Tunneling providers, also referred to as “ingress-as-a-service” presents had been initially designed to facilitate safe communication over untrusted networks. Over the previous a number of years they’ve more and more develop into instruments of alternative for cybercriminals. Providing a cloak of anonymity and encrypted pathways, these providers have emerged as an choice that permits attackers to obfuscate their actions and bypass typical safety measures. On this weblog, we’ll clarify how they work, discover the kinds of cyber threats they permit, and supply some mitigation methods to fortify your defenses in opposition to them.
Ingress-as-a-service vs. reverse proxies vs. tunnel applied sciences
It is very important perceive the distinction between ingress-as-a-service, reverse proxies and tunneling applied sciences to correctly perceive their options and limitations, in addition to to evaluate the potential safety impacts from their utilization.
Ingress-as-a-service platforms, exemplified by providers like Ngrok, primarily give attention to offering exterior entry to inner assets with out requiring advanced community configurations. These providers sometimes supply short-term URLs or domains that route site visitors to particular ports or purposes hosted on native servers.
In distinction, reverse proxies like NGINX act as intermediaries between purchasers and servers, offering options like load balancing, caching, and SSL termination. They’re extra configurable and are sometimes utilized in manufacturing environments to reinforce efficiency and safety.
Then again, tunneling applied sciences equivalent to GRE (Generic Routing Encapsulation) and IPSec (Web Protocol Safety) create safe pathways for information transmission over untrusted networks. Whereas they will additionally facilitate exterior entry to inner assets, they’re primarily designed for establishing safe connections between networks or hosts and encrypting information in transit.
Every of those applied sciences serves distinct functions and needs to be chosen primarily based on the precise necessities of the community structure and safety wants.
How Do Tunnel Companies Work?
Tunneling or Ingress as a Service providers equivalent to ngrok, LocalXpose, and Pinggy, present a safe technique to expose native servers behind NAT (Community Tackle Translation) and firewalls to the general public Web. They create a tunnel between a person’s machine and a publicly accessible endpoint, permitting for safe communication between the 2. This facilitates testing and sharing of providers hosted on native machines with out the necessity to register domains, purchase webhosting providers, or undergo advanced community configurations.
Right here’s how the method sometimes works with a service like Ngrok as “service supplier”, its customers as “clients,” and an Web end-user as “Web person”:
- The client installs a command line shopper software program supplied by the service supplier on their laptop or server. This shopper software program permits the service buyer to customise their providers;
- Upon set up, the client should present credentials to authenticate themselves on the service supplier’s platform. These credentials are used anytime the client requests modifications to their service configurations;
- The client makes use of the command line software program to configure native ports and protocols to be uncovered to the Web by way of the service supplier’s platform. For instance, they will make their port TCP/3306 obtainable to computer systems outdoors their non-public community by way of the tunneling service;
- The service supplier receives the configuration request and allocates assets which will embrace a FQDN, protocol and port on its infrastructure;
- Visitors directed to the allotted FQDN and port over the anticipated protocol is robotically forwarded to the client’s laptop;
- The service supplier relays information between Web customers and the client. This site visitors may be encrypted utilizing TLS, for instance, relying on the client’s preferences;
- The actual community and geographical location of the client is hidden and by no means disclosed to Web customers;
- A number of Web customers can entry assets exported by the client on the similar time;
- The service supplier additionally permits for authentication, site visitors management and different effective grain configurations by the client.
Options and Suppliers
The first promoting level of the business variations of those providers . Most declare that the method solely takes minutes, typically with no obtain required. Different touted options embrace system-generated or customized domains, assist for a number of protocols, site visitors and account logging, GUI or CLI interfaces, and instantaneous SSL certificates. A free choice is frequent, although, these normally solely supply a self-expiring area (15-60 minutes) and will produce other limitations associated to supported protocols and bandwidth. Paid plans are very inexpensive, with costs starting from US$2.50 to $20 monthly, relying on the supplier and options.
A easy Google search returns outcomes for firms each new and well-established which have entered this ingress-as-a-service market. There’s additionally an abundance of open supply do-it-yourself-hosting choices. The highest end result for the time period tunneling providers is the highly regarded awesome-tunneling GitHub repository by person anderspitman described as “Listing of ngrok/Cloudflare Tunnel options and different tunneling software program and providers. Concentrate on self-hosting.” The repository lists greater than 60 options.
What’s the purpose of those particulars? To display that the choices for tunneling are so quite a few and technically diversified that there isn’t any technique to observe or block all of them. This is the reason understanding how these providers function is crucial for successfully safeguarding networks in opposition to potential threats.
Professional Use Circumstances
Tunneling providers supply a variety of use circumstances throughout numerous industries and situations. Listed below are some examples:
Growth and Testing: Builders can expose their work-in-progress net purposes, APIs, and different providers to collaborators or purchasers for suggestions and testing while not having to deploy it to a manufacturing server.
Distant Entry: Allow distant entry to gadgets, equivalent to cameras, IoT gadgets, or residence servers, which are situated behind firewalls or NAT routers.
Bypassing Community Restrictions: Tunneling providers can bypass censorship or different restrictions by routing site visitors by way of encrypted tunnels, permitting customers to entry restricted content material and providers securely.
Penetration Testing and Safety Analysis: Safety professionals or safety analysis to simulate assaults, check safety controls, or analyze community site visitors.
File Switch and Information Sharing: Facilitate safe file switch and information sharing between events by creating encrypted tunnels for transmitting information and information over the Web.
Not-So-Professional Use Circumstances
Through the years, this device has garnered notoriety for its function in facilitating information exfiltration, phishing, ransomware assaults, and covert communication channels. Listed below are some threats that may be hosted or assisted utilizing tunnels:
Command and Management (C2) Servers: Tunnels set up safe communication channels between compromised techniques and their command-and-control servers.
Phishing: Phishing web sites are hosted on a nasty actor’s native machine and uncovered to the Web through a tunnel.
Information Exfiltration: Tunneling providers present a safe and encrypted channel for exfiltrating delicate information from compromised techniques.
Malware Distribution: Attackers can distribute malware by internet hosting malicious payloads on their native machines and exposing them by way of a tunnel.
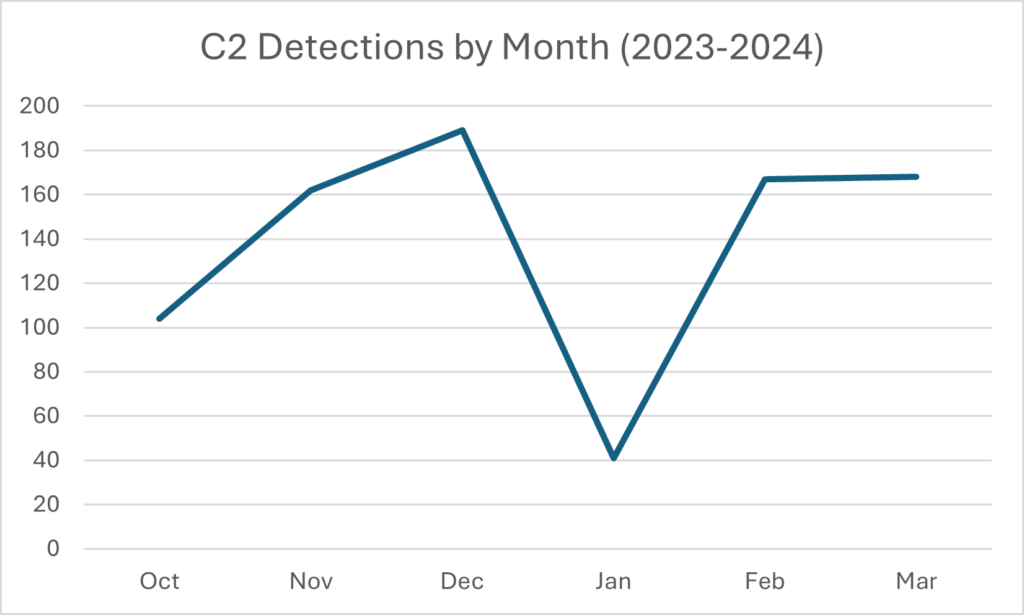
Present Development: C2s Hosted by Ngrok
The inspiration for this weblog was an uptick within the variety of C2s discovered hosted at Ngrok domains (*.ngrok-free.app and * ngrok.io) since This autumn 2023. The codecs range, however develop into simply recognizable after getting seen among the URLs:
tcp://ed0c-2604-a880-800-10-00-bf8-8001[.]ngrok.io:18237/
tcp://ssh.6be0b042ac77[.]ngrok.io:19599/
tcp://4.tcp.eu[.]ngrok.io:11855/
tcp://mailgate.6be0b042ac77[.]ngrok.io:18335/
tcp://pop.2b287b46[.]ngrok.io:18335/
tcp://mailgate.9f50d37b[.]ngrok.io:17888/
tcp://panther-tender-ghost[.]ngrok-free.app:17888/
tcp://4118-209-105-242-243[.]ngrok-free.app:17888/
tcp://4271-1-10-161-113[.]ngrok-free.app:17888/
Two particular malware households collectively account for greater than 96% of all noticed Command and Management (C2) URLs: njRAT and Nanocore RAT. When taking a look at exercise from October 2023 to April 2024, we seen a big lower in exercise in January 2024.
| Malware Household |
P.c of Ngrok C2s |
Related Risk Actor(s), per malpedia |
| AsyncRAT | 0.23% | Numerous, publicly obtainable |
| DCRAT | 0.23% | Numerous, offered on underground boards |
| Ghost RAT | 2.60% | EMISSARY PANDA, Hurricane Panda, Lazarus Group, Leviathan, Purple Menshen, Stone Panda |
| Nanocore RAT | 29.75% | APT33, The Gorgon Group |
| njRAT | 67.08% | AQUATIC PANDA, Earth Lusca, Operation C-Main, The Gorgon Group |
| Remcos | 0.11% | APT33, The Gorgon Group, UAC-0050 |
To discover choices for combatting tunneling abuse, we submitted a few of these C2 URLs to Ngrok for the primary time. They’ve a few choices for reporting abuse:
- Through an electronic mail tackle discovered on their abuse web page
- An abuse reporting API launched on their abuse web page: “In case you are an institutional fraud prevention agency, now we have made reporting content material for elimination simpler and extra environment friendly by offering a direct API integration for submitting studies. If you happen to anticipate to report a big quantity of abuse, please attain out to us on to inquire about entry to combine straight with our abuse reporting API.”
Their response and subsequent elimination had been nearly speedy. In addition they adopted as much as present particulars in regards to the API and to welcome extra submissions. This speedy, proactive method to minimizing abuse of their service was spectacular and refreshing.
Tightening Your Defenses Towards Tunneling Abuse
Organizations can considerably scale back the danger posed by this and comparable instruments once they perceive how malicious actors can exploit tunneling. Defending in opposition to this menace requires a multi-faceted method that encompasses proactive measures and constant monitoring:
- Community Monitoring and Evaluation
-
- Implement complete community monitoring to detect uncommon outbound connections.
- Make use of community evaluation instruments that may establish patterns indicative of tunneling or information exfiltration makes an attempt. This consists of sudden spikes in information switch to unfamiliar exterior addresses.
- In case your group doesn’t use these providers, tagging site visitors or completely blocking it may be an efficient measure.
- Endpoint Detection and Response (EDR)
-
- Make the most of EDR options to detect and reply to suspicious actions on endpoints, together with the unauthorized set up or execution of tunneling instruments.
- Configure EDR techniques to alert directors of makes an attempt to switch firewall settings or set up connections which are indicative of a tunneling service getting used.
- Software Whitelisting
-
- Implement software whitelisting insurance policies to forestall the execution of unauthorized purposes until it’s accredited for legit use circumstances inside the group.
- Usually replace whitelists to incorporate new legit instruments and evaluation the record to take away any which are now not wanted or pose a safety danger.
- Consumer Consciousness and Coaching
-
- Educate workers in regards to the dangers related to tunneling providers and the potential for his or her misuse. Embrace info on methods to acknowledge phishing makes an attempt or social engineering techniques that might result in the set up of such instruments.
- Conduct common coaching periods to enhance the safety consciousness of workers, specializing in the significance of reporting suspicious actions.
- Strict Entry Controls
-
- Implement strict entry controls and section networks to restrict the power of an attacker to maneuver laterally, even when they handle to ascertain a tunnel.
- Use multi-factor authentication (MFA) and powerful password insurance policies to cut back the danger of credential theft and unauthorized entry to techniques that may very well be used to deploy a tunneling device for malicious functions.
- Common Safety Audits and Penetration Testing
-
- Conduct common safety audits and penetration testing to establish vulnerabilities that may very well be exploited to put in and use these instruments maliciously. This could embrace assessments of each inner and exterior defenses.
- Evaluation and replace incident response plans to incorporate procedures for detecting, isolating, and eradicating unauthorized tunneling providers.
- Collaboration and Sharing of Risk Intelligence
-
- Take part in industry-specific menace intelligence sharing platforms to remain knowledgeable in regards to the newest techniques, methods, and procedures (TTPs) utilized by menace actors, together with the misuse of tunneling providers. Share insights and indicators of compromise (IoCs) associated to unauthorized providers use with friends and cybersecurity communities to assist in collective protection efforts.
In Conclusion
Because the digital panorama continues to evolve, the abuse of tunneling providers stays a persistent and evolving menace. Nonetheless, by taking the time to study this menace, remaining vigilant, implementing sturdy safety measures, and fostering a tradition of cybersecurity consciousness, companies can safeguard their networks and information in opposition to the clandestine actions of malicious actors.
Whereas numerous strategies exist to counter this menace, using menace intelligence presents an instantaneous, proactive method to detection and mitigation. IOCs can assist groups swiftly establish tunneling connections and related exercise of recognized phishing campaigns and C2 infrastructure. For extra details about Malware Patrol’s menace information feeds that cowl this type of exercise, click on right here.