
An enormous phishing marketing campaign dubbed “EchoSpoofing” exploited now-fixed, weak permissions in Proofpoint’s e mail safety service to dispatch thousands and thousands of spoofed emails impersonating large entities like Disney, Nike, IBM, and Coca-Cola, to focus on Fortune 100 firms.
The marketing campaign began in January 2024, disseminating a median of three million spoofed emails day by day and reaching a peak of 14 million emails in early June.

Supply: Guardio Labs
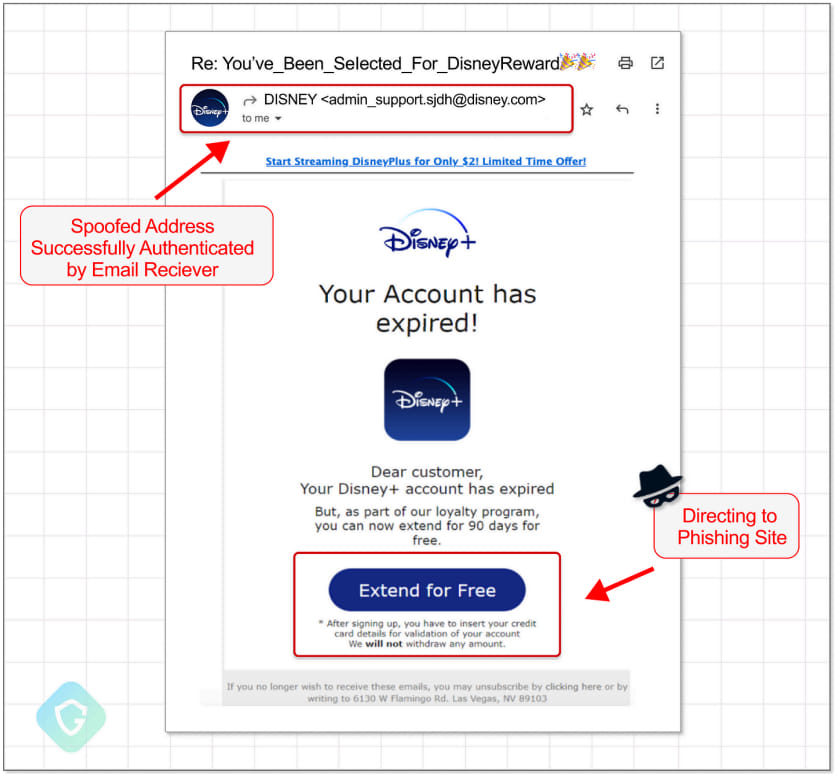
The phishing emails have been designed to steal delicate private data and incur unauthorized fees. In addition they included correctly configured Sender Coverage Framework (SPF) and Area Keys Recognized Mail (DKIM) signatures, making them seem genuine to the recipients.

Supply: Guardio Labs
Guardio Labs helped uncover the phishing marketing campaign and safety hole in Proofpoint’s e mail relay servers. In Might 2024, they notified the agency and helped them repair it.
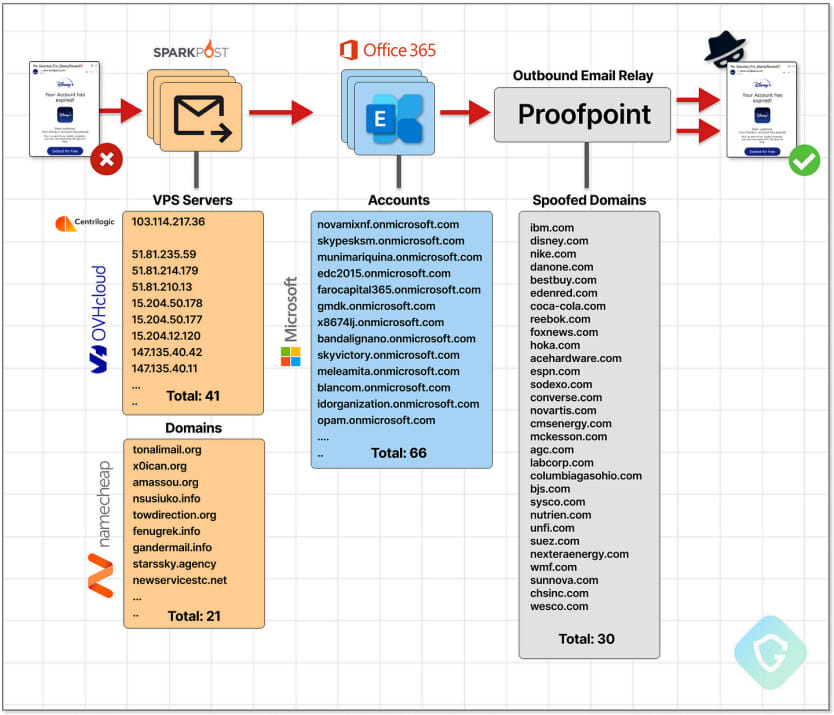
The EchoSpoofing marketing campaign
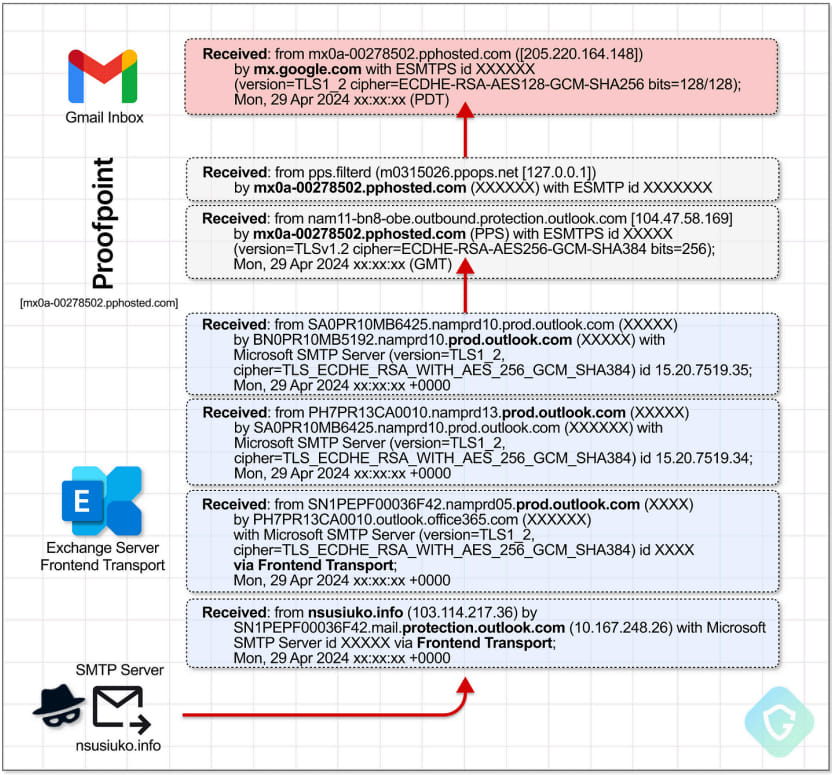
To conduct the marketing campaign, menace actors arrange their very own SMTP servers to create spoofed emails with manipulated headers after which relayed them by Proofpoint’s relay servers utilizing compromised or rogue Microsoft Workplace 365 accounts.
The attackers used Digital Personal Servers (VPS) hosted by OVHCloud and Centrilogic to ship these emails and used numerous domains registered by Namecheap.
Supply: Guardio Labs
The menace actors might move SPF checks and ship emails by Proofpoint’s servers because of a really permissive SPF file configured on domains by the e-mail safety providers.
When configuring a website to make use of Proofpoint’s e mail gateway, the corporate gives a configuration possibility to pick out the assorted e mail providers by which you want to permit e mail to be relayed.
When Workplace 365 is chosen, a very permissive SPF file was created, permitting any Workplace 365/Microsoft 365 account to relay e mail by Proofpoint’s safe e mail service.
embrace:spf.safety.outlook.com embrace:spf-00278502.pphosted.com
On the default setting, no particular accounts or tenants might be specified. As an alternative, Proofpoint trusted any Workplace 365 IP deal with vary, which means any account might use its relay.
For DKIM, when an organization works with Proofpoint, it uploads its DKIM non-public keys to the platform in order that emails flowing by the service are correctly signed.
Because the emails now handed each the DKIM and SPF checks, they have been allowed to be delivered to inboxes with out being flagged as spam.
Guardio Labs explains that main e mail platforms similar to Gmail handled these emails as genuine, and as an alternative of sending them to folks’s spam folders, they delivered them to their inboxes.
Supply: Guardio Labs
The emails featured lures associated to the impersonated model, claiming account expirations, or renewal/cost approval requests.
Supply: Guardio Labs
Proofpoint tightens safety
In a coordinated report from Proofpoint, the corporate says they’d been monitoring this marketing campaign since March,
With the technical IOCs shared by Guardio, Proofpoint was additional in a position to mitigate these assaults and supply new settings and recommendation on the best way to stop them sooner or later.
The corporate has an in depth information on how customers can add anti-spoof checks and tighten up their e mail safety, however some organizations did not carry out any of these handbook actions to forestall abuse, permitting campaigns like EchoSpoofing to materialize.
Proofpoint reached out to clients with permissive settings to assist them safe the configuration of their accounts.
The corporate launched the ‘X-OriginatorOrg’ header to assist confirm the e-mail supply and filter out non-legitimate and unauthorized emails.
Additionally, a brand new Microsoft 365 onboarding configuration display screen permits clients to configure extra restrictive permissions on Microsoft 365 connectors. These permissions specify the Microsoft 365 tenants that may be relayed by Proofpoint’s servers.
.jpg)
Supply: Guardio Labs
Lastly, Proofpoint has notified affected clients that phishing actors efficiently abused their manufacturers in a large-scale operation.
Though Microsoft has additionally been notified in regards to the Microsoft 365 abuse, the offending accounts stay energetic, some for over seven months.
