By Nathaniel Raymond
Microsoft Workplace paperwork within the Office365 software program suite have develop into a mainstay for a lot of customers who must create paperwork for enterprise stories, faculty essays, resumes, important notetaking, and even strategic analyses. Workplace paperwork supply a variety of not solely textual content however knowledge modifying software program options that embody applied sciences that introduce algorithmic logic by way of a macro or, extra not too long ago, with the combination of Python scripting being added to Excel for a extra dynamic and logical approach of decoding, modifying, and displaying knowledge. Nonetheless, this versatility additionally makes them a possible cyber weapon, able to distributing credential phishing and malware. These threats can vary from easy hyperlinks or embedded QR codes inside a doc to extra advanced threats, such because the “Microsoft Workplace Reminiscence Corruption Vulnerability” or CVE-2017-11882, which might and is usually paired with the “Microsoft Workplace/WordPad Distant Code Execution Vulnerability” or CVE-2017-0199.
Moreover, risk actors can even use the native programming language for Workplace paperwork named Visible Fundamentals for Functions, or VBA, to create malicious macros that execute as soon as the doc is opened. Understanding these distribution vectors, corresponding to sending paperwork by way of e mail or sharing them by way of cloud providers, is essential for companies to make sure that the correct and relevant customers receive them. Due to this fact, this distribution vector has led to Workplace paperwork being despatched by way of e mail attachments or embedded hyperlinks to the doc hosted on cloud internet hosting providers, changing into frequent in emails. Risk actors use this commonality together with designing paperwork in a number of malicious methods to distribute credential phishing or malware whereas giving the e-mail marketing campaign a way of legitimacy via spoofing manufacturers and themes. Given the potential hurt these threats may cause, it’s empowering for companies to concentrate on the frequent threats that may land in a consumer’s inbox utilizing Workplace paperwork.
Key Factors
- Microsoft Workplace paperwork are invaluable and versatile instruments for numerous customers who use them for varied functions in enterprise and private environments.
- Workplace doc applied sciences can ship advanced designed malware distribution instruments utilizing exploits corresponding to CVE-2017-11882 and CVE-2017-0199 or use the built-in VBA language for auto-executing macros.
- In distinction, Workplace paperwork can be easy of their method solely to ship a hyperlink or QR code embedded into the doc.
- Risk actors, well-versed within the frequent follow of doc e mail attachments or embedded hyperlinks to an Workplace doc, exploit this familiarity to their benefit. They craft emails which will seem reliable, thereby rising the danger to customers.
Hyperlinks in Workplace Paperwork
Embedded hyperlinks in Workplace paperwork are a standard tactic utilized by risk actors of various expertise to distribute malware and credential phishing. Nonetheless, hyperlinks in Workplace paperwork have usually been seen at Cofense as a method of distributing extra credential phishing than malware. As one may think, Workplace paperwork could be created in varied seems and codecs so as to add a layer of believability that the doc is reliable. Workplace paperwork can vary from plain textual content on the web page to extra inventive makes use of of embedded photographs and shapes to obfuscate the embedded hyperlink. Determine 1 is a credential phishing e mail with an RTF attachment created in Microsoft Phrase that has been seen in a number of customers’ inboxes, delivering a plain-looking doc containing a hyperlink to a Microsoft phishing web page, as proven in Determine 2.
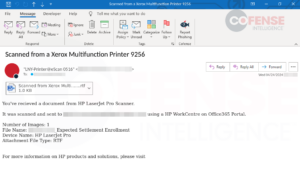

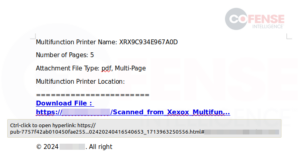

Determine 1: Credential phishing e mail with an embedded hyperlink inside connected RTF Phrase doc.
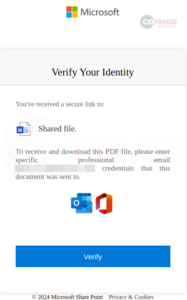

Determine 2: Microsoft credential phishing web page.
As acknowledged, malware is simply as simply distributed as credential phishing relating to hyperlinks in Workplace paperwork. Determine 3 exhibits an e mail from a DarkGate malware marketing campaign with an Excel worksheet attachment containing a hyperlink that delivers a JavaScript dropper, which then downloads and runs the DarkGate malware. In distinction to Determine 1, the Excel doc is a bit more inventive in its method to inviting customers to click on the embedded hyperlink, taking time to try to cover the embedded hyperlink.
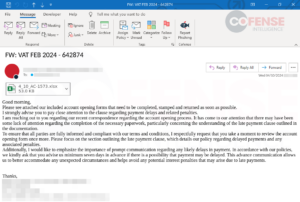

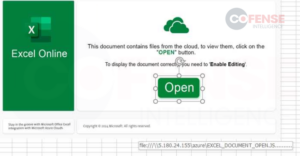

Determine 3: DarkGate e mail with an embedded hyperlink inside an connected Excel doc.
QR Codes in Workplace Paperwork
QR codes are an enigma with regards to cyber threats. That’s, a consumer should exhibit a sure degree of effort when interacting with QR codes, as they aren’t as accessible as a hyperlink or autonomous as a macro or CVE-2017-11882/0199. Since QR codes should not as simple as clicking a hyperlink or downloading and opening an attachment, on prime of getting to make use of a tool able to scanning a QR code, can place QR codes right into a place the place a consumer can query the validity of the QR code extra simply. In distinction, QR codes supply extra deception and obfuscation defenses from autonomous safety, particularly when embedded into photographs or information. This will make detecting the QR code’s underlying knowledge tougher, making it simpler to bypass safety suites corresponding to safety e mail gateways or (SEGs). Regardless of the mysticism surrounding the QR code in cyber threats, they’re a major risk that Cofense has seen take off in reputation, written about in earlier blogs. Workplace paperwork are not any exception when delivering a malicious QR code, as proven in Determine 4.
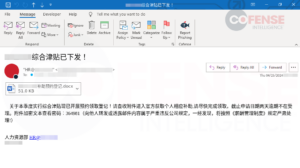



Determine 4: Credential Phishing e mail with an embedded QR code inside an connected password-protected Phrase doc.
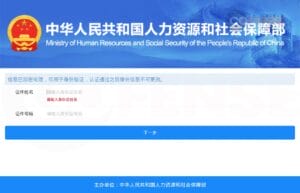

Determine 5: MOHRSS credential phishing web page.
Workplace Macros
In at present’s world, automation is rising exponentially with every passing yr, and much more so with the rise of synthetic intelligence. Workplace paperwork are not any totally different; automation could also be required to assist scale back handbook repetition when creating paperwork. Enter Visible Primary for Functions or just VBA. This built-in programming language helps customers by permitting algorithmic logic, referred to as a macro, to be carried out to boost consumer and enterprise effectivity. Nonetheless, risk actors can even use this highly effective automation to ship all method of malware.
Beginning with Determine 6, we see a plain and easy e mail with an connected Microsoft Phrase doc. If we conduct static analyses on the malicious doc, we’ll discover it’s laced with a malicious macro written with the built-in VBA language. This macro is ready to execute as soon as the consumer has opened the file. That is clear with the “Sub AutoOpen()” operate in the beginning of the macro. This makes these paperwork extraordinarily harmful because it takes a consumer little effort to begin the an infection course of. Nonetheless, not all is misplaced if a consumer does occur to open an attachment with a macro-laden workplace doc.
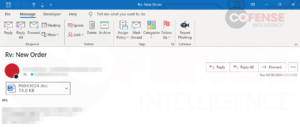

![]()
![]()


Determine 6: Electronic mail and static evaluation of the file that reveals malicious VBA code.
In June 2022, in response to this risk, Microsoft rolled out an replace to its Workplace merchandise that blocked macros from working by default. Because of this if a consumer have been to obtain and open an Workplace doc containing a macro, they’d be met with a banner that warned them of any macro contained in the paperwork and allowed them to allow it in the event that they so select, as proven in Determine 7.
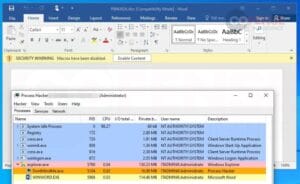

Determine 7: Macro-laden Workplace Phrase doc with macro execution disabled.
Nonetheless, if the consumer chooses to “Allow Content material,” primarily letting the macro run, it’ll begin the an infection course of. Since VBA is a programming language built-in into Workplace paperwork, there are lots of potential methods the doc can ship malware. Nonetheless, on this particular pattern, proven in Determine 8, we will see that PowerShell is used to obtain and run the primary payload at a OneDrive URL utilizing an “IEX” or Invoke-Expression PowerShell command to deal with and run the downloaded knowledge as code. The macro then has a second-stage payload, proven in Determine 6, the place the remainder of the executable knowledge is hosted.
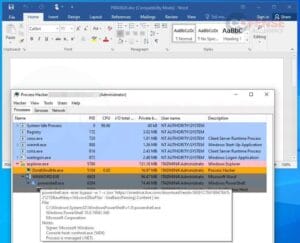

Determine 8: Macro-enabled doc working PowerShell instructions to additional an infection.
The macro-laden Workplace doc was largely made common by the Emotet group, which primarily used these macro techniques to distribute the Emotet malware. Thus, Workplace macros have been one of the vital common supply mechanisms by quantity noticed by Cofense. Though macro-laden Workplace paperwork are a robust avenue to distribute malware requiring the least quantity of consumer effort to execute, they aren’t as common as different supply mechanisms at present, corresponding to CVE-2017-11882 or CVE-2017-0199 exploits, because of a major a part of the Emotet malware shut down by legislation enforcement entities.
Workplace Doc Vulnerabilities
CVE-2017-11882
The “Microsoft Workplace Reminiscence Corruption Vulnerability” or CVE-2017-11882 is a vulnerability that makes use of the Workplace built-in equation editor, which permits LaTeX graphical mathematical equations to be displayed in a doc. The equation editor’s buffer overflow vulnerability permits malicious code to be injected into this system and executed as soon as the consumer has opened the doc, setting the hassle for executing the malicious code on the identical ranges as executing macros. In distinction to macros, the vulnerability doesn’t have default defenses like macros that disallow automated macro execution by default. This locations vulnerability in a excessive state of recognition as a wonderful various to macros.
Cofense has noticed that CVE-2017-11882 vulnerability is a wildly common supply mechanism alternative amongst risk actors. This reputation is exacerbated by open-sourced instruments which will enable for autonomously creating Workplace paperwork containing the vulnerability, which could be discovered merely utilizing a search engine. Looking for the vulnerability reveals these instruments, just like the examples proven in Determine 9, are available to everybody wanting to make use of the vulnerability. Word that these open-sourced instruments showcased shouldn’t be thought-about the de facto risk actor tooling relating to these vulnerabilities. These examples solely showcase how a risk actor with a reasonable to excessive diploma of ability can create scripts or packages that enable for autonomously creating Workplace paperwork containing both vulnerability.
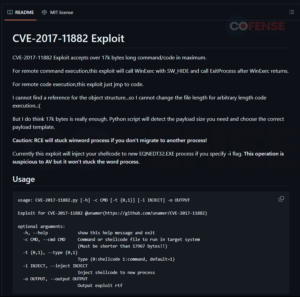

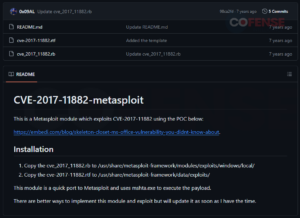

Determine 9: Open-sourced instruments to create Workplace paperwork containing the CVE-2017-11882 vulnerability.
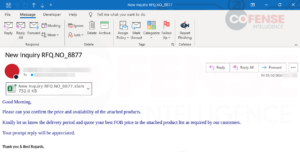





Determine 10: Hooked up Excel doc containing the CVE- 2017-11882 vulnerability delivering Agent Tesla Keylogger.
CVE-2017-0199
The “Microsoft Workplace/WordPad Distant Code Execution Vulnerability” or CVE-2017-0199 permits embedded malformed Microsoft HTML Functions, or HTA, information inside RTF or wealthy textual content information to execute distant code to retrieve payloads from distant assets to additional an infection. A kind of payloads is usually that of paperwork containing the CVE-2017-11882 vulnerability. Very like the CVE-2017-11882 vulnerability, CVE-2017-0199 can be common resulting from entry to open-sourced instruments or the expert creation of such instruments, corresponding to these exhibited in Determine 11 and the truth that it takes little effort for the consumer to open the doc, akin to auto executing macros.
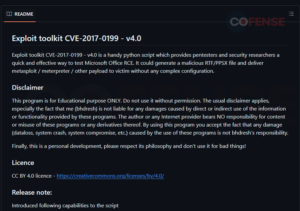

Determine 11: Open-source instrument for creating Workplace paperwork containing the CVE-2017-0199 vulnerability.
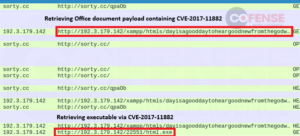



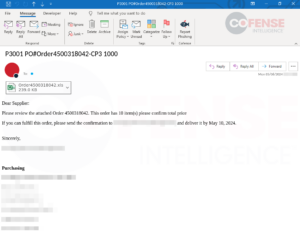

Determine 12: Hooked up Excel doc delivering FormBook by way of CVE-2017-0199 to CVE-2017-11882 obtain chain.