By Jacob Malimban
STR RAT is a distant entry trojan (RAT) written in Java that was first seen in 2020. Like different RATs, it provides risk actors full management when it’s efficiently put in onto a machine. STR RAT is able to keylogging, stealing credentials, and even delivering extra malicious payloads. The malware receives a model replace yearly, on common. These updates correlate with the renewed use of STR RAT by risk actors. Presently, 60% of the STR RAT samples that Cofense analyzed from January 2023 to April 2024 are delivered on to the e-mail versus an embedded hyperlink.
Historical past
STR RAT is sort of a seasonal flu. Yearly, some a part of the an infection chain receives an replace, and STR RAT turns into extra outstanding for a brief time period. STR RAT was first found on an antivirus discussion board publish in 2020. Already in model 1.2, it had the primary RAT options now we have come to count on: password stealing, keystroke logging, and backdoor entry. It additionally had a pretend “.crimson“ ransomware module, that solely renamed recordsdata with out encrypting them.
In 2021, Microsoft Menace Intelligence tweeted about STR RAT and its look in phishing campaigns. STR RAT began showing once more in 2022, with emails spoofing the Maersk delivery model. It additionally employed the polyglot file approach the place the malware may very well be executed as an MSI or Java file. In 2023, STR RAT reached model 1.6 and began utilizing Zelix KlassMaster together with the already applied Allatori software program. These instruments obfuscated the supply code and made it more durable for cybersecurity professionals to research the malware. Lastly in 2024, STR RAT was uploaded to professional providers like GitHub and Amazon Net Companies (AWS) in order that it may very well be downloaded by way of hyperlinks embedded in emails and clogged consumer inboxes with a vengeance.
Capabilities
Like different RATs, STR RAT is able to password stealing, keystroke logging, and backdoor entry. It will possibly steal passwords saved in Chrome, Firefox, and Web Explorer. For electronic mail shoppers, it targets Outlook, Thunderbird, and China’s Foxmail. Different instructions are proven in Desk 1.
Key instructions embrace o-keylogger, which creates a textual content file containing all subsequent textual content typed out. For RAT capabilities, there’s down-n-exec to obtain and execute a file, remote-screen for the attacker to commandeer the pc, and power-shell for a PowerShell terminal.
Desk 1: STR RAT instructions from G Information.
| reboot | power-shell | hrdp-new | ie-pass |
| shutdown | file-manager | hrdp-res | all-pass |
| uninstall | keylogger | chrome-pass | chk-priv |
| disconnect | o-keylogger | foxmail-pass | req-priv |
| down-n-exec | processes | outlook-pass | rw-encrypt |
| replace | startup-list | fox-pass | rw-decrypt |
| up-n-exec | remote-screen | tb-pass | show-msg |
| remote-cmd | rev-proxy |
Within the Wild
STR RAT has by no means been as prevalent as extra common RATs like Remcos RAT. Nonetheless, there are fascinating patterns with the frequency of STR RAT and the months from January 2023 to April 2024 as proven in Determine 1. In 2023, there’s a sustained use of STR RAT from March to August. That is possible as a result of new STR RAT replace, model 1.6, and the polyglot file approach for extra compatibility with Home windows. In March 2024, STR RAT once more seems in important numbers. This may be attributed to attackers utilizing professional providers like GitHub and AWS to host and ship STR RAT. It’s because GitHub and AWS hyperlinks seem extra professional than a website registered simply two days previous to each safe electronic mail gateways (SEGs) and recipients.
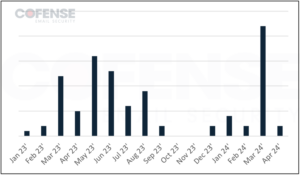

Determine 1: STR RAT lively risk report (ATR) Quantity from January 2023 to April 2024.
Supply Mechanisms
Determine 2 exhibits the supply mechanisms for STR RAT. The lion’s share is simply attaching STR RAT to the phishing electronic mail. Thus, direct attachment constitutes about 60% of Cofense’s STR RAT Energetic Menace Reviews (ATRs). Loaders are subsequent at 20%, beating URLs embedded in PDFs by 5%. The final 5% is delivered by droppers.


Determine 2: Supply Mechanisms used to ship STR RAT between January 2023 and April 2024.
Attachment
STR RAT is usually delivered in an archive connected to the e-mail. STR RAT is usually a .jar file, requiring specialised parts to run on a sufferer machine. This part is a Java Runtime Setting (JRE). Since STR RAT JAR recordsdata wants a JRE to execute, connected archive recordsdata have the potential to comprise all obligatory JRE binaries. Nevertheless, STR RAT can be identified to obtain the required recordsdata from the Maven and GitHub repositories.
Loaders
Surprisingly, STR RAT’s 2nd commonest supply mechanism is Loaders as an alternative of an embedded URL like different malware. Loaders are malware that attain out to a payload location to obtain and run the malware. STR RAT is usually loaded by Jar Downloaders. Jar Downloaders require Java to execute, however the attacker can customise or replace the payload STR RAT whereas maintaining the unique Jar Downloader malware hyperlink. A second loader is CVE-2017-11882, a generally exploited Microsoft Workplace vulnerability. When run, the Phrase or Excel doc will obtain a payload to execute. On this case, the Workplace doc runs STR RAT. A 3rd loader used is the Home windows Registry File downloader. It entails a .reg file connected to the e-mail, which installs a registry key to the pc when executed. After set up, the registry file will obtain both STR RAT or a dropper. The malicious registry key could be configured to run on each restart, gaining persistence.
Embedded URLs
Menace actors could use hyperlinks to obtain malware as an alternative of attaching malware to the e-mail in an try to bypass electronic mail safety. The sufferer recipient would click on on the hyperlink and obtain the malware unknowingly. For STR RAT, the URLs are both linked within the electronic mail or in an connected PDF. The connected PDF encourages the sufferer to click on and obtain the anticipated content material however downloads malware as an alternative. The file downloaded is both the .jar STR RAT or an archive file containing the malware.
As talked about earlier, most URLs use professional providers to host the malware. Attackers have uploaded STR RAT to AWS, GitHub, and Discord’s CDN (Content material Supply Community). The hyperlink to the malware is then embedded within the emails. For STR RAT, risk actors additionally use hyperlink shorteners to bypass electronic mail safety and conceal the file downloaded sometimes proven within the full URL.
Droppers
In contrast to loaders, droppers already comprise the malware to be deployed. A dropper file incorporates each its personal dangerous code and the ultimate malware (like STR RAT). It doesn’t want to achieve a web-based payload like a loader does. A dropper file has an anomalously bigger file dimension which hints to one thing malicious. For instance, an HTML file is normally simply kilobytes; subsequently, an HTML file that’s a number of megabytes massive is suspicious.
For STR RAT, our information present that the JavaScript Dropper (JS Dropper) is the commonest dropper. A JS Dropper is a .js file that’s natively executed on Home windows computer systems. JS Droppers are normally connected to the e-mail. Naturally, as JS Dropper incorporates each itself and STR RAT, the JS Dropper file is kind of massive.
Conduct (Capabilities)
As soon as STR RAT is executed by a JRE, it begins inserting recordsdata, creating persistence, and putting in dependencies. Some variations of STR RAT even print out debug info when operating, exhibiting profitable set up of downloaded recordsdata as proven in Determine 3.


Determine 3: Debug info from STR RAT.
One file of explicit curiosity is XXXXlock.file situated within the consumer’s native dwelling profile (C:Usersusername). The XXXX is changed with the port used to speak again to STR RAT’s command and management servers. The lock file additionally seems to forestall a number of situations of STR RAT. That is particularly helpful as this malware doesn’t sometimes delete itself and run in reminiscence like different malware.
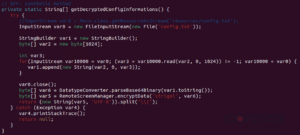

Determine 4: Most important.java in STR RAT.
A JAR is a Java Archive file that we are able to extract to get extra details about the configuration of a STR RAT pattern. Within the sources folder, there’s a base 64 encoded config.txt. The config can be encrypted utilizing AES. To decrypt, we are able to discover the passphrase “strigoi” in Most important.java. There are additionally extra particulars concerning the encryption in RemoteScreenManager.java. In Determine 5 we see {that a} PBKDF2 secret’s made utilizing that passphrase, in addition to the opposite AES decryption particulars.
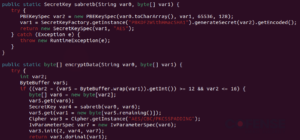

Determine 5: RemoteScreenManager.java with decryption particulars.
Within the newly created lib folder within the consumer’s native dwelling profile (C:Customers<username>), the professional recordsdata could be discovered. Be aware that these recordsdata can be present in AppData Roaming (C:Customers<username>AppDataRoaming) folder. These professional recordsdata can both be downloaded, as described within the networking part, or dropped to disk by bigger samples which have bundled the required recordsdata. JNA, or java native entry, permits straightforward use of home windows DLLs (dynamic hyperlink libraries). A software program developer or risk actor can work with Home windows libraries by simply writing Java code. SQLite JDBC (Java DataBase Connectivity) permits STR RAT to make use of SQLite as a database. Most significantly, system-hook is a “keyboard and mouse listener for Java”, as said in its GitHub web page. It’s used illegitimately in STR RAT for keylogging.


Determine 6: Downloaded recordsdata in lib.
After setup and execution, it makes use of a geolocator service. It makes use of a professional service akin to hxxp//ip-api[.]com/json/ to geo-fingerprint the contaminated laptop and can ship this and different system info to the C2 server.
Detection and Looking
There are completely different variations of STR RAT which go away completely different IOCs on disk. Listed below are some indicators to count on.
Set up
After execution, STR RAT can copy itself to a number of areas. A renamed “txt” file could be present in AppData Roaming (C:Customers<username>AppDataRoaming) and the consumer’s native dwelling profile (C:Customers<username>). These areas will even have a brand new folder, lib, containing professional recordsdata which are utilized by STR RAT. For extra info on the keylogging system-hook, see the within the Behaviors part. Lastly, there needs to be a XXXXlock.file the place XXXX is the port of the STR RAT C2, like 7888lock.file. This file will likely be within the consumer’s native dwelling profile.
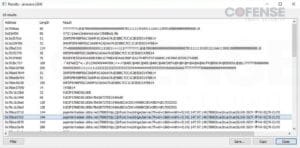

Determine 7: STR RAT configuration in reminiscence.
The configuration of STR RAT can be seen by way of reminiscence evaluation. This is identical configuration encrypted utilizing the passphrase ‘strigoi’, amongst different issues. In Determine 7, the C2 server, port, and a website related to STR RAT, jbfrost[.]stay, could be seen. The area jbfrost[.]stay was in use since STR RAT first appeared in 2020. The present whois information present the register date occurred on March 14, 2022. It’s fascinating how STR RAT makes use of each hardcoded (jbfrost[.]stay) and randomly generated C2s for communication. For the randomly generated C2s, see the Community Site visitors part.
Persistence
STR RAT can create persistence. Whether or not by Registry Run Keys / Startup Folder (MITRE T1547.001) or a Scheduled Activity/Job (MITRE T1053), the malware will run each time the consumer logs in in addition to at set time intervals. Endpoint detection and response software program can monitor the next location for STR RAT persistence.
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
- C:CustomersAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup
- C:ProgramDataMicrosoftWindowsStart MenuProgramsStartUp
- Skype in Activity Scheduler


Determine 8: ‘Skype’ scheduled activity for STR RAT persistence.
Community Site visitors
Cofense has noticed STR RAT reaching out to area identify and port mixture. The C2s are sometimes subdomains of free dynamic DNS providers, like Duck DNS. There are additionally ports mixed with pure IP deal with and not too long ago, AWS. Like different RATs, HTTP is used for C2 communications, although the port isn’t the usual tcp/80.
Reliable Companies
STR RAT additionally reaches out to professional providers. GitHub and Maven are professional websites that host professional instruments for software program improvement. Though the area of those indicators can’t be blocked, seeing an endpoint attain out to those areas in tandem with different habits is very suspicious and warrants additional investigation.
- hxxpsrepo1[.]maven[.]org/maven2/internet/java/dev/jna/jna/5[.]5[.]0/jna-5[.]5[.]0[.]jar
- hxxpsrepo1[.]maven[.]org/maven2/internet/java/dev/jna/jna-platform/5[.]5[.]0/jna-platform-5[.]5[.]0[.]jar
- hxxpsrepo1[.]maven[.]org/maven2/org/xerial/sqlite-jdbc/3[.]14[.]2[.]1/sqlite-jdbc-3[.]14[.]2[.]1[.]jar
- hxxpsgithub[.]com/kristian/system-hook/releases/obtain/3[.]5/system-hook-3[.]5[.]jar
- hxxpip-api[.]com/json/