issue is much like the one affecting Telegram for Home windows in April, which was initially rejected however fastened later, the place attackers might bypass safety warnings and carry out distant code execution when sending a Python .pyzw file by way of the messaging shopper.
WhatsApp blocks a number of file sorts thought-about to hold a threat to customers however the firm tells BleepingComputer that it doesn’t plan so as to add Python scripts to the checklist.
Additional testing by BleepingComputer reveals that PHP recordsdata (.php) are additionally not included in WhatsApp’s blocklist.
Python, PHP scripts not blocked
Safety researcher Saumyajeet Das discovered the vulnerability whereas experimenting with file sorts that could possibly be connected to WhatsApp conversations to see if the applying permits any of the dangerous ones.
When sending a probably harmful file, comparable to .EXE, WhatsApp reveals it and provides the recipient two choices: Open or Save As.
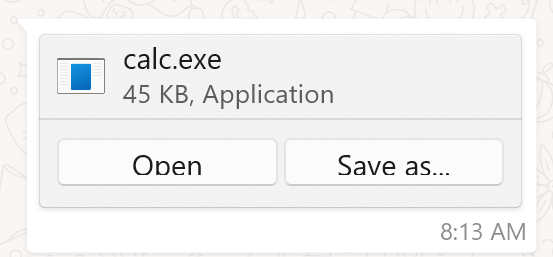
supply: BleepingComputer.com
Nonetheless, when making an attempt to open the file, WhatsApp for Home windows generates an error, leaving customers solely the choice to avoid wasting the file to disk and launch it from there.
In BleepingComputer checks, this habits was in keeping with .EXE, .COM, .SCR, .BAT, and Perl file sorts utilizing the WhatsApp shopper for Home windows. Das discovered that WhatsApp additionally blocks the execution of .DLL, .HTA, and VBS.
For all of them, an error occurred when making an attempt to launch them immediately from the app by clicking “Open.” Executing them was doable solely after saving to disk first.
supply: BleepingComputer
Speaking to BleepingComputer, Das stated that he discovered three file sorts that the WhatsApp shopper doesn’t block from launching: .PYZ (Python ZIP app), .PYZW (PyInstaller program), and .EVTX (Home windows occasion Log file).
BleepingComputer’s checks confirmed that WhatsApp doesn’t block the execution of Python recordsdata and found that the identical occurs with PHP scripts.
If all of the sources are current, all of the recipient must do is to click on the “Open” button on the obtained file, and the script executes.
Das reported the issue to Meta on June 3 and the corporate replied on July 15 saying that the difficulty had already been reported by one other researcher and may have already been fastened.
When the researcher contacted BleepingComputer, the bug was nonetheless current within the newest WhatsApp launch for Home windows, and we might reproduce it on Home windows 11, v2.2428.10.0.
“I’ve reported this problem to Meta by way of their bug bounty program, however sadly, they closed it as N/A. It is disappointing, as this can be a simple flaw that could possibly be simply mitigated,” defined the researcher.
BleepingComputer reached out to WhatsApp for clarification concerning the cause for dismissing the researcher’s report, and a spokesperson defined that they did not see it as an issue on their facet, so there have been no plans for a repair:
“We have learn what the researcher has proposed and admire their submission. Malware can take many various kinds, together with by way of downloadable recordsdata meant to trick a consumer.”
“It is why we warn customers to by no means click on on or open a file from any person they do not know, no matter how they obtained it — whether or not over WhatsApp or another app.”
The corporate consultant additionally defined that WhatsApp has a system in place to warn customers once they’re messaged by customers not of their contact lists, or whom have telephone numbers registered in a distinct nation.
However, if a consumer’s account is hijacked, the attacker can ship to everybody within the contact checklist malicious scripts which are simpler to execute straight from the messaging app.
Moreover, a lot of these attachments could possibly be posted to private and non-private discussion groups, which could possibly be abused by risk actors to unfold malicious recordsdata.
Responding to WhatsApp rejecting the report, Das expressed disappointment with how the challenge dealt with the scenario.
“By merely including the .pyz and .pyzw extensions to their blocklist, Meta can stop potential exploitation by way of these Pythonic zip recordsdata,” the researcher stated.
He added that by addressing the difficulty WhatsApp “wouldn’t solely improve the safety of their customers but additionally show their dedication to promptly resolving safety issues.
BleepingComputer contacted WhatsApp to alert them that the PHP extension can also be not blocked however has not obtained a response presently.
