The marketing campaign begins with an electronic mail and ends with the account being compromised, however there are a number of notable steps all through the an infection chain earlier than the goal enterprise account is totally compromised. Every step follows the identical lure to attract victims in and accumulate delicate data associated to the account. Pictures of the phishing pages will be seen in Determine 2 under.
- E-mail Hyperlink – The phishing emails begin with a hyperlink that’s both hyperlinked to textual content or embedded right into a clickable picture just like the “Confirm” button seen earlier. These hyperlinks are all hosted on the domains Netlify[.]app or Vercel[.]app, that are webhosting providers that the risk actors are abusing to host their phishing websites. In some circumstances, the marketing campaign incorporates a t[.]co, X’s hyperlink shortener, into the an infection chain that simply acts as an extra redirect.
- Step 1: Touchdown Web page – Following the e-mail, customers are met with a touchdown web page that serves no practical function aside from to govern customers into believing it is a professional course of to recuperate their account.
- Step 2: Account Data – The second step harvests Meta account data resembling enterprise electronic mail, web page identify, web page proprietor, electronic mail deal with, cellphone quantity, data associated to monetary data, and up to date journey preparations, and an space to submit an enchantment. A few of this data could appear pointless, however within the case of the risk actors efficiently getting access to an account, this might assist them disrupt Meta’s account restoration course of.
- Step 3: Account Password – The third step is fairly simple, it simply requests that the consumer enter their password. Stolen data on this marketing campaign is exfiltrated to numerous places arrange by the risk actors, one instance is that credentials have been posted to a Telegram bot.
- MFA Bypass Step – This step is what makes this marketing campaign such a high-level and doubtlessly profitable risk. It’s comparatively easy at first look, it simply requests that the consumer inputs their 6-digit or 8-digit code from their authenticator app. As soon as entered, there’s a loading course of that primarily waits lengthy sufficient for a brand new code to be generated after which requests it once more. This extra step is probably going used to make sure that entry to the account has efficiently been stolen.
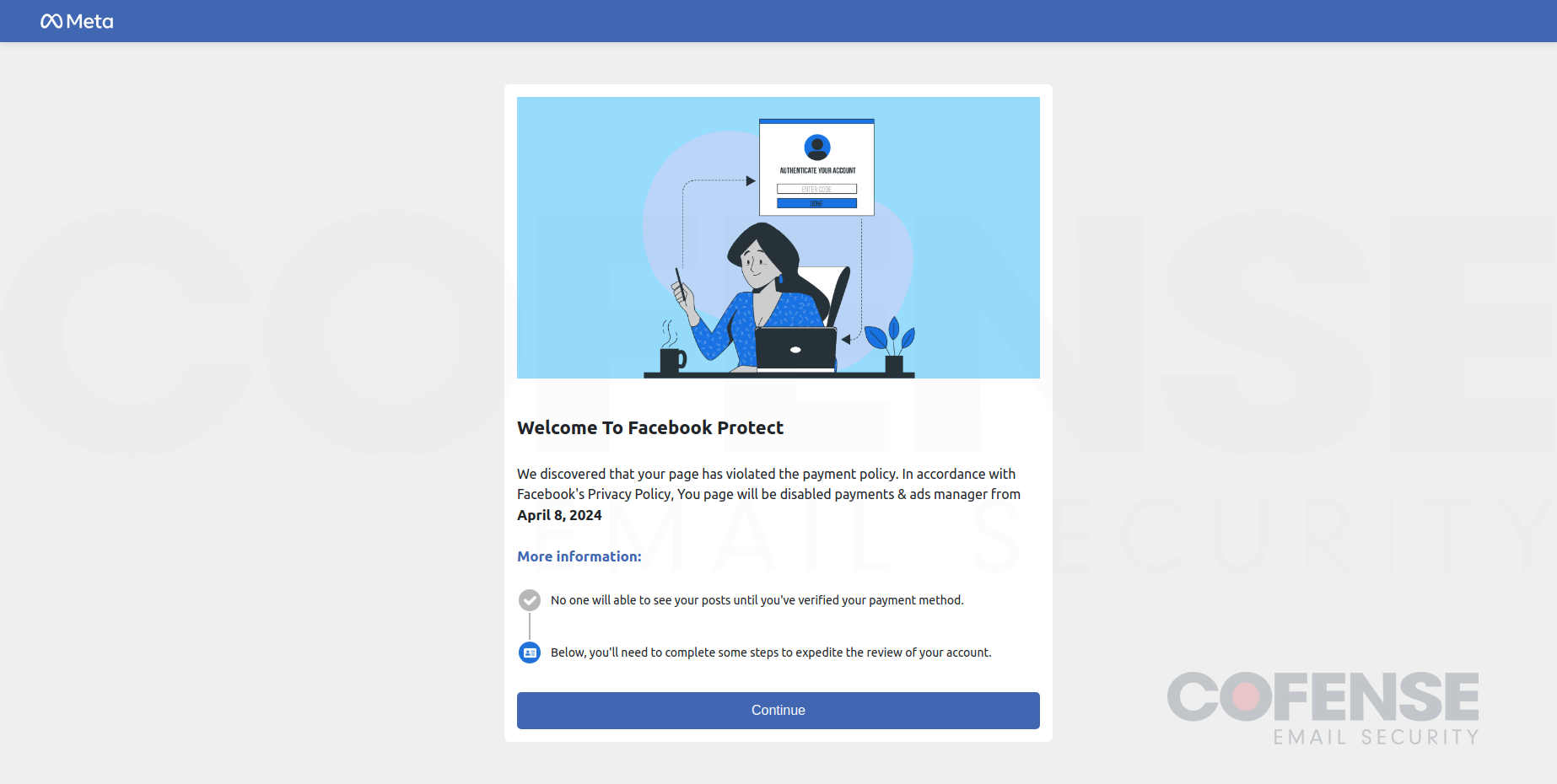

Determine 2: The touchdown web page, the primary web page that customers will see after interacting with the phishing URL.
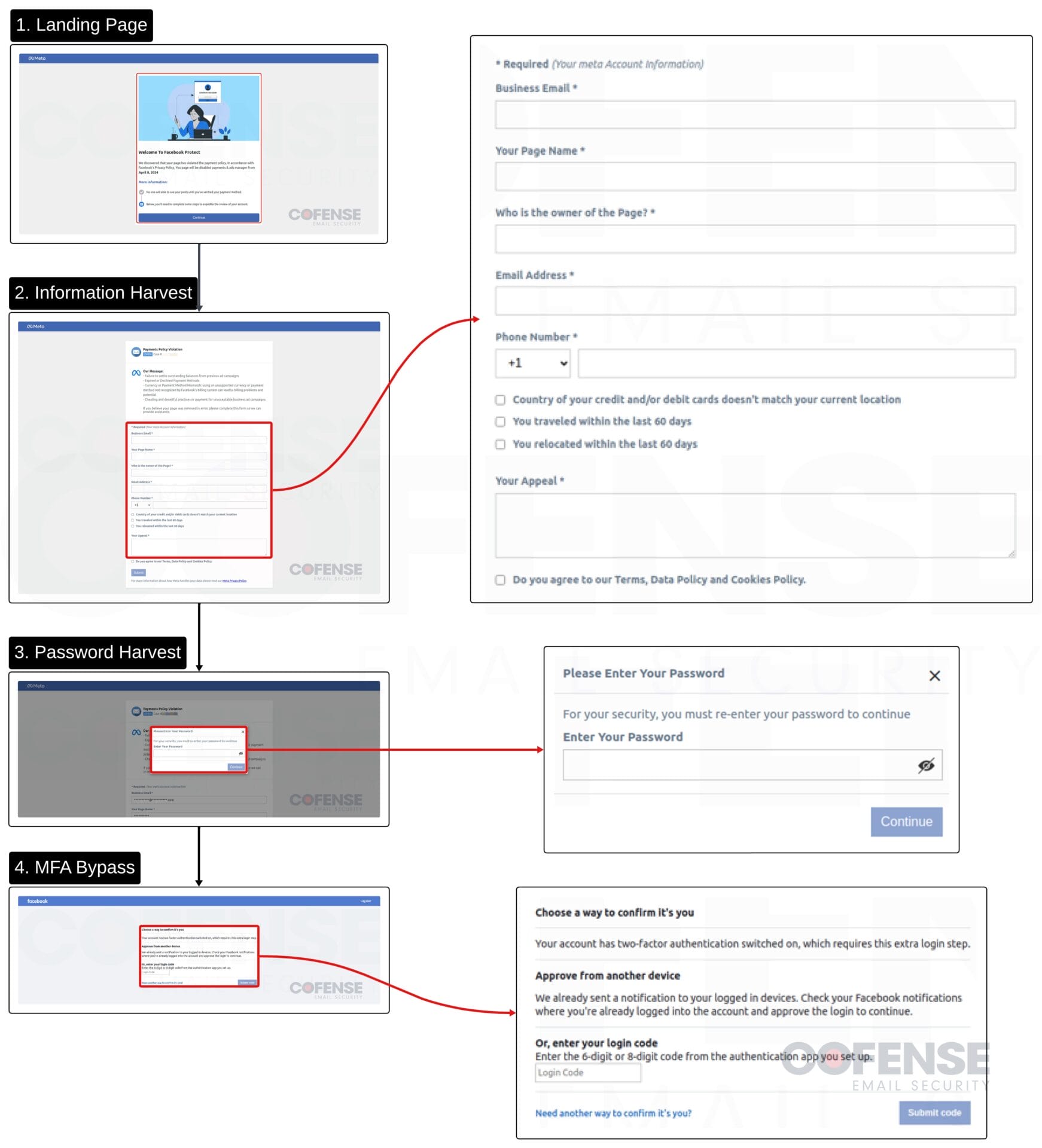

Determine 3: Breakdown of the total phishing an infection chain.
A Deep Evaluation of Menace Actor Infrastructure
Throughout an evaluation, a Cofense risk analyst recognized open entry to tooling used for this marketing campaign hosted on bot1[.]sieulike[.]com. The location incorporates a number of redirects which were translated from Vietnamese to English. These redirects go to areas the risk actors ceaselessly go to like Netlify[.]app to create new hyperlinks, Microsoft electronic mail login for Hotmail, and two spreadsheets; one for income and prices along with one containing knowledge on nations they aim. Most of those are locked behind logins and require entry to be granted by the risk actors.
Particularly, the Revenue / price spreadsheet requires a login to have the ability to entry the spreadsheet. The actual fact that there’s a spreadsheet particularly for prices and income implies that the risk actors are in search of monetary acquire. Whereas that’s apparent for many campaigns, for this one, specifically, it actually proves that the risk actors will make use of an extra assault vector as soon as the enterprise advert account has been compromised.
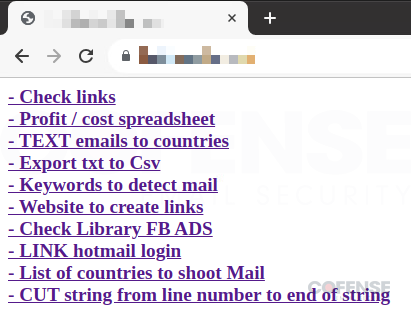

Determine 4: Menace actor sources, infrastructure, and instruments used on this marketing campaign.
The location additionally hosts a number of instruments that present how environment friendly and superior these risk actors are. These instruments range from merely changing enter textual content right into a CSV to producing full phishing emails. A breakdown of among the extra notable instruments which might be listed in Determine 4:
- Verify Hyperlinks (Figures 5 and 6) – All the indicators of compromise you could possibly ever need are conveniently included on this instrument. Not solely does it include an extended record of phishing URLs which might be actively getting used, nevertheless it additionally permits the risk actors to routinely verify if the hyperlinks are nonetheless reside or have been taken down.
- TEXT emails to nations (Determine 7) – This can be a distinctive instrument used to routinely generate phishing emails primarily based on standards entered by the risk actors. The risk actors choose one of many 19 totally different nations they aim, the theme they need the e-mail to be (coverage violation or copywriting infringement), the phishing hyperlink they wish to use, after which it generates a textual content model of the e-mail and the headers.
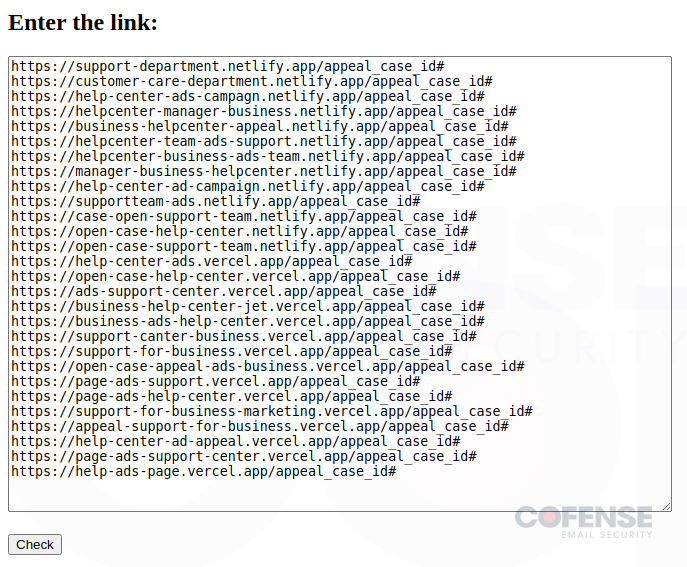

Determine 5: Menace actor instrument to enter malicious hyperlinks to verify in the event that they’re lively.
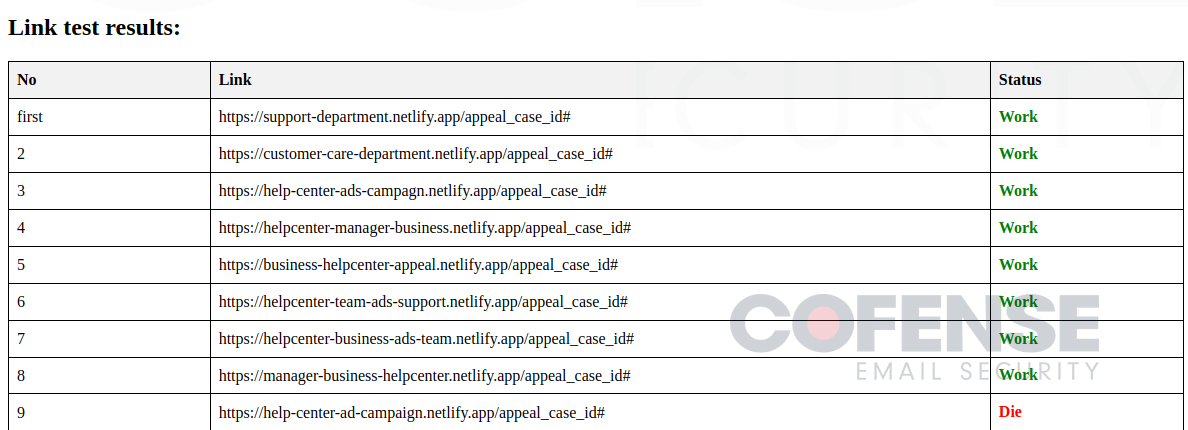

Determine 6: Outcomes from the URL enter displaying if lively or useless.
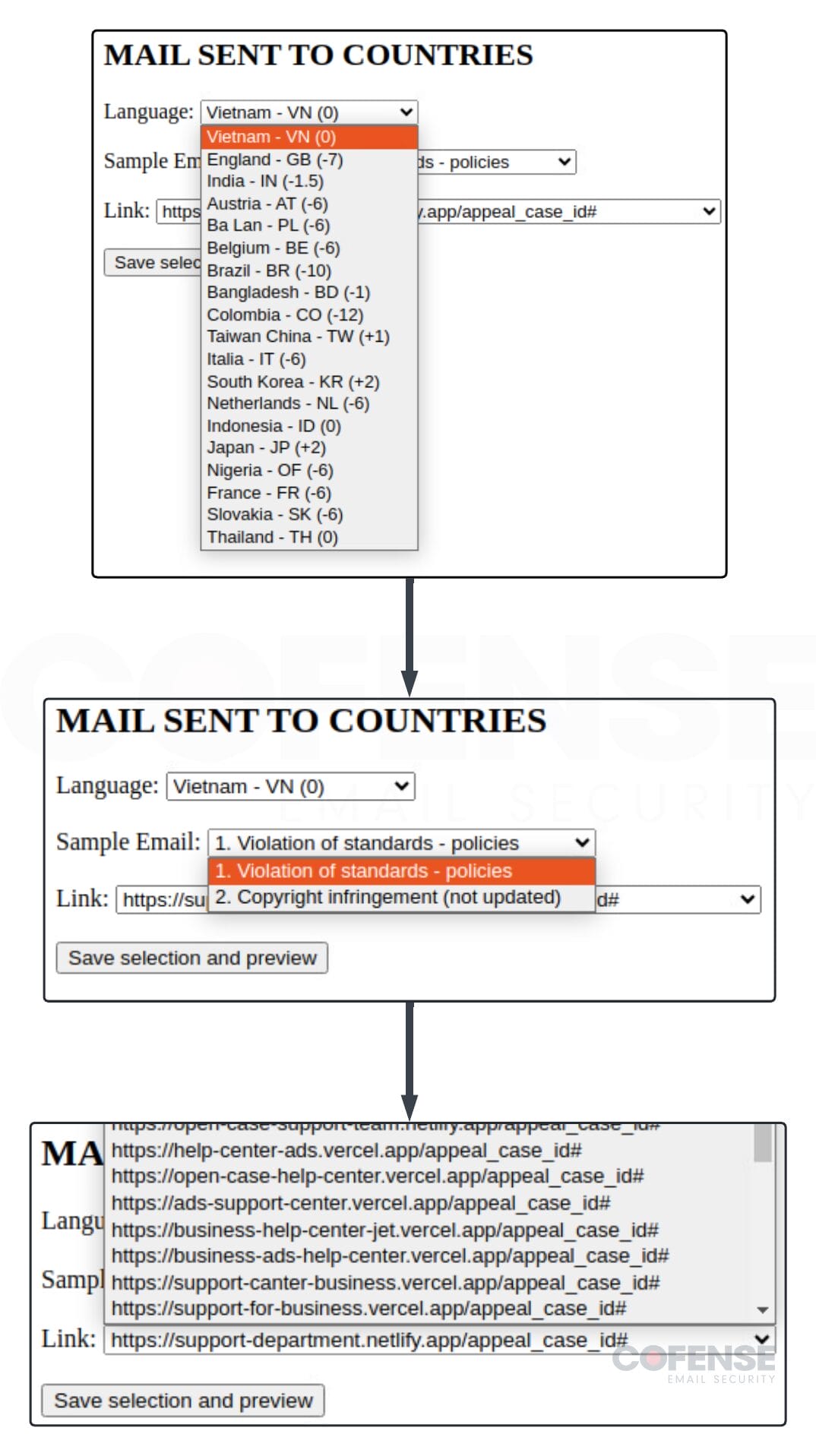

Determine 7: Menace actor instrument to generate phishing emails for this marketing campaign.
Meta Spoofing within the Menace Panorama
Cofense studies on a major quantity of credential phishing emails day by day that had been uncovered inside an enterprise consumer’s inbox. Of these emails, Meta is the second most spoofed model seen within the first quarter of 2024. Out of the campaigns spoofing Meta, emails from this marketing campaign make up a great portion of the quantity. Determine 8 under exhibits the highest 5 manufacturers spoofed in Credential Phishing campaigns seen by Cofense in Q1 of this yr. Meta follows behind Microsoft, which is well-known for being spoofed in a excessive proportion of phishing emails because of the common use of Microsoft electronic mail providers.
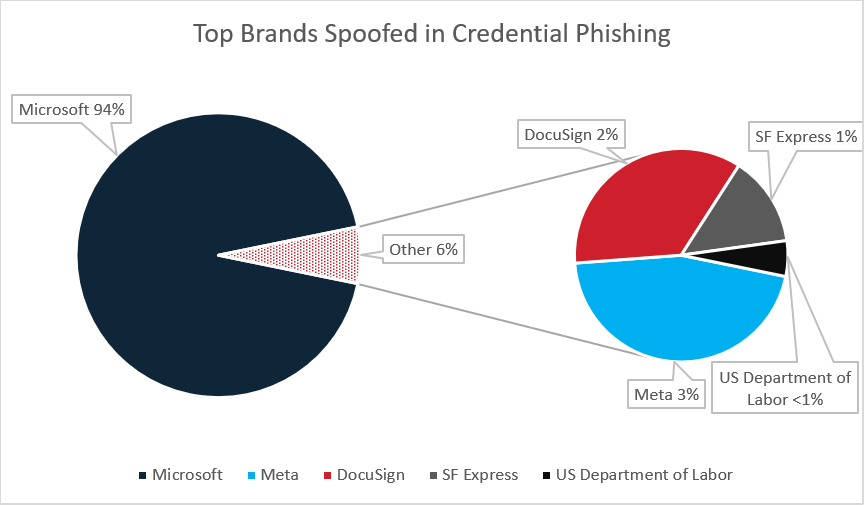

Determine 8: Prime manufacturers spoofed in Credential Phishing campaigns seen by Cofense in Q1 2024.