Customers whose recordsdata had been affected by encoder trojans mostly encountered Trojan.Encoder.3953, Trojan.Encoder.35534, and Trojan.Encoder.26996.
Relating to Android cellular units, probably the most generally detected threats had been Android.HiddenAds adware trojans, Android.FakeApp malicious packages, and Android.Spy spyware and adware trojans. On the identical time, our virus analysts found extra threats on Google Play.
Principal traits in Q2 2024
- Adware trojans and undesirable adware packages had been extremely energetic
- Malicious scripts and all kinds of phishing paperwork predominated in malicious electronic mail visitors
- Android.HiddenAds adware trojans once more had been probably the most generally detected threats for Android units
In line with Physician Net’s statistics service
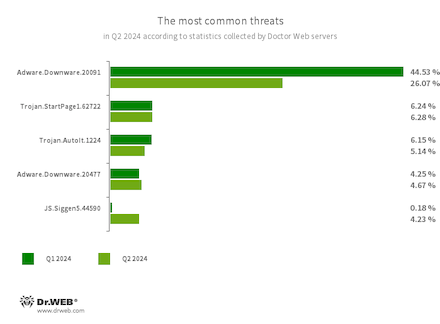
The most typical threats in Q2 2024:
- Adware.Downware.20091
- Adware.Downware.20477
- Adware that always serves as an middleman installer of pirated software program.
- Trojan.StartPage1.62722
- A trojan horse that may modify the house web page within the browser settings.
- Trojan.AutoIt.1224
- The detection identify for a packed model of the Trojan.AutoIt.289 malicious app, written within the AutoIt scripting language. This trojan is distributed as a part of a bunch of a number of malicious functions, together with a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs numerous malicious actions that make it tough for the primary payload to be detected.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It exhibits a selected message if the bundle is put in on a server with a time zone of Russian cities.
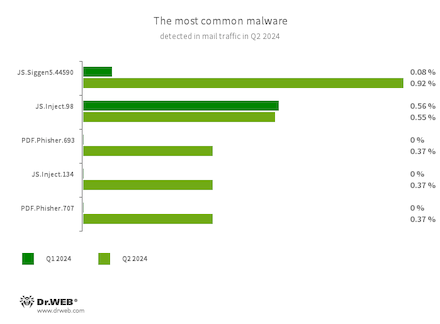
Statistics for malware found in electronic mail visitors
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It exhibits a selected message if the bundle is put in on a server with a time zone of Russian cities.
- JS.Inject
- A household of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- PDF.Phisher.707
- PDF.Phisher.693
- PDF paperwork utilized in phishing newsletters.
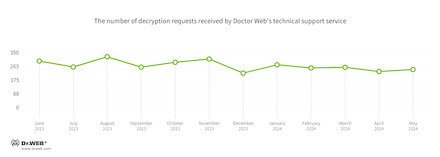
Encryption ransomware
The dynamics of the requests we obtained to decrypt recordsdata affected by encoder trojans:
The most typical encoders of Q2 2024:
- Trojan.Encoder.3953 — 18.43%
- Trojan.Encoder.35534 — 9.22%
- Trojan.Encoder.26996 — 8.75%
- Trojan.Encoder.35067 — 2.07%
- Trojan.Encoder.37369 — 1.61%
Harmful web sites
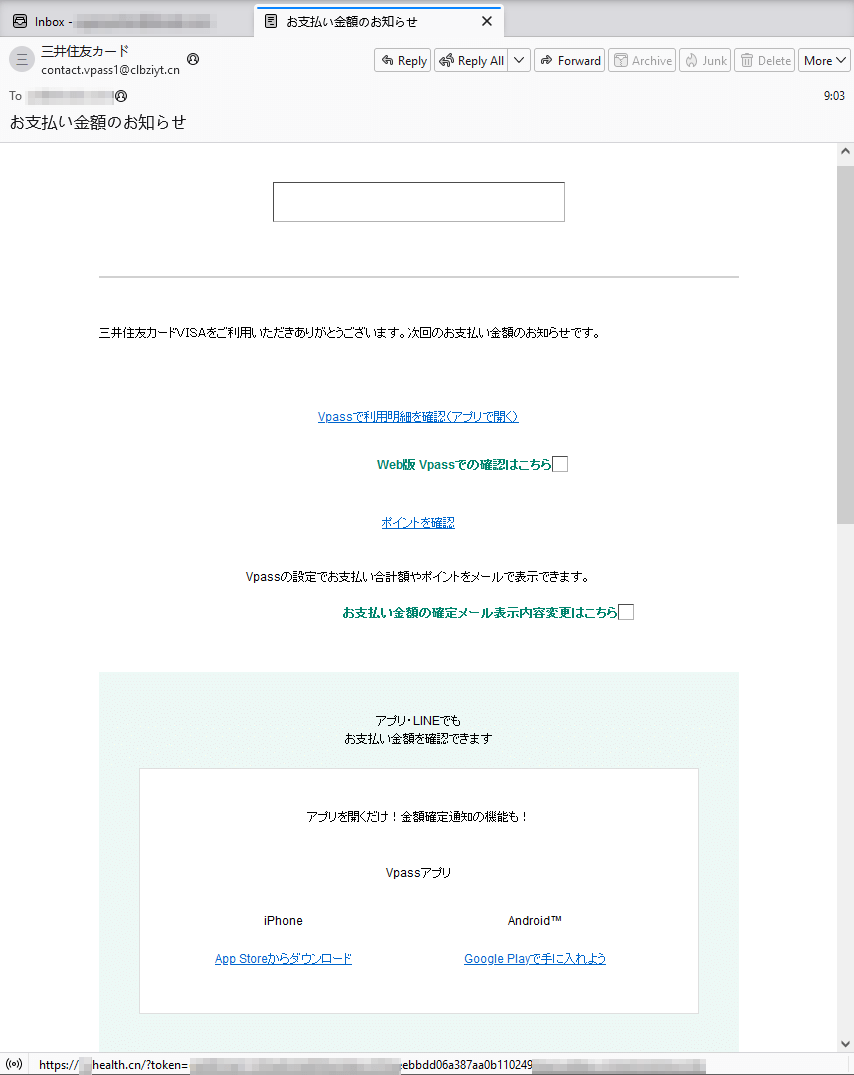
In Q2 2024, Physician Net’s specialists detected a mass-mailing fraud marketing campaign concentrating on customers from Japan. Fraudsters pretending to behave on behalf of one of many banks knowledgeable potential victims a couple of sure buy they’d made and supplied them the possibility to see the small print of this “fee” by clicking on the offered hyperlink. However, in actuality, this hyperlink led to a phishing Web useful resource.
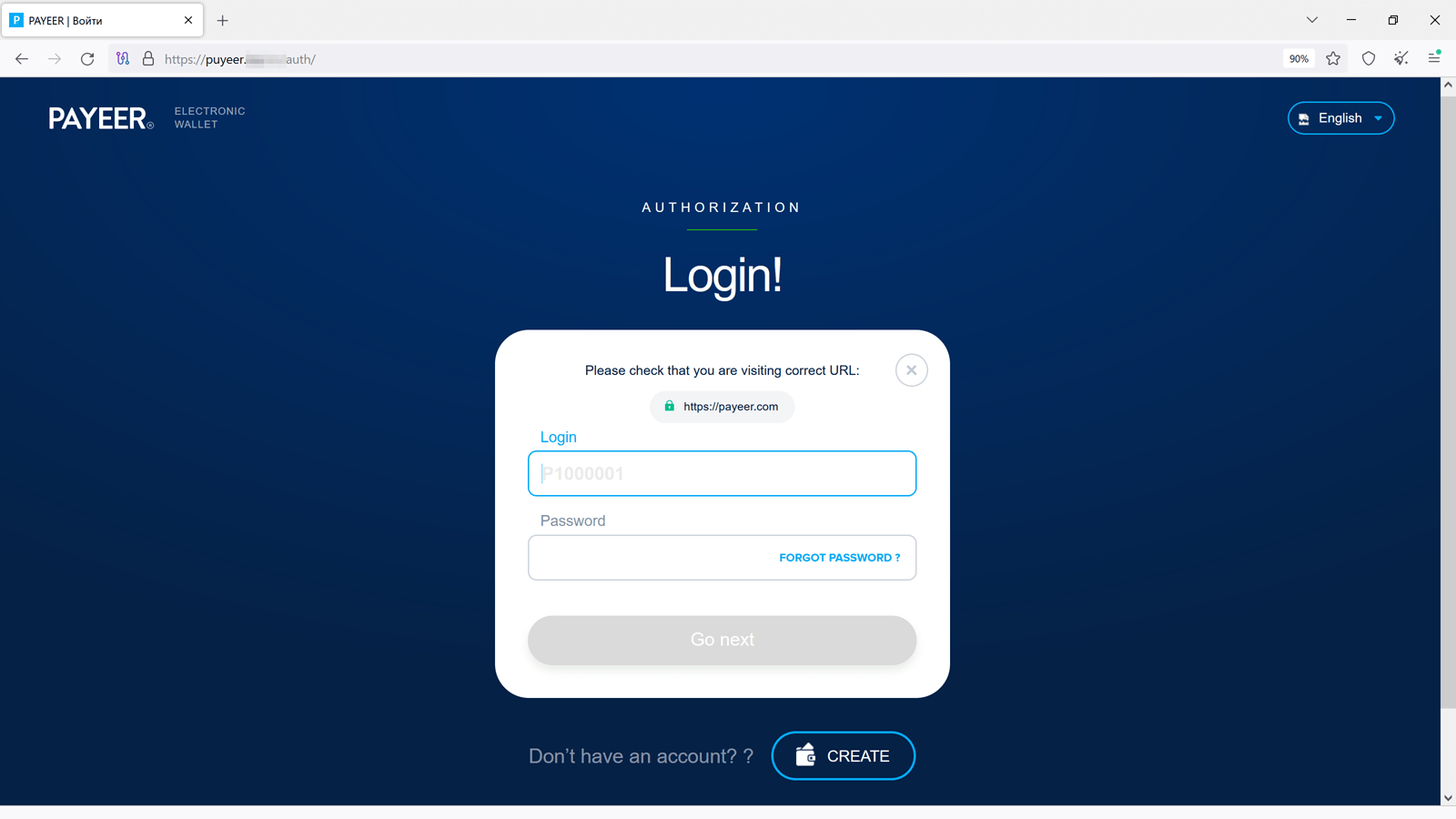
Among the many fraudulent web sites present in Q2 2024, our Web analysts additionally observed phishing assets that imitated the looks of real e-wallet websites, corresponding to Payeer. With their assist, risk actors tried to steal customers’ authentication knowledge.
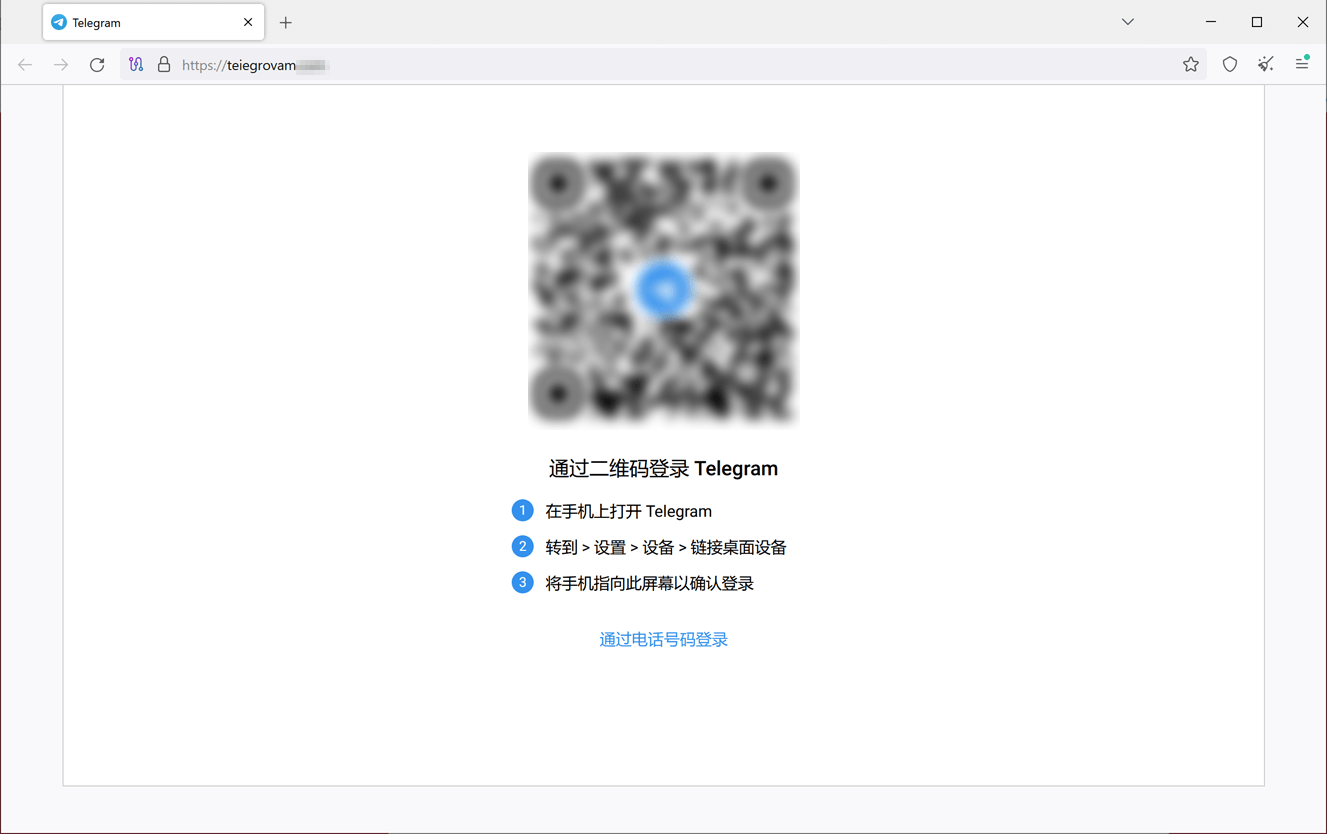
Furthermore, cybercriminals usually are not abandoning their makes an attempt to achieve entry to individuals’s accounts from numerous messengers. For this, they make the most of pretend login kinds. Beneath is an instance of 1 such phishing website the place potential victims are requested to log in to Telegram by way of a QR code or a telephone quantity. If a possible sufferer agrees, their login knowledge will find yourself within the attackers’ fingers.
On the identical time, our specialists proceed to detect fraudulent websites that concentrate on Russian-speaking customers. Amongst these, websites that supply potential victims supposedly free lottery tickets are nonetheless frequent. On such websites, potential victims are instructed that they’ll get a lottery ticket as a “present” that in the end finally ends up being a “winner”. To “obtain” the prize, victims should present their financial institution card particulars or pay some fee or customized to have the non-existent prize “transferred” to their checking account.
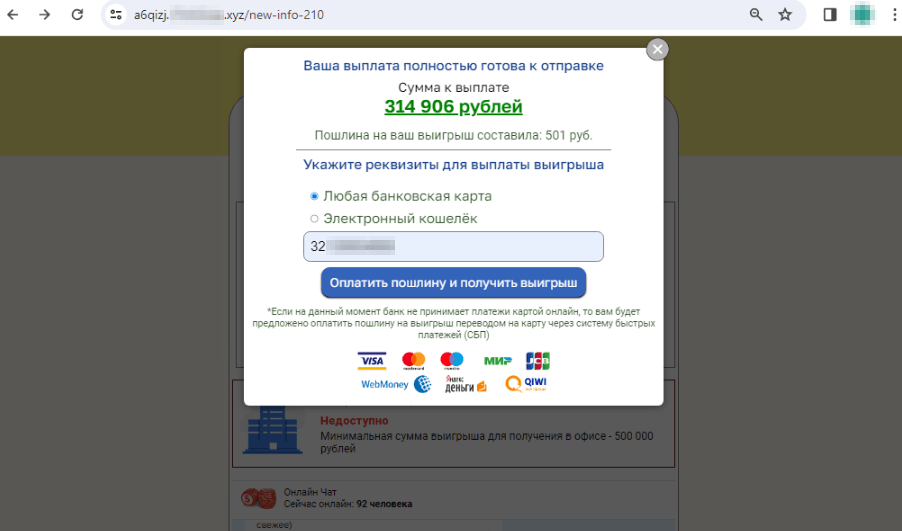
An instance of 1 such rip-off web site is proven beneath. First, it simulates “free” lottery ticket registration after which allegedly exhibits a web-based broadcast of the draw:
The consumer “wins” 314.906 rubles, however to “obtain” their winnings, they have to present financial institution card particulars and pay a “payment” of 501 rubles to have the cash “transferred”:
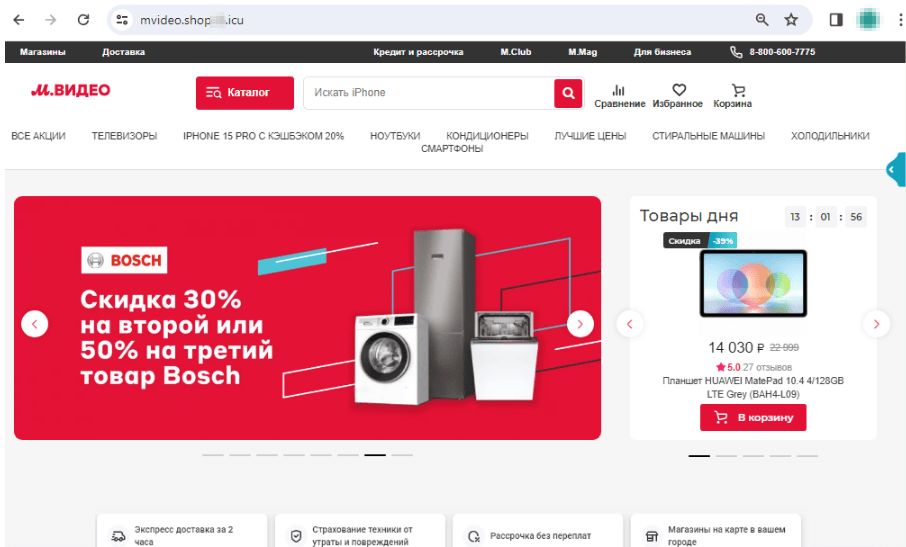
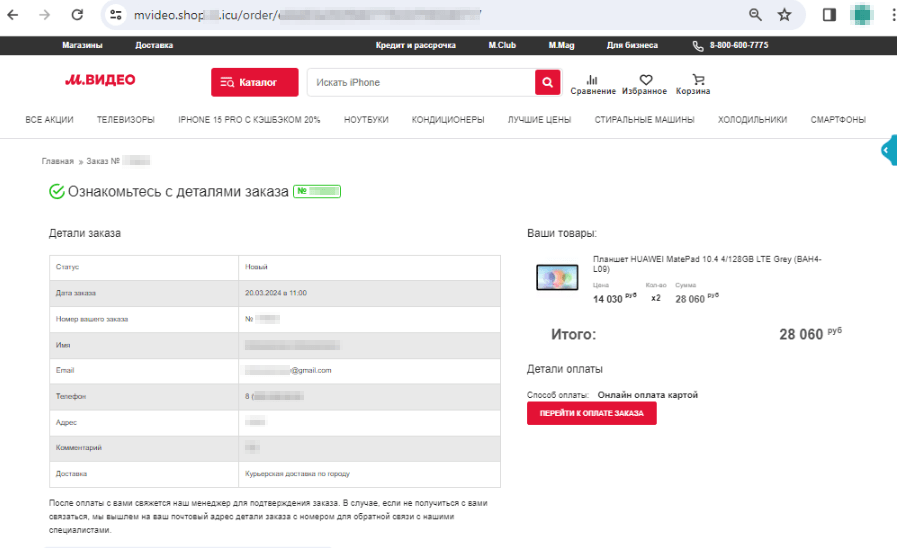
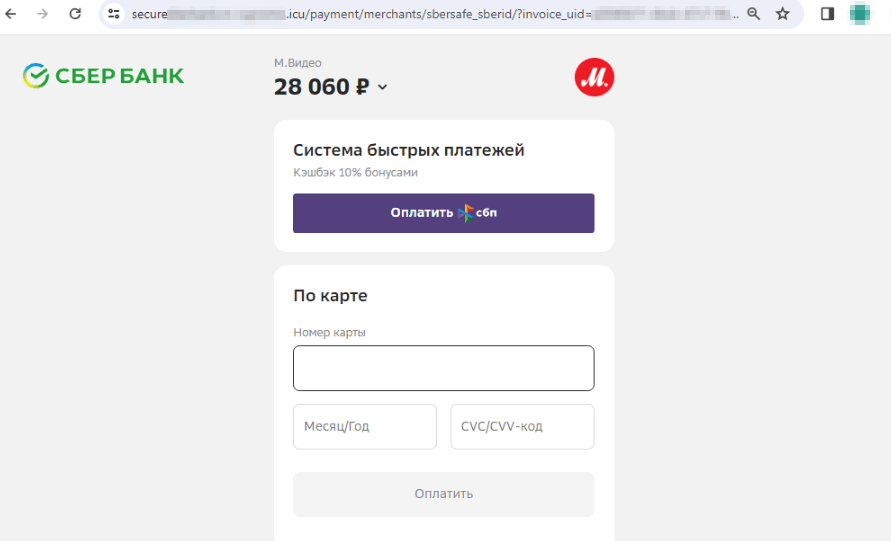
Copycat web sites of on-line shops are nonetheless one other well-liked scheme amongst scammers. These embody pretend websites of electronics and residential home equipment shops. Cybercriminals lure potential victims with “reductions”, “coupons”, and all kinds of “promotions”, providing them well-liked items on the market at decrease costs. When putting an “order” on such websites, customers are normally requested to pay by way of a web-based financial institution or a financial institution card. Nonetheless, our specialists observed that fraudsters have additionally begun together with the Quicker Funds System (“Система быстрых платежей”, “СБП”, or “SBP”) instead fee methodology.
The screenshots beneath present an instance of 1 such pretend web site that imitates an electronics retailer’s actual net useful resource:
The potential sufferer locations an order for a “product” that’s supposedly being supplied at a reduction:
The Quicker Funds System is obtainable to the consumer as one of many fee strategies for this “order”:
Malicious and undesirable packages for cellular units
In line with detection statistics collected by Dr.Net for Android, in Q2 2024, Android.HiddenAds adware trojans had been mostly detected on protected units. They had been adopted by Android.FakeApp malicious functions. The third commonest packages had been spyware and adware trojans from the Android.Spy household.
On the identical time, all kinds of threats had been once more discovered on Google Play. Amongst them had been extra Android.FakeApp trojans, an undesirable Program.FakeMoney.11 app, and likewise the Android.Harly.87 trojan, which subscribed customers to paid providers.
The next Q2 2024 occasions involving cellular malware are probably the most noteworthy:
- Android.HiddenAds adware trojans remained probably the most energetic risk,
- Extra threats had been detected on Google Play.
To search out out extra in regards to the security-threat panorama for cellular units in Q2 2024, learn our particular overview.