E mail safety instruments akin to Safe E mail Gateways (SEGs) usually encode URLs which can be embedded in emails. This permits the safety equipment to scan the URL earlier than the recipient visits the web site. Oftentimes when SEGs detect URLs in emails which can be already SEG encoded they don’t scan the URLs, or the scanning reveals solely the safety software’s scanning web page and never the precise vacation spot. Consequently, when an e-mail already has SEG encoded URLs the recipient’s SEG usually permits the e-mail by way of with out correctly checking the embedded URLs. Risk actors have abused this for a while, however Q2 of this 12 months, and Could particularly, noticed a rise in menace actors making the most of SEG encoding malicious URLs earlier than sending them to victims.
Instruments Utilized in The Wild
The 4 instruments mostly seen in use by menace actors to encode URLs and bypass SEGs in Q2 2024 are VIPRE E mail Safety, BitDefender LinkScan, Hornet Safety Superior Risk Safety URL Rewriting, and Barracuda E mail Gateway Protection Hyperlink Safety. E mail campaigns utilizing these instruments to bypass SEGs have been seen in environments protected by all the pieces from Proofpoint to Microsoft ATP.
VIPRE E mail Safety
URLs encoded by VIPRE E mail Safety, particularly URLs encoded by url[.]emailprotection[.]hyperlink had been seen with 12 distinctive topics in early June 2024. These emails had topics just like the next subset:
| Widespread E mail Topics |
| Overview & Signal: Partnership_Investment_Proposal.DOCX |
| New Contract and Termination Settlement.pdf |
| You’ve got a brand new encrypted VM from <recipient title or identifiable info> |
| Full: Increment Coverage and Customary Termination Settlement.pdf. |
| Wage Compensation Report 2024 |
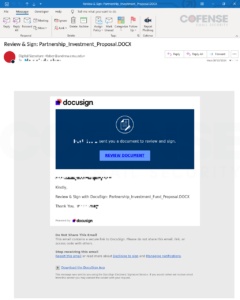

Determine 1: E mail with embedded URL encoded by VIPRE E mail Safety’s url[.]emailprotection[.]hyperlink.
URLs encoded with VIPRE E mail Safety’s different encoding URLs: url2[.]mailanyone[.]web, url10[.]mailanyone[.]web, url12[.]mailanyone[.]web, and so on. had been seen primarily in Could of 2024 with over 200 distinctive topics. These emails had topics just like the next subset:
| Widespread E mail Topics |
| 7167-<recipient title or identifiable info>: Settle for the proposal and return |
| One Time Authentication Immediate |
| Notification Entry #27 -Could 15, 2024, 07:49:27 AM |
| 8533-<recipient title or identifiable info>: Signal and Return to course of |
| <recipient title or identifiable info> Termination Settlement……623.docx |


Determine 2: E mail with embedded URL encoded by VIPRE E mail Safety’s url10[.]mailanyone[.]web.
BitDefender LinkScan
URLs encoded by BitDefender LinkScan, particularly URLs encoded by lsems[.]gravityzone[.]bitdefender[.]com had been seen most frequently in early June 2024 with 8 distinctive topics. These emails had topics just like the next subset:
| Widespread E mail Topics |
| Pressing Motion Required: Safe E mail Alert !!! |
| Oops, We Withheld Some Messages From you June 09 Case- #UMMQEGA7 |
| <recipient title or identifiable info> e-Safe/e-File/0B6UCG Tuesday, June 11, 2024 |
| Timesheet Replace Notification: View Ref-VJ7N8GO012P modifications made to your timesheet |
| Report Ticket 0168724 For <recipient title or identifiable info> |
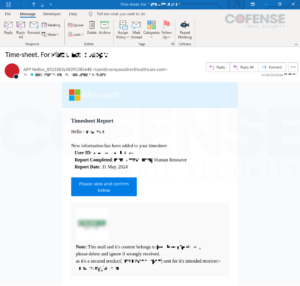

Determine 3: E mail with embedded URL encoded by BitDefender LinkScan’s lsems[.]gravityzone[.]bitdefender[.]com.
URLs encoded with BitDefender LinkScan’s different encoding URL, linkscan[.]io, had been solely seen in two campaigns in June of 2024. These emails had topics just like the next subset:
| Widespread E mail Topics |
| Speedy Motion Required: Mail Server Error – Replace Entry on Tuesday 11/Jun/2024 – TicketID: LCCP-YLSNYA-FLLWK |
| Time-sheet For <recipient title or identifiable info> |
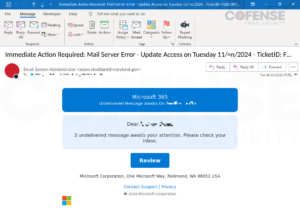

Determine 4: E mail with embedded URL encoded by BitDefender LinkScan’s linkscan[.]io.
Hornet Safety Superior Risk Safety URL Rewriting
URLs encoded with Hornet Safety Superior Risk Safety URL Rewriting (seclinks[.]cloud-security[.]web) had been seen primarily in late Could and early June of 2024 with 8 distinctive topics. These emails had topics just like the next subset:
| Widespread E mail Topics |
| PVX #5LOA: Full: Please Signal&Return #Ref-D786DYY37B(2) |
| Oops, We Withheld Some Messages From you June 09 Case- #UMMQEGA7 |
| <recipient title or identifiable info> e-Safe/e-File/0B6UCG Tuesday, June 11, 2024 |
| Timesheet Replace Notification: View Ref-VJ7N8GO012P modifications made to your timesheet |
| Time-sheet Submission: Please affirm your new time-sheet |


Determine 5: E mail with embedded URL encoded by Hornet Safety Superior Risk Safety URL Rewriting’s seclinks[.]cloud-security[.]web.
URLs encoded with Hornet Safety Superior Risk Safety URL Rewriting’s different encoding URL, atpscan[.]international[.]hornetsecurity[.]com, had been solely seen in campaigns in late Could and early June of 2024 with 16 distinctive topics. These emails had topics just like the next subset:
| Widespread E mail Topics |
| Accepted for less than 83574 – <recipient title or identifiable info> |
| #0IU6IB Overview Monday, June 10, 2024 |
| YV8 72Q: Signal&Return #Ref-JB0UOYAY19P |
| 4700-27Z Please full: Signal&Return #Ref-04020427Z |
| Motion Required: We witheld 9 messages from you. |


Determine 6: E mail with embedded URL encoded by Hornet Safety Superior Risk Safety URL Rewriting’s atpscan[.]international[.]hornetsecurity[.]com.
Barracuda E mail Gateway Protection Hyperlink Safety
URLs encoded by Barracuda E mail Gateway Protection Hyperlink Safety, particularly URLs encoded by linkprotect[.]cudasvc[.]com had been seen with 19 distinctive topics in Q2 2024. These emails had topics just like the next subset:
| Widespread E mail Topics |
| #23321041 |
| Your DocXXX Await Your Approval Ref:#ezgyo4r |
| Complete Wellness Program for <recipient title or identifiable info> Workers |
| Your DocXXX Await Your Approval Ref:#hlufnew |
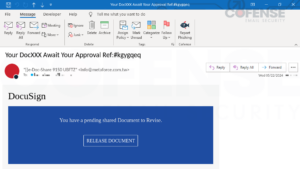

Determine 7: E mail with embedded URL encoded by Barracuda E mail Gateway Protection Hyperlink Safety’s linkprotect[.]cudasvc[.]com.
Varieties Of Campaigns Seen Utilizing SEG Encoded URLs
There have been many several types of campaigns making use of SEG encoded URLs in Q2. A few of the most typical themes had been content material requiring a signature and voicemail or withheld e-mail notifications. As might be seen from the above Figures, DocuSign and Microsoft had been usually spoofed.
DocuSign
Numerous campaigns themed round content material requiring a signature spoofed DocuSign. Regardless of this spoofing, comparatively few of the campaigns made use of an precise DocuSign hyperlink which isn’t unusual amongst Credential Phishing emails spoofing DocuSign. That is doubtless as a result of the DocuSign hyperlinks are usually used to bypass SEGs and if the menace actor is already bypassing a SEG by encoding the malicious URL then they haven’t any want for an additional step that may get taken down.
Microsoft
Second solely to DocuSign, Microsoft was essentially the most generally spoofed model in e-mail campaigns making use of SEG encoded URLs in Q2 2024. Though not all of the Microsoft spoofing made sense, for instance, the Microsoft spoofing Time Sheet Report in Determine 3, it was nonetheless generally seen. It is a widespread tactic for menace actors searching for to abuse victims’ inherent belief in well-known manufacturers.