Present in Environments Protected By: Microsoft
By Andrew Mann, Cofense Phishing Protection Middle
Everybody in the present day has some type of social media, whether or not it’s Instagram, X, YouTube or Fb. It’s an incredible strategy to talk and keep related with household and buddies, however on the similar time, it may be scary when your social media falls sufferer to a cyber-attack.
Most of these campaigns illustrate how safe e-mail gateways (SEGs), or any sort of automated system, could fail to catch issues that solely the skilled eye can. Risk analysts right here on the Cofense Phishing Protection Middle (PDC) are correctly skilled and outfitted to catch these phishing campaigns which have proven up in environments using SEGs.
Right here on the PDC, we now have seen quite a few social media phishing web sites, starting from X, Instagram, Telegram, Snapchat and Fb. These assaults can purpose to gather your username and password by sending an e-mail saying that “your password must be up to date” or “your account goes to be deleted. Click on right here to keep away from termination!”
These phish can already be very possible and tempting to the untrained eye, and even with that, the risk actor did a commendable job at tailoring this phish to appear to be a legit Fb/Meta account termination e-mail. They have been in a position to do that partially as a result of they used Meta’s Enterprise Supervisor service which helped make the e-mail appear extra actual. Receiving emails like these may be scary while you don’t know in case your account is underneath hearth. It’s at all times finest apply to maintain a relaxed thoughts and never rush to click on something within the e-mail in case you are not sure.
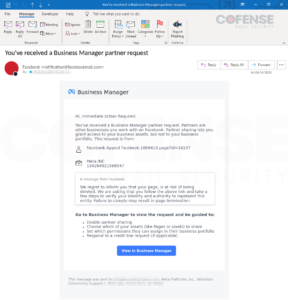

Determine 1: Electronic mail Physique
Within the above picture you’ll be able to see format of the physique is nicely completed, the grammar is appropriate {and professional}, they usually included a singular case quantity for this particular account requisition. In addition they included some informative help to assist information the consumer to the request made.
One indicator of suspicious exercise, is that they began out the e-mail as “Hello, Quick Motion Required.” The risk actor used a easy scare/urgency tactic to make the consumer suppose if they don’t observe these steps straight away, their account will likely be deleted. A highly regarded tactic to make use of amongst these kind of social media phishing emails.
Usually, the massive blue button would take us to the phishing web site if clicked on. Nonetheless, on this case, it doesn’t, which is one the explanations this a singular phishing e-mail. As a substitute, they offered the phishing URL above within the portion of the e-mail itemizing who made the Enterprise Supervisor request.
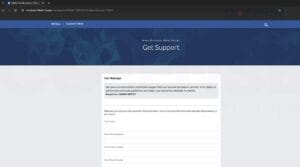

Determine 2: Phishing Web page
After going to the above hyperlink, the risk actor put of their tailor-made e-mail, it redirects to the phishing web site. It’s a very customary Fb/Meta phishing webpage, they usually even put a observe on the high saying “your account has been in violation of our phrases of service and neighborhood pointers.”
A last threatening reminder to persuade the consumer to offer their username and password. A naïve perspective may miss the plain implications that this web site is faux. Some frequent pointers are that if it was Fb, the URL deal with can be an actual Meta/Fb area similar to fb[.]com and never fb[.]1006615[.]web page. The risk actor tried to make a superb try by not less than together with the identify Fb within the subdomain.
At all times be cautious of the threats cyber-criminals can pose. They’re after something and every little thing that may be held in opposition to a consumer. Starting from credit-card data, Social Safety numbers, or your login credentials, they’ll use what they will to not simply entry your social media account however to any on-line account you might have.
All third-party logos referenced by Cofense whether or not in brand kind, identify kind or product kind, or in any other case, stay the property of their respective holders, and use of those logos on no account signifies any relationship between Cofense and the holders of the logos. Any observations contained on this weblog concerning circumvention of finish level protections are primarily based on observations at a cut-off date primarily based on a selected set of system configurations. Subsequent updates or completely different configurations could also be efficient at stopping these or related threats. Previous efficiency shouldn’t be indicative of future outcomes.
The Cofense® and PhishMe® names and logos, in addition to every other Cofense services or products names or logos displayed on this weblog are registered logos or logos of Cofense Inc.